TL;DR
- Cross-site scripting (XSS) is a web security vulnerability that lets attackers inject malicious scripts into trusted websites. These scripts execute in the browser, giving threat actors access to cookies, session tokens, or sensitive data.
- XSS is dangerous because it compromises client-side environments and bypasses traditional server-side security tools.
- XSS allows malicious scripts to run in a user’s browser, often stealing sensitive data like session tokens and cookies from trusted websites.
Introduction
Who this guide is for:
Web developers, security professionals, compliance officers, and IT teams working on web applications or handling sensitive user data.
Why it matters:
Cross-site scripting (XSS) is one of the most common and dangerous client-side attack vectors. It affects millions of users and organizations, especially those in finance, healthcare, retail, and SaaS sectors.
What this article covers:
- What XSS is and how it works
- Real-world examples and attack types
- Industries and individuals most impacted
- Best practices for prevention and defense
- FAQ and next steps
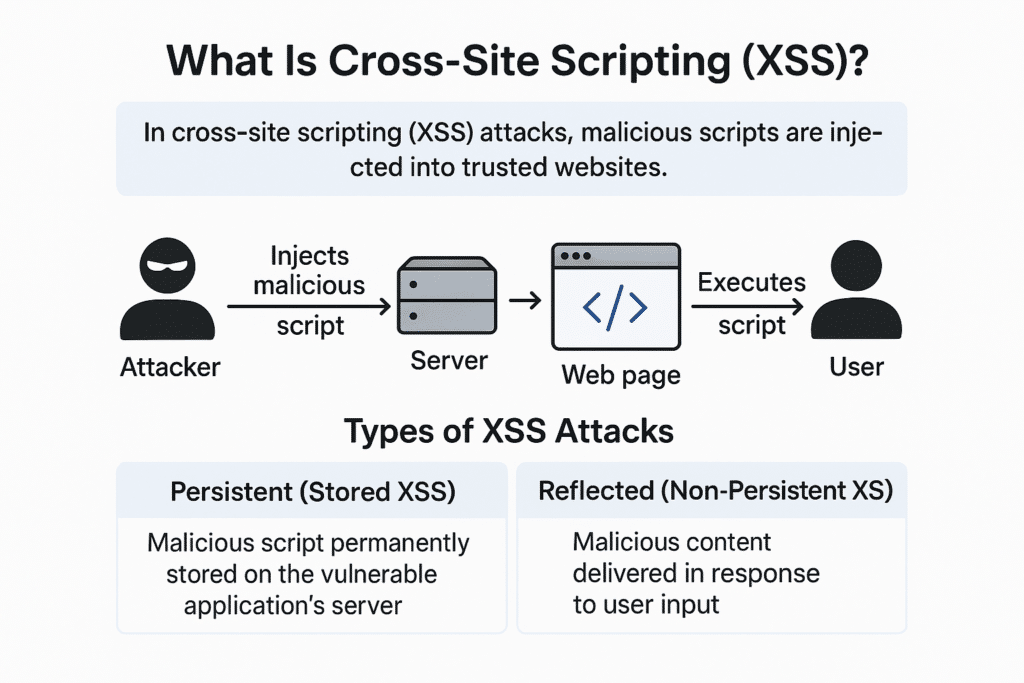
How Cross-Site Scripting (XSS) Works
XSS attacks exploit browser behavior—browsers trust content from a server, even if it includes malicious code. When a web app fails to properly validate or encode user input, attackers can inject scripts that run in the victim’s browser.
Typical XSS Attack Flow:
- Attacker injects malicious JavaScript into a webpage (via form, URL, etc.).
- The server stores or reflects the script in a response.
- User visits the compromised page or clicks a malicious link.
- Browser executes the injected script.
- Script steals data, impersonates the user, or redirects traffic.
- Data is sent back to the attacker’s server.
Types of Cross-Site Scripting Attacks
XSS comes in several forms, depending on how and where the script is injected:
1. Persistent (Stored XSS):
- Malicious code is permanently stored in a server-side database or application component.
- Triggered whenever a user loads the infected page (e.g., via a comment field or message board).
- Example: Injected code in a public forum post that steals login credentials.
2. Reflected XSS:
- Delivered through a URL or form that reflects user input back in the server response.
- Often used in phishing attacks or malicious links.
- Example: A crafted search URL returns a page displaying the attacker’s script.
3. DOM-Based XSS:
- Occurs entirely in the client browser’s DOM, without server interaction.
- Manipulates the page’s JavaScript environment.
- Example: A script dynamically reads URL fragments and injects HTML directly.
4. Blind XSS:
- Like stored XSS, but the malicious payload executes in an admin or backend interface.
- The attacker never sees the immediate result but gets data later.
- Example: Attack embedded in a support form visible only to an internal team.
Who Is Targeted by Cross-Site Scripting (XSS) Attacks?
XSS vulnerabilities target any website that accepts user input, especially those with large user bases or sensitive data collection.
High-Risk Industries:
- Finance & Banking
- Healthcare & Insurance
- E-commerce & Retail
- SaaS Platforms
- Travel & Hospitality
- Cryptocurrency & Blockchain
Commonly Impacted Roles:
- Remote employees: Cross-Site Scripting (XSS) can steal login credentials and PHI.
- Consumers: Attacks may harvest credit card details or personal information.
- Business customers: Breaches at app providers can leak sensitive B2B data.
- Web development firms: Client-side attacks target frontend code, especially JavaScript-heavy apps.
How to Prevent and Mitigate Cross-Site Scripting (XSS) Attacks
Traditional server-side tools aren’t enough—Cross-Site Scripting (XSS) is a client-side threat. Proactive defense requires a layered approach and developer awareness.
Best Practices for XSS Prevention:
- DevSecOps culture: Integrate security in every phase of development.
- Automated client-side attack surface monitoring tools.
- Content Security Policy (CSP): Use allowlists to control script sources.
- Sanitize HTML inputs: Avoid unsafe tags and attributes.
- Output encoding libraries: Prevent JavaScript injection via templates.
- Avoid unsafe JavaScript calls: e.g., innerHTML, document.write(), eval().
- Automated code scanning and crawling to detect unauthorized scripts.
- Secure JavaScript event handlers and callback functions.
For detailed developer guidance, see the OWASP XSS Prevention Cheat Sheet.
FAQ
What is the difference between stored and reflected XSS?
Stored XSS saves the script on the server and affects all users. Reflected XSS only affects the user who clicks a crafted link or submits a specific request.
Can traditional firewalls stop XSS?
No. Since XSS is executed on the client side, traditional server-side firewalls and antivirus tools are ineffective.
What’s an example of DOM-based XSS?
A page that reads a query string (?msg=hi) and injects it into the HTML without sanitization, like document.write(location.search), is vulnerable to DOM-based XSS.
Who is responsible for fixing XSS?
Primarily the web development team, but security engineers and DevOps professionals must enforce policies and controls.
Is XSS still a common vulnerability?
Yes. Cross-Site Scripting (XSS) vulnerabilities remain in the OWASP Top 10 due to their widespread presence and high impact.


