TL;DR
- A Web Application Firewall (WAF) protects websites and applications by filtering, monitoring, and blocking malicious HTTP/S traffic.
- WAFs defend against threats like SQL injection, XSS, and bots—essential for modern web security and compliance.
- They’re widely used to protect APIs, customer data, and application performance at the edge.
Why Protecting the Client Side Matters
Protecting client-side web applications and websites is a critical goal shared by both the application development and cybersecurity teams.
Web application vulnerabilities are among the most common attack vectors. However, there’s still confusion over who owns client-side security:
- Is it the security team’s responsibility?
- Or does it fall on application developers?
As application security shifts left, the answer is: both teams must collaborate.
To effectively secure the client side—especially against threats like:
- E-skimming
- Magecart attacks
- Formjacking
- Other client-side exploits
—security must be integrated earlier in the software development lifecycle (SDLC).
5 Tools for Client-Side Web Application Security
Protecting the client side—what users see and interact with in their browser—is critical to preventing modern cyberattacks like formjacking, e-skimming, and Magecart. These threats operate in real-time, directly in the user’s browser, often by exploiting third-party JavaScript or injecting malicious scripts.
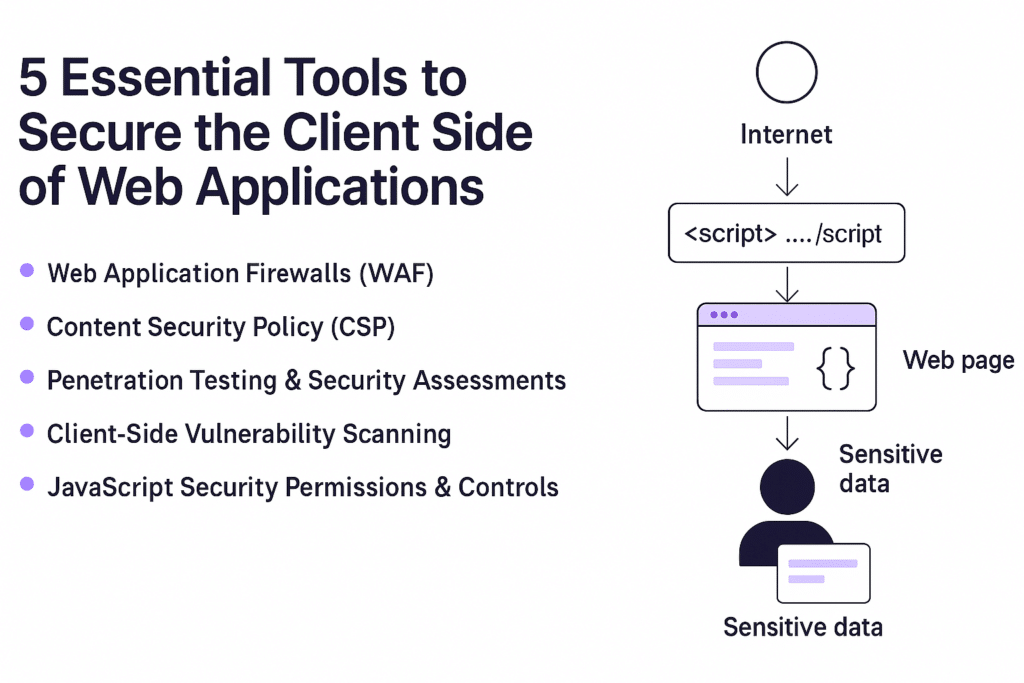
To defend against these threats, organizations use a combination of technologies and practices. Here are the five most important tools:
Web Application Firewalls (WAF)
A WAF filters and monitors incoming HTTP/S traffic between the internet and a web application. It blocks known malicious payloads like SQL injection, XSS, and bot traffic before they reach the backend.
- Strengths: Blocks perimeter threats, easy to deploy (especially cloud WAFs), supports compliance (e.g., PCI DSS).
- Limitations: Cannot inspect what happens inside the browser or detect threats from trusted third-party scripts.
Content Security Policy (CSP)
CSP is a browser-native security mechanism that helps prevent code injection attacks by controlling which scripts, styles, and resources can load on a webpage.
- Strengths: Enforces a “whitelist” of approved content sources. Helps mitigate XSS attacks.
- Limitations: Complex to configure and maintain. Difficult to enforce consistently on dynamic applications or large script libraries.
Penetration Testing & Security Assessments
These tests simulate real-world attacks to uncover vulnerabilities before attackers do. They include manual testing and automated scans to identify misconfigurations, insecure code, and logic flaws.
- Strengths: Identifies both known and unknown vulnerabilities. Helps prioritize risk remediation.
