Simplify Your Website Security and Compliance
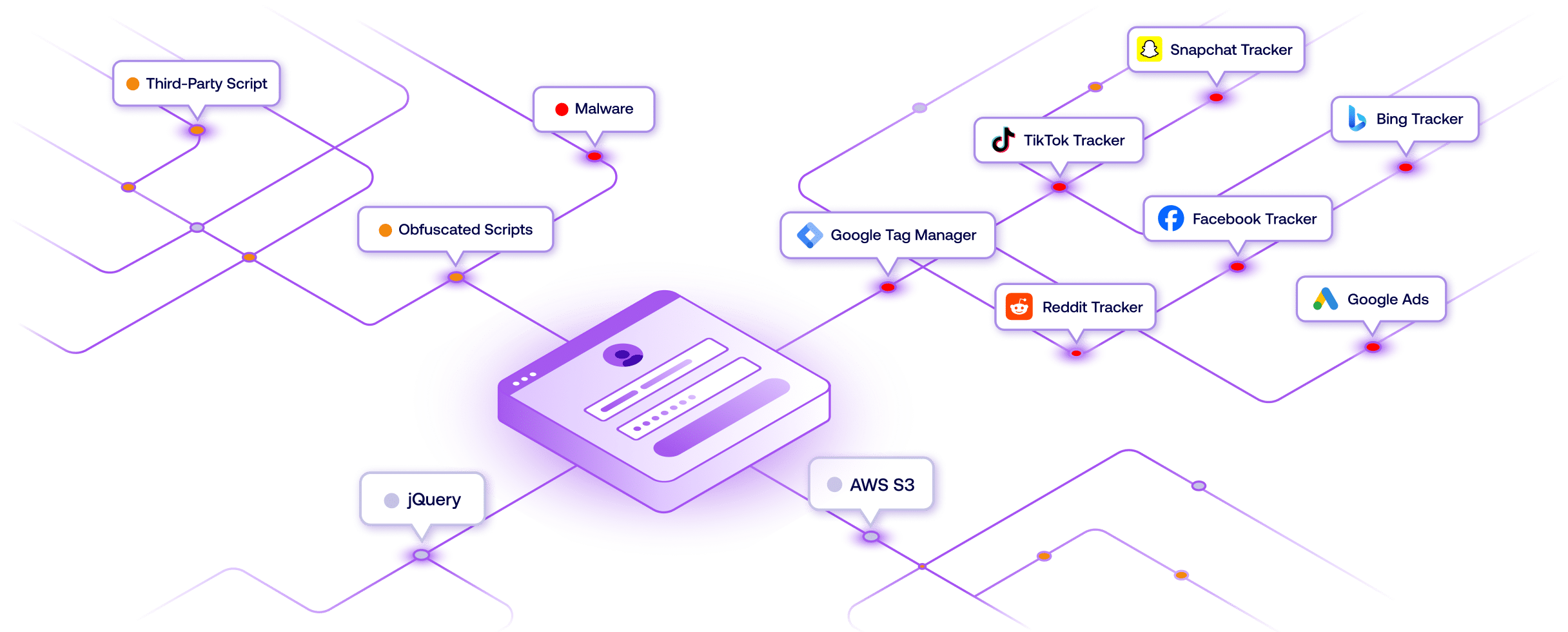
Modern websites rely on numerous third-party components and scripts that can change behavior at any time. Traditional security tools can’t detect these dynamic changes, leaving gaps in your security and compliance programs.
- Complex Third-Party Dependencies
- Dynamic Script Behavior Changes
- Hidden Data Collection Activities
- Multi-Jurisdiction Compliance Requirements
- User Privacy Protection Needs
- Supply Chain Security Risks
Why companies trust Feroot
“Feroot Inspector gave us immediate visibility into our website security risks without requiring any deployment or configuration. The automated scanning and analysis saved us countless hours while improving our security posture.”


FREE DOWNLOAD:
Get the Website Security Automation Guide
Learn how automated external scanning can simplify your website security and compliance programs.