TL;DR
- A JavaScript injection attack is a client-side security threat where malicious scripts are inserted into a web page’s code.
- These scripts can steal data, hijack sessions, and compromise users—all from within the browser.
- JavaScript injection is dangerous because it happens invisibly and often bypasses traditional server-side security controls.
Introduction
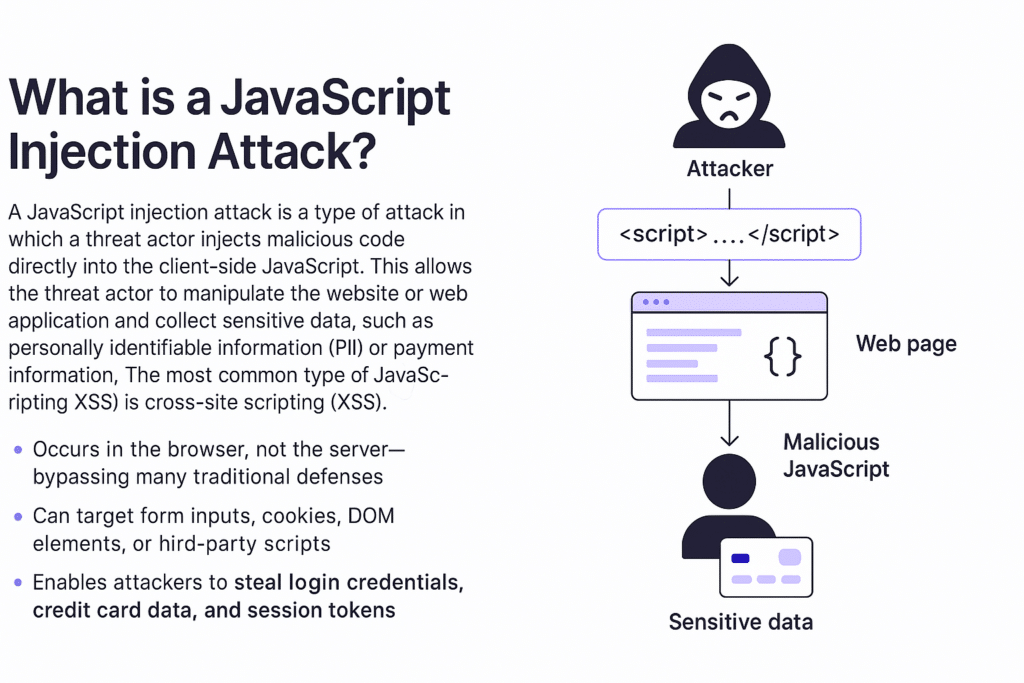
A JavaScript injection attack is a type of attack in which a threat actor injects malicious code directly into the client-side JavasScript. This allows the threat actor to manipulate the website or web application and collect sensitive data, such as personally identifiable information (PII) or payment information. The most common type of JavaScript injection attack is cross-site scripting (XSS).
Key characteristics:
- Occurs in the browser, not the server—bypassing many traditional defenses.
- Can target form inputs, cookies, DOM elements, or third-party scripts.
- Enables attackers to steal login credentials, credit card data, and session tokens.
- Cross-site scripting (XSS) is the most prevalent form, but other variations exist (e.g., DOM-based injection).
- Often triggered when a user loads a compromised page or interacts with vulnerable input fields.
Who are the targets of these attacks?
Businesses
Any organization that maintains a website collecting sensitive data—such as payment details or login credentials—is a potential target. Industries most at risk include:
- Retail and e-commerce
- Entertainment and streaming platforms
- Travel and hospitality
- Utilities and infrastructure
- Third-party vendors (e.g., online advertising platforms, tag managers, analytics providers)
Attackers may aim to steal both financial data and admin or user credentials for broader compromise or resale.
Consumers
Consumer PII, credit card, and financial data are the primary targets of JavaScript injection attacks. This data is used for fraud, identity theft, and social engineering attacks.
How does an attack work?
When a user visits a compromised or vulnerable website, malicious JavaScript code is triggered and executed within their browser—without the user’s knowledge.
This injected script can:
- Capture form data such as credit card information or login details
- Steal cookies to hijack authenticated sessions
- Redirect users to phishing or malware-laden pages
- Log keystrokes or insert fake elements to manipulate actions
Because it happens in real-time in the browser, the attack is often invisible to traditional server-side security tools.
What is the impact of a Javascript injection attack?
Loss of Sensitive Customer Information
When malicious JavaScript captures form input, cookies, or session data, the result is unauthorized access to private customer information.
