A more resilient approach to preventing e-skimming attacks starts with breaking an old habit: assuming client-side scripts are “known good.”
Because modern checkout pages rely on services that support analytics, experimentation, fraud detection, and customer experience, and each one can add JavaScript that shifts quietly as vendors and tag managers update their code.
The modern setup brings real flexibility, but it also creates a gap in ownership. Trust is extended, but control fades.
Resilience comes from reversing that. It begins when security leaders treat the payment page as an environment they still own.
This article shows how to build the visibility and governance that make e-skimming prevention clear, steady, and dependable.
What you’ll learn in this article:
- Malicious JavaScript on checkout pages captures card data as customers type, which means traditional server-side tools alone are not enough to prevent e-skimming attacks.
- Effective Magecart attack prevention and formjacking protection start with a complete inventory of payment-page scripts, clear ownership, and the ability to detect unauthorized changes in real time.
- Client-side monitoring, script governance, and a tested incident response plan help you prevent e-skimming, satisfy PCI DSS v4.0 requirements (6.4.2, 6.4.3, 11.6.1), and give your team evidence they can stand behind during an audit.
Understanding E-Skimming attacks
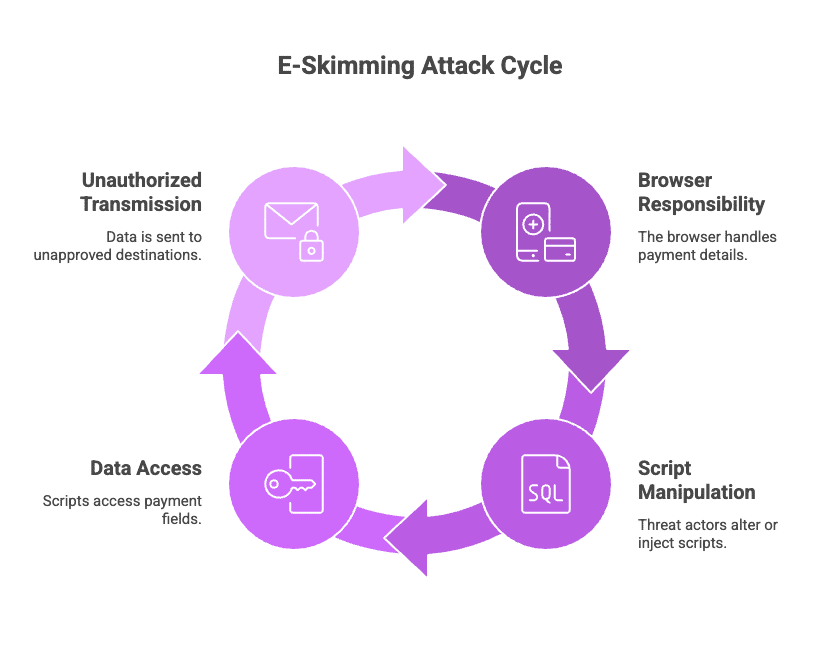
The clearest way to understand e-skimming is to recognize that the browser now carries responsibility once reserved for backend systems.
It is the place where customers type payment details, where scripts handle those inputs directly, and where changes in what a script reads or sends become part of the live checkout flow.
So if a threat actor successfully alters an existing script or injects a new one, that script can begin accessing payment fields and sending the information to destinations the team never approved. That combination of new access and unapproved transmission creates the conditions for e-skimming.
Check out: How to Detect and Prevent JavaScript Injection Attacks on Websites
The Volusion breach is one well-known example, where a change to Volusion’s cloud commerce platform introduced a skimming script into the shared JavaScript file that supported merchant storefronts. And because the platform served that file to every shop, the script ran across many checkout pages at once.
It’s a reminder that e-skimming aligns with script behavior in the browser, and that visibility into that behavior is the most reliable starting point.
Payment page attack surface: Third-party scripts and client-side risks
When you look at e-skimming, the significant shift is to stop thinking only about “the website” and start thinking about “the code that runs in the customer’s browser when they pay.” That is your real payment perimeter.
Check out: Which Solutions Detect Unauthorized JavaScript Trackers in Real-Time?
On a typical checkout, there are several moving parts. Your own JavaScript renders the page, handles validation, and talks to back-end services. Third-party scripts sit beside it for analytics, fraud detection, performance monitoring, and marketing.
Those third parties may, in turn, load fourth-party code that you did not select directly but that still runs in the same context. CDN-hosted libraries, such as shared frameworks and UI components are pulled in as needed. Tag management systems serve as a deployment layer for many of these scripts simultaneously.
