When client-side security breaches happen, web application developers may find themselves at the receiving end of the blame game (somewhat unfairly). The demands of an accelerated development cycle combined with pressures related to JavaScript web applications security, means developers may feel caught in the proverbial “damned if you do and damned if you don’t” loop.
Increasing website attacks make implementing JavaScript security technologies and processes a priority for any business. The proliferation of third-party libraries and vulnerable JavaScript code increase client-side attack risk. Criminal purveyors of Magecart, cross-site scripting (XSS), and other types of script attacks take advantage of these vulnerabilities. And with vulnerabilities identified, hackers then inject malicious scripts into existing source code to steal sensitive data, personally identifiable information (PII), financial data, and credit card numbers, which can be monetized on the dark web.

Why Do Businesses Need JavaScript Web Application Security?
The reasons why JavaScript web application security is so critical comes down to three primary factors: (1) how web application security works; (2) JavaScript code itself; and (3) the proliferation of open-source libraries.
Client-Side Operations & JavaScript Web Application Security: Websites operate primarily on the client side or front end (as opposed to the server side or back end). Traditional perimeter security tools do not protect the client side, and tools like web application firewalls (WAFs), policy controls, and threat intelligence are only partially effective for front-end security. (To better understand client side vs. server side, check out our blog: What is the difference between client side and server side and why is it important to your everyday security?)
Insecure JavaScript: To add to the complexity, JavaScript wasn’t built with security in mind. Because there are no security permissions built into the JS framework, it is difficult to prevent client-side attacks on JavaScript code. The most common JavaScript security vulnerabilities include:
- Source code vulnerabilities
- Input validation
- Reliance on client-side validation
- Unintended script execution
- Session data exposure
- Unintentional user activity
Open Source Libraries: When you’re under pressure to create an elegant application quickly, compiling pre-written code can make sense. Open source libraries are a great source for pre-written JavaScript code. However, the third- and fourth-party code found in open source libraries is often flawed and sometimes malicious. Adding this code to a business website can open the organization up to breaches and JavaScript supply chain attacks.
In fact, a recent research study by WhiteSource highlighted the problems with open source libraries and JavaScript, identifying more than 1,300 malicious packages in the most commonly downloaded JavaScript package repository.

Bridging the development and security divide
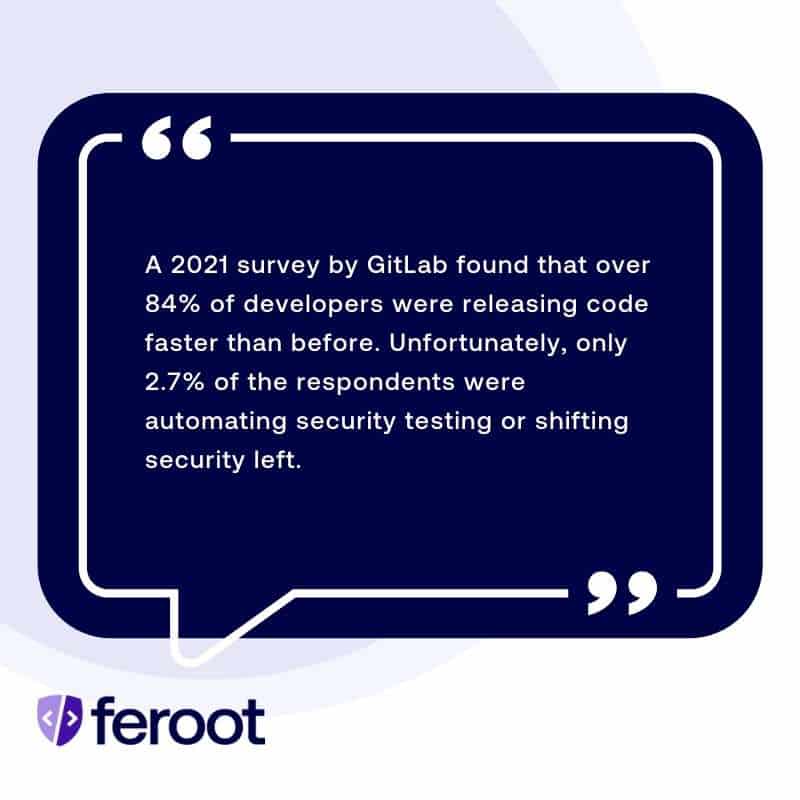
The need for secure web application development is ever present. A 2021 survey by GitLab found that over 84% of developers were releasing code faster than before. Unfortunately, only 2.7% of the respondents were automating security testing or shifting security left.
Bridging the divide between development and security comes down, in part, to understanding the risks associated with insecure development activities and vulnerable code. Developers, in particular, often find themselves caught between development velocity and web app security. Contrary to popular opinion, an accelerated application development cycle and application security are not mutually exclusive. In fact, with the right processes and tools in place, developers can still quickly churn out functional and elegant web applications and make the development process secure at the same time.
To help ensure a secure development process, here are five easy things developers can do:
- Move security to the left: Security needs to happen throughout the whole software development lifecycle. Take a few minutes to engage with the security team or security experts for advice and assistance.
- Maintain safe JavaScript open-source libraries and be selective with third- and fourth-party scripts, plugins, and tools: Confirm the security of any external libraries by making sure they’re not on any blocklists. Regularly patch and update your libraries. Always inspect third- and fourth-party additions for vulnerabilities.
- Perform automated client-side attack surface monitoring: Inspection activities are critical, but also time consuming if you don’t have an automated solution to review JavaScript code. A purpose-built solution, like Feroot’s Inspector that automates the process can be a fast and easy way to identify malicious script activity on exciting web applications.
- Implement web application development security best practices: Prevent cross-site scripting and injection attacks by avoiding inline JavaScript, using an advanced, automated content security policy, validating input, avoiding eval(), and keeping strict mode on.
- Know the OWASP Top Ten: Know what web application security threats are the most common and risky based on analysis by the Open Web Application Security Project (OWASP). Developers can use the OWASP Top 10 to set the stage for improving the security of web applications early in the development process.
Build More Secure JavaScript Web Applications
JavaScript carries tremendous client-side risk. The only way to protect businesses and customers is to apply JavaScript security best practices to the web application development process.