- Theft of credit card data, names, email addresses, and home addresses during checkout or login processes.
- Stolen authentication cookies and tokens can allow attackers to impersonate legitimate users across multiple sessions or services.
- Compromised credentials may be reused for credential stuffing attacks on other platforms.
Profit loss
The financial implications of JavaScript injection go beyond the breach itself—they can ripple across sales, support, operations, and legal departments.
- Loss of transactional revenue if customers abandon affected platforms.
- Increased support and remediation costs following user impact.
- Drop in customer retention as users lose trust in digital safety.
- Potential loss of partnerships with vendors who require security assurances.
Regulatory and Compliance Issues
Failure to secure client-side environments can lead to non-compliance with major data protection regulations.
- PCI DSS violations if payment data is stolen can lead to revocation of merchant privileges.
- GDPR fines for improper handling of EU resident data can reach up to €20M or 4% of global revenue.
- HIPAA enforcement actions for healthcare-related data breaches can include penalties and required oversight.
- Legal liabilities, class-action lawsuits, and mandatory disclosure requirements.
Reputational Harm
Security incidents tied to JavaScript injection can quickly become public, affecting how users and partners perceive the brand.
- Media coverage and social media backlash can amplify reputational damage.
- Loss of consumer confidence, especially if PII or financial data was exposed.
- Long-term brand erosion that impacts market positioning and investor trust.
What can businesses do to protect against JavaScript injection attacks?
Businesses can reduce the number and impact of JavaScript injection attacks by following these best practices:
Use automated monitoring and inspection
Monitoring and inspection activities are critical, but also time consuming if you don’t have an automated solution to regularly review client-side JavaScript code. A purpose-built solution that automates the process can be a fast and easy way to identify unauthorized script activity that has been injected onto the front end.
Use an advanced, automated Content Security Policy tool
An automated CSP tool can help businesses control their client-side attack surface by deploying and managing Content Security Policies on their web applications. Advanced automated CSP tools identify all your first- and third-party scripts, your digital assets, and the data they can access. The tool then generates appropriate Content Security Policies based on scanned data and anticipated effectiveness. Businesses can fine tune their CSPs at the domain level for easy management, version control, and reporting.
Audit web assets
Maintain a complete inventory of your web assets and understand the type of data each one handles. Regularly inspect pages for vulnerable scripts and unauthorized modifications.
- Identify scripts that interact with sensitive inputs.
- Flag unknown or legacy code for review.
- Prioritize assets handling payment or login data.
Regularly crawl the client side
Use automated tools to scan and analyze client-side behavior across your web applications. This helps uncover anomalies, hidden scripts, and signs of compromise.
- Detect malicious DOM changes or shadow scripts.
- Identify unauthorized third-party behavior.
- Catch early indicators of formjacking or skimming.
Block HTML in inputs
Prevent users from injecting scripts by blocking HTML tags and code snippets at both the front end and back end.
- Strip or escape
<script>,<img>, and other risky tags. - Use libraries that sanitize inputs across browsers.
- Enforce consistent encoding policies.
Validate form inputs
Set clear, restrictive rules for the types of input your forms accept. For example, require alphanumeric characters only and deny special symbols or code-like entries.
- Reject fields with unusual characters or formatting.
- Use allowlists for expected input types (e.g., phone numbers, emails).
- Log rejected entries for monitoring.
Create safe cookies
Apply cookie flags and usage rules that reduce the risk of session hijacking via JavaScript access.
- Use
HttpOnlyandSecureflags on all session cookies. - Consider IP binding or session timeout rules.
- Avoid exposing tokens via client-side JavaScript.
FAQ
What’s the difference between JavaScript injection and XSS?
XSS is a type of JavaScript injection focused on exploiting web applications by injecting scripts. JavaScript injection is broader—it includes any unauthorized script insertion in the browser.
Can JavaScript injection affect mobile apps?
Yes. Hybrid mobile apps (e.g., those built with React Native or Cordova) that render HTML and JavaScript are vulnerable to the same injection threats.
Does using HTTPS prevent injection?
No. HTTPS encrypts traffic but does not protect against malicious scripts or injection vulnerabilities already embedded in the code or third-party libraries.
Is JavaScript injection part of OWASP Top 10?
Yes. It falls under several OWASP Top 10 categories, especially A03:2021-Injection and A07:2021-Identification and Authentication Failures.
How does Feroot help with this?
Feroot provides continuous client-side monitoring, alerting you to unauthorized script activity, DOM manipulation, and third-party risks—making JavaScript injection visible and actionable.