TL;DR
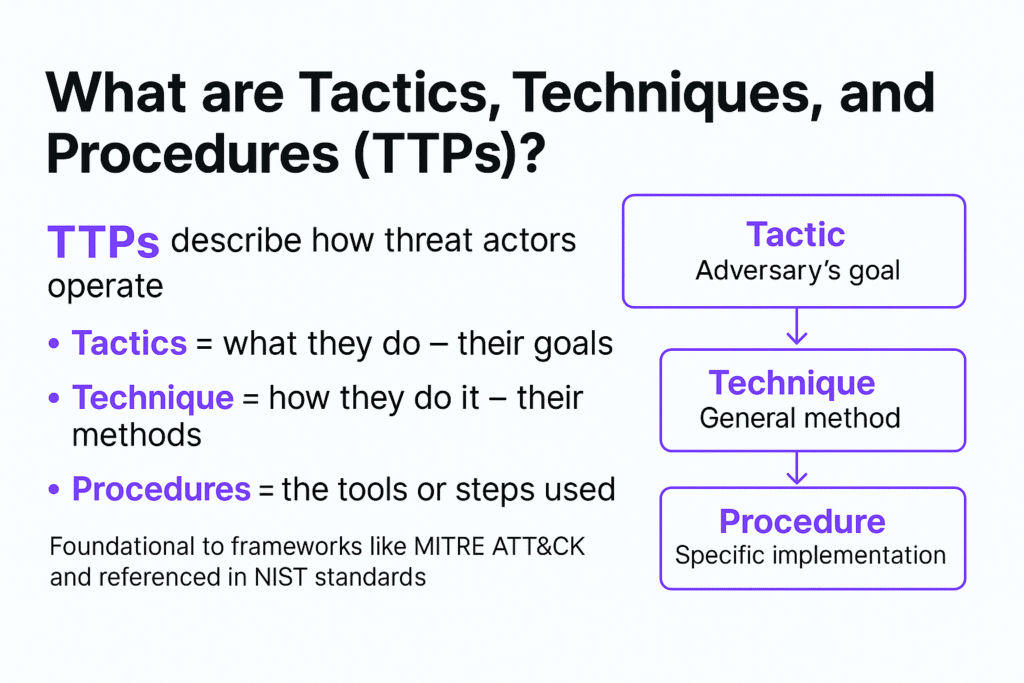
- TTPs—short for Tactics, Techniques, and Procedures—are the behavioral patterns of cyber attackers.
- They describe what attackers do (tactics), how they do it (techniques), and the tools or steps they use (procedures).
- Understanding TTPs helps cybersecurity teams detect, attribute, and mitigate attacks more effectively.
- Commonly referenced in frameworks like MITRE ATT&CK, TTPs are foundational to threat intelligence.
Introduction
If you’re a security analyst, threat hunter, SOC operator, or part of a red team, understanding TTPs is critical. These behavioral signals help identify and stop adversaries before major damage occurs.
This guide explains:
- What TTPs are
- How they relate to real-world threats
- Their role in frameworks like MITRE ATT&CK
- Practical examples and defense strategies
What Are TTPs in Cybersecurity?
Tactics, Techniques, and Procedures (TTPs) describe the strategic and operational behavior of threat actors.
- Tactics = The why (the adversary’s objective)
- Techniques = The how (general method used). The method used by the threat actor to engage in the attack can be e-skimming, magecart, javascript injection attacks, or cross-site scripting (XSS).
- Procedures = The specific (exact sequence of actions)
These concepts form a layered model of attacker behavior, essential for cyber threat intelligence and defense planning. Security professionals may apply TTPs to any type of attack, from traditional server-side threats like ransomware to client-side JavaScript supply chain attacks.
TTPs Breakdown: Tactic vs Technique vs Procedure
| Layer | Description | Example |
| Tactic | Adversary goal or objective | Gain Initial Access |
| Technique | General method to achieve the goal | Spearphishing via Email |
| Procedure | Detailed execution of the technique | Sending payloads via a spoofed HR email |
Understanding these layers helps defenders correlate signals, detect intrusions faster, and attribute attacks more accurately.
Real-World Example: How TTPs Work in an Attack
Imagine a phishing campaign:
- Tactic: Initial Access
- Technique: Spearphishing Attachment
- Procedure: A threat actor sends a fake job offer email with a malicious PDF exploiting a known CVE.
By detecting these steps early, SOC teams can break the kill chain and prevent lateral movement.
Frameworks That Use TTPs: MITRE ATT&CK and NIST
MITRE ATT&CK
The ATT&CK framework is a comprehensive TTP database used to map threat actor behavior.
Each group in the framework (like APT29 or FIN7) has a unique TTP profile, enabling behavior-based detection and attribution.
NIST Cybersecurity Framework (CSF)
NIST acknowledges TTPs in its cybersecurity guidance, particularly in:
- NIST SP 800-53 (Security and Privacy Controls): Encourages monitoring for behavior-based anomalies, including adversary TTPs.
- NIST SP 800-61r2 (Incident Handling): Recommends correlating events and behaviors (TTPs) to recognize coordinated attacks.
- NIST Cyber Threat Framework: Explicitly structures adversary behaviors using tactics and techniques, aligned with TTP taxonomy.
Organizations using NIST-aligned controls benefit from integrating TTPs into continuous monitoring, SIEM rules, and threat hunting strategies.
Why TTPs Matter: Detection and Attribution
Benefits:
- Precision Detection: TTPs map closely to behavior-based alerts, enabling detection even when malware is obfuscated.
- Threat Attribution: Nation-states and APTs have repeatable TTP fingerprints (e.g., APT29’s use of credential dumping).
- Proactive Defense: Red teams simulate TTPs to test resilience.
- Framework Alignment: Tools like MITRE ATT&CK rely on TTPs for structured threat analysis.
Risks:
- TTP Overlap: Different groups may share similar techniques.
- Procedure Evolution: Attackers constantly tweak procedures to evade detection.
Best Practices for Tracking TTPs
- Use the MITRE ATT&CK framework for mapping TTPs
- Automate TTP enrichment in SIEM and SOAR platforms
- Correlate TTPs across kill chain stages
- Focus on behavior, not just IOCs
Security teams that prioritize TTP-based detection outperform those relying solely on static indicators like hashes or IPs.
FAQ
What does TTP stand for in cybersecurity?
TTP stands for Tactics, Techniques, and Procedures. It describes the behavior and methods used by threat actors in cyber attacks.
How do TTPs help in threat detection?
TTPs reveal attacker intent and methods, allowing security teams to detect behavior rather than just known malware signatures.
Is MITRE ATT&CK based on TTPs?
Yes. MITRE ATT&CK is a knowledge base that categorizes and documents adversary TTPs across the cyber kill chain.
What’s the difference between a technique and a procedure?
A technique is a general approach (e.g., credential dumping), while a procedure is how it’s actually carried out (e.g., using Mimikatz on Windows Server 2019).
Why do TTPs matter more than IOCs?
TTPs are harder to fake and evolve more slowly than IOCs, making them more reliable for long-term threat detection.


