Modern checkout pages have evolved from static forms into dynamic ecosystems where dozens of third-party scripts run alongside first-party code. This complexity expands the attack surface and challenges traditional defenses designed for fixed perimeters. PCI DSS 6.4.3 was introduced to address that shift, emphasizing continuous oversight of browser-executed scripts and the integrity of client-side behavior.
What You’ll Learn in this article:
- Why e-commerce PCI compliance demands a different playbook than traditional retail environments
- How to use a three-tier authorization framework to align security with business velocity
- What really breaks when you deploy Subresource Integrity (SRI), and how to fix it without slowing growth
- How to approach PCI DSS 6.4.3 as a strategic investment in safeguarding revenue, moving beyond the compliance-only mindset.
E-commerce reality
Modern checkout pages don’t behave like closed, predictable point-of-sale terminals. They run in dynamic browsers that routinely incorporate external code and services. In practice, many checkout experiences load dozens of third-party scripts before any payment data is entered, providing a useful benchmark for the operational complexity teams manage every day.
The Neiman Marcus data breach is a reminder of how serious these risks can be. In 2021, the company reported a compromise that exposed information from more than 4.6 million customer accounts. The aftermath included regulatory scrutiny, legal settlements amounting to several million dollars, and lasting harm to customer trust. Incidents like this highlight how a single overlooked script or integration can lead to far-reaching consequences.
The 2025 Verizon Data Breach Investigations Report points out that web application attacks, including client-side skimming, continue to be among the most frequent causes of data exposure. These attacks often trigger penalties, lawsuits, and reputational damage that exceed the immediate financial loss.
The goal for modern security teams is not to slow down the business. It’s to make sure that innovation happens safely. When verification becomes part of everyday work rather than a final checkpoint, marketing and product teams can move forward with confidence. Progress and protection start to feel like parts of the same process, not competing priorities.
Authorization strategy
Authorization is the first pillar of PCI DSS 6.4.3. It sets the foundation for how scripts are introduced, reviewed, and approved before they reach production. Authorization ensures that every script running on a payment page has a clear purpose, a trusted source, and an appropriate level of oversight.
At Feroot, conversations with leading compliance and security professionals often return to this principle. The strongest programs do not treat authorization as a barrier to innovation. They treat it as a way to align security practices with the core business. When authorization frameworks are well-designed, they bring balance: teams can move quickly while maintaining visibility, control, and integrity.
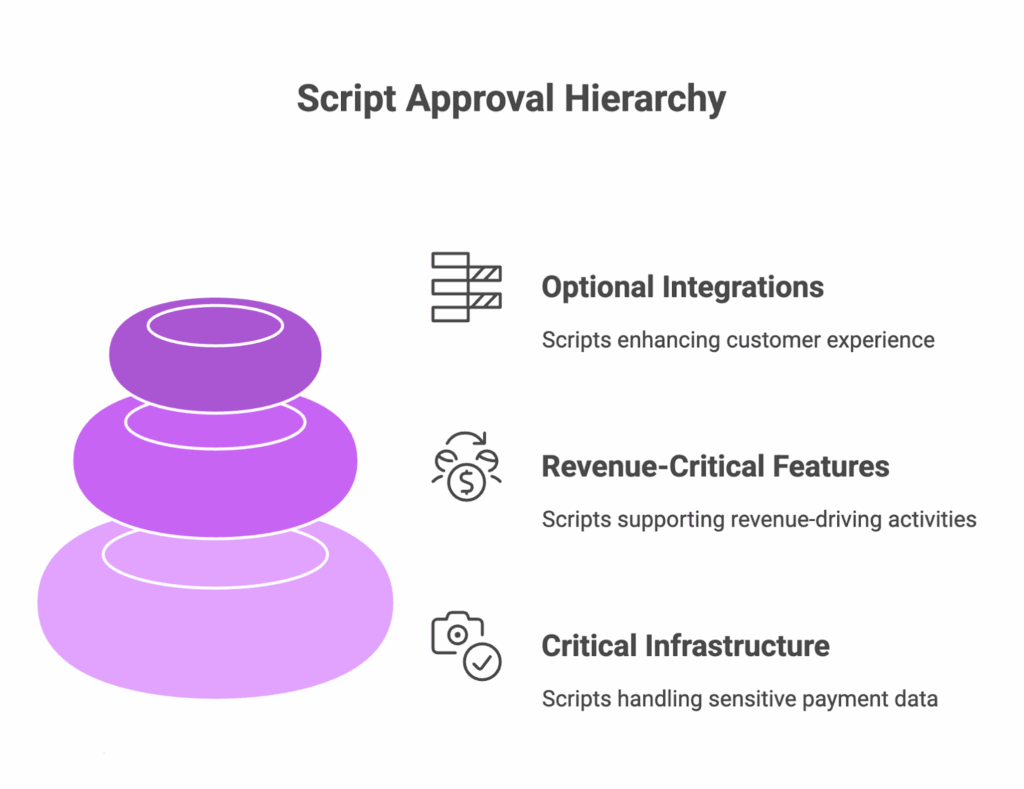
To make this practical, many organizations use a three-tier model that aligns the level of review with the level of risk.
Tier 1: Critical infrastructure approval
Scripts that touch checkout functionality or cardholder data belong in this category. They represent the foundation of your business and require the highest level of scrutiny. Approvals should come from senior leadership, such as a VP or CISO. Subresource Integrity (SRI) is mandatory for all Tier 1 scripts to ensure that nothing loaded from a third-party source has been tampered with. Strict change control processes are also essential. These are the trust anchors of your digital ecosystem.