The key insight is simple: count and monitor the scripts on your checkout page. Because each script contributes to the environment, whether it comes from your team, a vendor, or a vendor’s vendor. When that environment changes, even slightly, it makes room for unintended behaviour.
A useful exercise with your team is to ask three questions and insist on concrete answers, not approximations:
- Can we list every script that runs on checkout right now?
- What information can each script read or modify?
- When did each script last change, and who approved that change?
5-layer defense strategy to prevent e-skimming and Magecart attacks
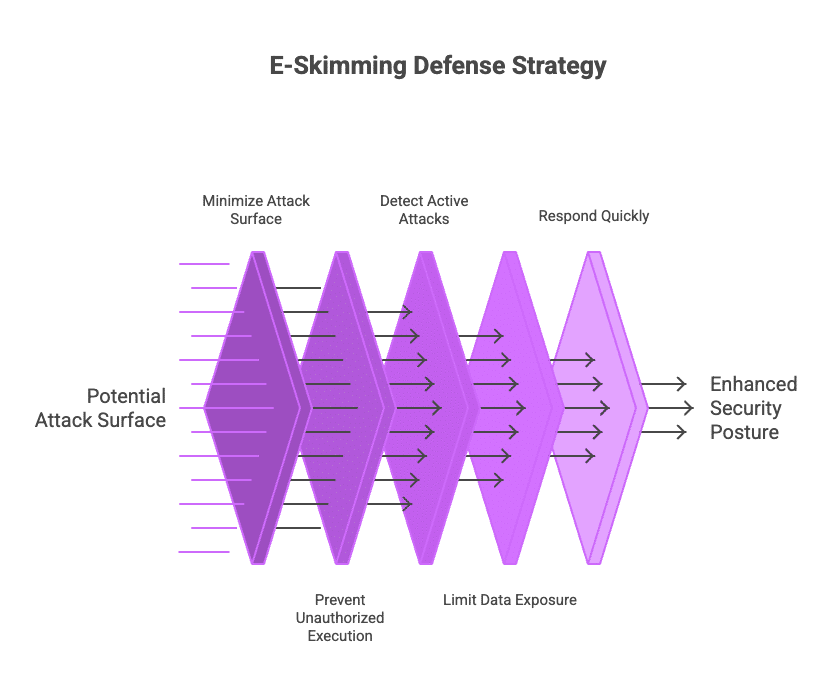
A single control cannot stop e-skimming. It is reduced by a set of layers that work together, each closing off a different part of the path an attacker needs to take.
Layer 1: Minimize attack surface
A good starting point is to reduce the things that can go wrong quietly. That often means trimming the checkout page to only what is essential for payment processing, fraud controls, and compliance, and removing the rest. From there, control over who can change the payment page code and through which deployment paths becomes a deliberate design choice rather than an accident of history.
Layer 2: Prevent unauthorized execution
Once the surface is smaller, the next step is to control what is allowed to run. Content Security Policy helps by defining which domains may serve scripts and where data may flow. Subresource Integrity complements this by ensuring that static scripts from CDNs match a known hash before the browser trusts them.
Secure iframe patterns for payment widgets further contain what external providers can see. It is essential to acknowledge that CSP has limits. Many e-commerce teams rely on third-party services that make a stringent policy impractical, which is why later layers are not optional.
Layer 3: Detect active attacks
With guardrails in place, attention turns to what is happening in production. Continuous, real-time observation of client-side behavior gives you early notice when something changes: new scripts appearing, existing scripts accessing payment fields differently, or network requests to unfamiliar domains.
Feroot PaymentGuard AI monitors script behavior on payment pages, correlates meaningful changes, and raises tamper alerts that your SOC or incident team can act on quickly.
Layer 4: Limit data exposure
Even with strong monitoring, it is advisable to reduce the value of any data that an attacker might reach. Tokenizing card information as early as possible, encrypting sensitive fields on the client where design allows, and keeping payment data in memory only for brief, well-defined periods all help reduce the blast radius.
These measures do not replace monitoring, but they change the scale of harm if a skimmer does manage to execute.
Layer 5: Respond quickly
Prepare for the moment when you see an anomaly. An incident response plan for e-skimming should define who is called, how malicious scripts are removed, how evidence is preserved, and how card brands and acquirers are notified.
PCI DSS 6.4.3 and 11.6.1: E-skimming detection requirements
When you view e-skimming through the lens of PCI DSS v4, it becomes clear that monitoring is now treated as part of standard payment-page governance.
Requirements 6.4.3 and 11.6.1 now require organisations to know which scripts run on payment pages, maintain their integrity, and detect and alert on unauthorized changes that could affect cardholder data.