- Limitations: Point-in-time only—doesn’t offer continuous protection. May miss client-side JavaScript behavior that only executes under user interaction.
Client-Side Vulnerability Scanning
Unlike traditional scanners, client-side scanners focus on what actually runs in the browser. These tools identify suspicious or malicious behavior in third-party scripts, tag managers, and runtime DOM manipulations.
- Strengths: Visibility into real-time execution of scripts. Detects unauthorized changes to forms, cookies, and DOM elements.
- Limitations: Newer technology. May require integration with CI/CD workflows for continuous visibility.
JavaScript Security Permissions & Controls
These tools help enforce granular control over what JavaScript code can do in the browser—such as accessing forms, network calls, or sensitive input fields. Some advanced platforms allow “allowlisting” behavior or tagging scripts based on risk.
- Strengths: Enforces least privilege for scripts. Helps prevent data leakage and script abuse.
- Limitations: Requires behavioral analysis and accurate baselining of script behavior.
What is a Web Application Firewall?
A Web Application Firewall is a security tool that inspects and filters traffic between a web application and the internet. Its goal is to detect and block malicious requests before they reach your application backend. It protects web applications from attacks, such as cross-site forgery, cross-site-scripting (XSS), and SQL injection. WAFs are deployed in front of web applications and analyze bi-directional web-based (HTTP) traffic, detecting and blocking anything malicious. They are great tools to use when protecting your business from skimming attacks, but they can only do so much. Think of it as a bouncer for your website—screening every visitor and only letting the safe ones through.
WAFs use a combination of:
- Rule-based logic (blacklists and whitelists)
- Behavioral analysis
- Machine learning (in some advanced WAFs)
They block attacks such as:
- SQL Injection
- Cross-site Scripting (XSS)
- Cookie poisoning
- Remote file inclusion (RFI)
- Distributed Denial-of-Service (DDoS)
- Malicious bot traffic
What WAF limitations do I need to be aware of?
WAFs are a special category of firewall that are designed specifically to protect web applications and your business from falling victim to skimming attacks.
According to the Payment Card Industry Data Security Standards (PCI-DSS), a WAF sits between a web application and the client endpoint and serves as a security policy enforcement point.
Web application firewalls protect web applications from attacks, such as cross-site forgery, cross-site-scripting (XSS), file inclusion, and SQL injection.
However, WAFs are an open systems interconnection (OSI) layer 7 defense mechanism against application-layer attacks. They protect services that user-facing web applications apply to collect, store, and utilize data. WAFs are not designed to protect the browser-level user interface itself.
WAFs cannot protect businesses or their customers from:
- Sophisticated Skimming Malware
- WAFs are not able to detect and protect businesses from more sophisticated skimming malware.
- Drive-by Skimming and Supply Chain Attacks
- WAFs are unable to detect manipulated JavaScript code or data exfiltration.
- Sideloading and Chainloading Attacks
- WAFs do not protect against skimming performed by a sideloaded JavaScript code.
Web Application Firewalls (WAFs) Use Cases & Benefits
WAFs are widely deployed to secure modern web environments. Common use cases include:
- Protecting eCommerce platforms from input-based attacks
- Blocking malicious bots from scraping or brute-forcing logins
- Securing APIs exposed to third-party clients
- Maintaining PCI DSS compliance (e.g., requirement 6.6 for app-layer protection)
- Reducing attack surface for web-based zero-day exploits
Benefits of using a WAF:
- Real-time threat detection
- Improved visibility into traffic
- Protection without altering app code
- Supports zero trust and layered defense models
To learn more about WAF’s and best-practices to improve your client-side security, check out our white paper.
Next Steps
Implementing effective client-side security is crucial to ensure the safety of your customer data, the integrity of your user experience, the functionality of your web applications and websites, and the ability for your business to grow and succeed. If you are on the long arduous journey to build a client-side security program, check out our blog over the coming weeks as we cover the remaining four client-side security approaches, CSP, pentesting & assessments, client-side vulnerability scanning, and JavaScript security permissions.
FAQ
What is the main purpose of a web application firewall?
To protect web applications from common threats by filtering and analyzing incoming traffic based on security rules.
How is a WAF different from a traditional firewall?
Traditional firewalls block unauthorized network access. WAFs specialize in inspecting HTTP/S traffic to protect web applications from specific exploits like XSS or SQLi.
Is a WAF required for compliance?
Yes—standards like PCI DSS require WAFs or equivalent measures for public-facing web applications.
Can a WAF stop JavaScript-based attacks?
No, WAFs generally can’t detect client-side attacks like formjacking. You need dedicated client-side protection for that.
Are cloud WAFs secure?
Yes, most are highly secure and maintained by leading providers. However, trust and compliance depend on your use case and vendor.


