HIPAA compliance alert: Avoid breaches from online trackers on health websites.



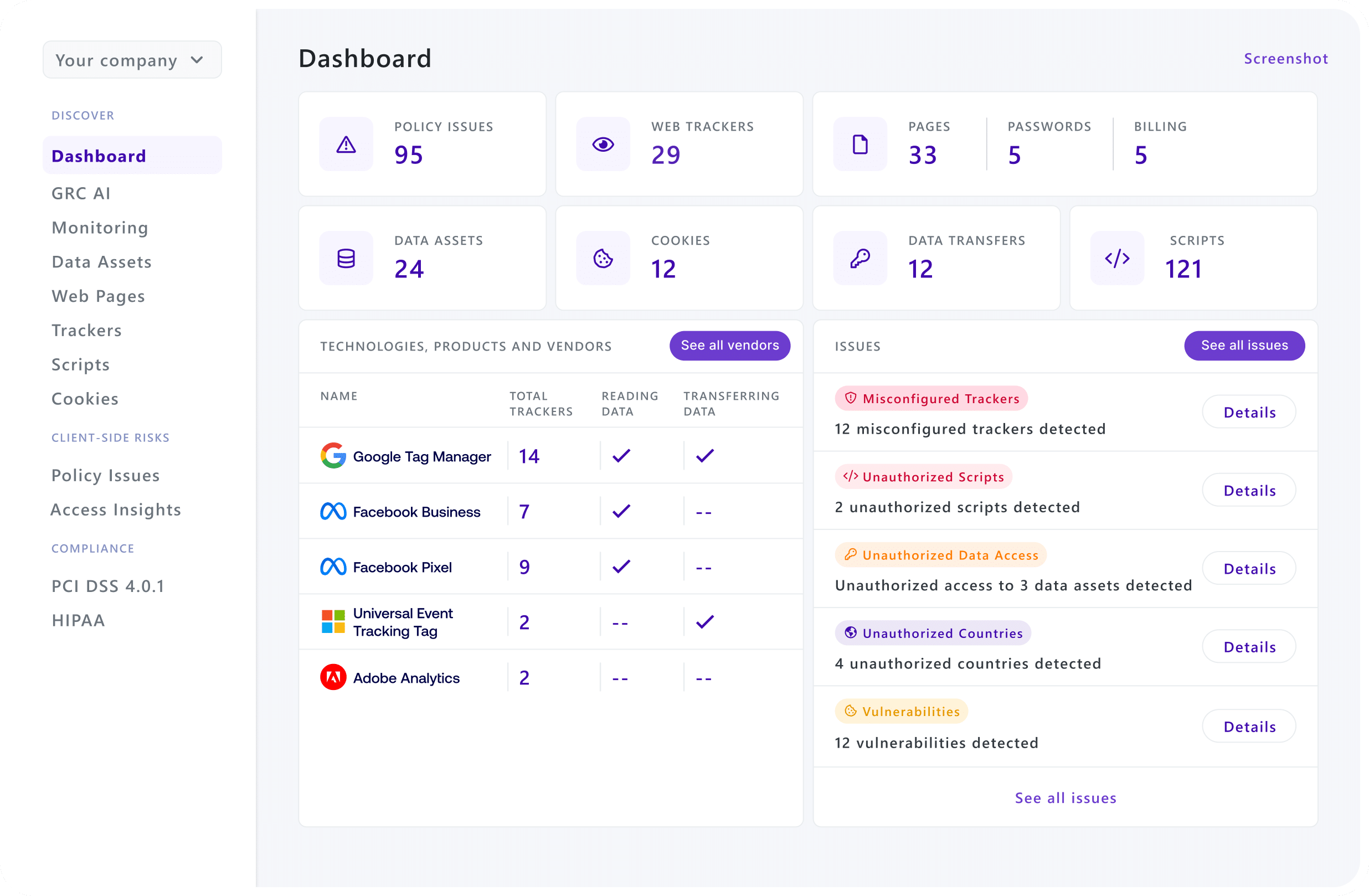
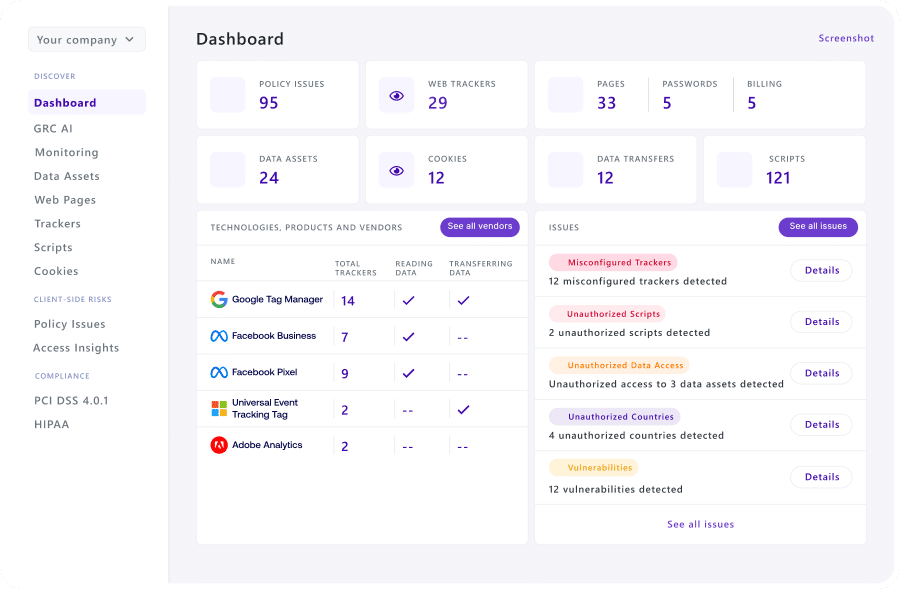
Feroot AI takes the burden off your plate with automated compliance that runs quietly in the background.
We’re on a mission to secure half a billion web pages by 2028 – including yours.

“A day doesn’t go by that you don’t hear about a new JavaScript-based attack on a company’s website or web application. We’re seeing attackers pivoting from traditional server-side attacks to client-side attacks. To protect our business from server-side threats, we needed to enhance our client-side security capabilities to stay ahead of the threat.”