What effective monitoring should include:
- Coverage of all payment pages in production, at all times, not just the homepage or staging
- Tracking of first, third, and fourth-party scripts as a single, in-scope set under PCI DSS 6.4.3
- Behavioural analysis that can see when scripts start reading payment fields or interacting with the checkout DOM in new ways
- Context-aware alerts that distinguish planned, approved changes from suspicious modifications
- Awareness of which scripts are authorised, when they last changed, and whether any new, unapproved scripts have appeared on payment pages
Common gaps to close
The gaps we see most often are the opposite of what PCI expects. Point-in-time scanning that runs monthly or quarterly, rather than continuous visibility. Monitoring that focuses on the homepage or marketing pages, while checkout is assumed safe.
Static inventories with no behavioural analysis, so a script can begin reading card fields without being noticed. Manual, ad hoc alert review with no clear SLA for payment page incidents.
From a practical standpoint, it helps to define response timelines that match both risk and compliance expectations:
- Immediate. Alert when any new script is added to a payment page or when an unauthorized domain starts receiving data from checkout.
- Within hours. Investigate the alert, validate whether the change was part of an approved deployment or a vendor update, and decide whether to block or temporarily roll back.
- Within days. Complete basic forensics, establish the time window and scope of any e-skimming activity, and execute remediation steps.
E-skimming incident response
Immediate (First Hour):
When you confirm or strongly suspect active e-skimming on checkout, the priority is containment. In many cases, that means taking the affected payment page or path offline, or moving to a known-good fallback flow, to stop further card data exposure.
At the same time, block outbound traffic to known attacker domains and preserve logs and artifacts. Activate your incident response plan and bring in the security operations, legal, and compliance teams, as PCI DSS Requirement 12.10 requires.
Short-term (24-48 Hours):
As containment stabilizes, start structured forensics. Identify how the skimmer was introduced, which scripts or vendors were involved, and which transactions and customers may be affected.
Remove malicious code, patch exploited vulnerabilities, and reset any compromised credentials. Work with your acquirer and card brands on any required engagement of a PCI Forensic Investigator, and align breach notifications with their programs and applicable laws.
Long-term (Weeks):
Over the following weeks, complete the forensic investigation, document the scope, and implement additional controls on payment pages, including stricter script governance and monitoring for PCI DSS 6.4.3 and 11.6.1.
Use the incident to refine your incident response playbooks and strengthen both technology and vendor controls so the exact path cannot be reused.
How e-skimming prevention satisfies PCI DSS 6.4.3, 6.4.2 and 11.6.1
When you look at e-skimming through a PCI lens, the standard is not asking for anything mysterious. It is asking you to control the same client-side risks you already care about, and to prove that control in a structured way.
Requirement 6.4.3: Know and justify every script on payment pages
PCI DSS v4.0.1 introduced 6.4.3 specifically for payment page scripts. The requirement expects you to maintain an inventory of all scripts that load and execute in the customer’s browser, document why each one is necessary, and ensure they are authorized. This applies to your scripts, third-party scripts, and iframes.
Requirement 11.6.1: Detect tampering in real time
Requirement 11.6.1 adds a second expectation. It calls for a change and tamper-detection mechanism that evaluates HTTP headers and payment page content as received by the consumer’s browser and alerts on unauthorized modifications.
This formalizes what you already need for e-skimming defense.
Requirement 6.4.2: Protect public-facing web applications
Requirement 6.4.2 builds on the intent of legacy Requirement 6.6 from PCI DSS v3.2.1, which requires an automated technical solution, such as a web application firewall in front of public-facing web applications, to detect and prevent web-based attacks. While a WAF will not catch every e-skimming attempt just by its own, it is part of the overall control set PCI expects around your e-commerce front end.
Taken together, 6.4.2, 6.4.3, and 11.6.1 describe a coherent control story: protect your application, inventory, and authorize scripts, and detect unauthorized changes on payment pages in the browser.
The upside is that if you build a client-side security program around those points, you are moving toward both Magecart attack prevention and PCI alignment at the same time. In other words, good e-skimming prevention is not a separate project. It is how you satisfy the new PCI requirements in a way that protects customers’ cards and your audit posture.
Implementation Roadmap
A good way to prevent e-skimming attacks is to build the program in phases. You are not trying to solve everything in a week. You are trying to reach a point where you can clearly see what runs on checkout, control who can change it, and prove it to yourself and to a PCI assessor.