Tier 2: Revenue-critical feature review
Scripts in this category support revenue-driving activities such as analytics, conversion tracking, and fraud detection. These scripts are important for growth but do not handle sensitive payment data directly. They should be reviewed monthly, logged within the Content Security Policy (CSP), and continuously monitored for unexpected changes. This tier allows business teams to maintain momentum while security maintains oversight.
Tier 3: Optional integrations review
Optional scripts include post-purchase surveys, personalization tools, and retargeting pixels. They contribute to customer experience but are not essential for checkout operations. A lighter quarterly review process is appropriate here. This prevents unnecessary sprawl while keeping implementation flexible and low-impact.
This model becomes especially valuable in moments of real-world pressure. During a busy promotion, for example, marketing might request a new conversion pixel late in the evening. Under this framework, the script would be categorized as Tier 2, approved with monitoring, and allowed to go live without delay. Compliance remains intact and business continues smoothly.
In another scenario, a vendor might release an urgent update to a checkout SDK. Because it directly affects the payment process, that script would fall under Tier 1. It would escalate immediately to leadership for review and approval, ensuring accountability where the potential impact is highest.
The most effective organizations treat this process as a structure that enables confidence. When every team understands how scripts are classified, approvals become quicker, audits become easier, and risk becomes measurable. Feroot’s work with compliance leaders has shown that this clarity allows organizations to build security programs that are both resilient and responsive.
Tamper control with sub-resource integrity (SRI)
Subresource Integrity, or SRI, is one of the most effective ways to verify that the scripts running in a browser have not been altered. It works by assigning a cryptographic fingerprint to each approved script. When the browser loads the script, it checks the fingerprint to confirm that the file is identical to the one originally approved. If it is not, the script will not load.
In principle, SRI sounds simple. In practice, it can create challenges when scripts are updated frequently or when vendors release new versions without notice. If the fingerprint changes before the verification record is updated, legitimate scripts may fail to load. Successful organizations discover that integrity verification only works long term when it’s built around how the business truly operates day to day.
Over time, Feroot has observed several best practices that make SRI both effective and sustainable:
- Plan for marketing enablement. Provide pre-approved and verified fingerprints for the scripts your marketing teams use most often, such as analytics tools (Google Analytics 4, Adobe Analytics), tag managers (Google Tag Manager, Tealium), and advertising or conversion tracking pixels (Meta Pixel, LinkedIn Insight Tag, Google Ads Conversion Tag). Having these verified in advance allows campaigns and site updates to move forward smoothly while still maintaining integrity checks and compliance.
- Collaborate with vendors. Encourage partners to publish versioned scripts with consistent update schedules and available hashes. This allows your team to plan for changes instead of reacting to them.
- Implement monitoring and alerts. Establish clear alerts when a script fails integrity verification so the issue can be resolved quickly without disrupting customer experience.
When SRI is supported by these practices, it becomes a reliable part of everyday operations rather than an obstacle. It reinforces trust at the browser level and turns compliance into an active form of protection instead of passive control.
QSA partnership
A good Qualified Security Assessor is not an adversary. Their goal is to verify that your controls can withstand real-world conditions. They will look for consistency, repeatability, and evidence that your systems function under pressure. The difference between a weak and strong audit response often comes down to visibility. A weak answer might depend on a static spreadsheet. A strong answer demonstrates live monitoring, clear ownership, and automated alerts. When this visibility is built into daily operations, audits become collaborative rather than stressful.
The difference between failing and passing often comes down to how you answer:
Weak answer:
QSA: “How do you know which scripts touch payment data?”
You: “We have a spreadsheet.”
Strong answer:
QSA: “How do you know which scripts touch payment data?”
You: “Our monitoring platform shows 14 scripts with payment access, updated hourly, with alerts for any changes.”
Business case
If you’re going before your management or board to get approval for your compliance framework and its associated costs, it’s a good idea to make the case in their language. CFOs and boards don’t think in “compliance hours.” They think in terms of revenue and efficiency. Here are 3 ways you can frame the conversation.
Frame 1: Revenue protection – IBM pegs breach costs at $4.45M; a single compromise can erase holiday revenue. Your investment in compliance protects revenue.” .
Frame 2: Operational efficiency – “Compliance automation can save the company between $18K and $30K annually compared to manual tracking.”
Frame 3: Audit readiness – “Zero delays and zero last-minute scrambles allow teams to prioritize revenue-generating activities.”
Here’s what this looks like on a summary slide:
Annual cost: {platform subscription fees}
Revenue protected: $7.9M in breach exposure avoided
Operational savings: $27,000 in manual hours
Compliance outcome: Audit-ready evidence, no delays
When positioned this way, compliance becomes less of an operational burden and more of a core infrastructure investment that protects revenue and strengthens the company’s strategic advantage.
Strategic advantage
The most competitive organizations treat PCI DSS 6.4.3 as infrastructure intelligence.
While your competitors might treat compliance as a drag, the shift for your company is to treat it as your leverage. The discipline required to manage scripts, enforce integrity, and maintain inventory becomes the same discipline that drives secure, scalable growth for your organization.
By viewing PCI DSS 6.4.3 according to this perspective, it becomes a blueprint for building e-commerce systems that protect revenue, accelerate business, and strengthen trust at scale.