Phase 1: Assessment (Week 1)
The first step is discovery. Create an inventory of all scripts that execute on payment pages and map each script to its vendor. PCI DSS 6.4.3 requires you to know and justify each payment page script, so this inventory serves as your foundation.
Phase 2: Quick wins (Weeks 2 to 3)
Next, remove scripts that are clearly not needed on checkout and restrict who can edit the payment page code. At the same time, introduce a basic Content Security Policy that at least limits script sources to known domains.
Phase 3: Monitoring (Weeks 4 to 6)
With the surface reduced, introduce client-side monitoring that tracks all first, third, and fourth-party scripts on payment pages, in line with PCI 11.6.1 requirements for change and tamper detection in the browser. Configure alerts and establish baselines so the team knows what normal looks like.
Phase 4: Hardening (Weeks 7 to 8)
Once monitoring is stable, strengthen CSP, add Subresource Integrity for static scripts where possible, tighten access controls, and refine vendor requirements so new integrations meet 6.4.3 and 11.6.1 expectations from day one.
Phase 5: Ongoing program
Finally, treat this as an ongoing discipline. Review scripts regularly, audit key vendors, tune alerts, and run tabletop exercises that walk through an e-skimming scenario from detection to notification, in line with PCI incident response guidance.
Common e-skimming prevention challenges (and how to solve them)
In practice, most of the resistance you encounter has little to do with the idea of security and everything to do with tradeoffs that teams worry about.
Marketing often owns tags and experiments and may see e-skimming controls as friction. The way through is not to argue in abstractions but to show what a real incident costs.
Performance concerns come next. Teams worry that client-side monitoring will slow checkout. The reality is that modern monitoring can be designed to add only a small amount of latency, especially when scripts are loaded asynchronously and data collection is optimized. The proper conversation is not “zero impact” but “measured, acceptable impact with clear value and trade-offs”
CSP is another common point of tension. A strict policy can break functionality if you go from nothing to full enforcement in one step. A report-only mode, focused first on visibility and then gradually tightened, works far better with product and engineering.
Manual e-skimming prevention vs. automated monitoring
Many teams begin with manual processes to understand which scripts run on their checkout pages and to keep records aligned with PCI DSS requirements. While this approach can work for simpler environments, it isn’t scalable. Because as payment pages evolve and vendors update their code more frequently, the effort required to maintain that understanding grows, and gaps tend to appear between review cycles.
Discovery and Monitoring
Manual reviews often rely on a developer inspecting the checkout source code and documenting the scripts in spreadsheets or notes tied to Requirement 6.4.3. This can be accurate at a single point in time, but it rarely captures how scripts change between assessments. Vendor and fourth-party code can load without much visibility, and it becomes hard to track when a script begins to access payment fields or connect to new domains.
On the other hand, Feroot PaymentGuard AI automatically discovers all scripts in real time, including third-party dependencies. Continuous monitoring detects behavioral changes, new domain connections, or suspicious payment field access. Real-time alerts meet PCI DSS 11.6.1 requirements. This means that minutes spent on setup translate into ongoing production.
Keeping Compliance Evidence Current
Manual evidence collection typically relies on screenshots, notes, and spreadsheets assembled for QSA reviews. These records reflect a single point in time and tend to become outdated quickly, which makes updates harder to maintain between assessments.
Feroot PaymentGuard AI automates the entire process. This way, you get audit-ready reports for PCI DSS 6.4.3 and 11.6.1 generated on demand, proving continuous operation with timestamps and integrity validation.
The Bottom Line
Manual e-skimming prevention typically requires 60 to 100 hours for initial setup and 40+ hours per quarter for ongoing compliance. PaymentGuard AI reduces this to 2 to 4 hours for integration and automated continuous monitoring, roughly an 85% reduction in effort.
Automated e-skimming prevention with PaymentGuard AI
PaymentGuard AI continuously discovers all payment page scripts, monitors behavior to detect tampering or unauthorized access to payment fields, and provides audit-ready evidence for PCI DSS 6.4.3 and 11.6.1. Deployment takes minutes and works across all major e-commerce platforms.
Request a Demo to see how PaymentGuard AI can give your team clear sight into what runs on checkout and quiet confidence that e-skimming is being handled.
FAQ
Can we rely on a WAF alone to prevent e-skimming?
No. WAFs protect server-side vulnerabilities but cannot see malicious JavaScript injected into the browser. E-skimming happens client-side, which is why PCI DSS added requirements 6.4.3 and 11.6.1 specifically for payment page scripts.
How quickly must we respond to e-skimming alerts?
PCI DSS doesn’t specify exact timelines, but best practice is immediate containment (within the first hour), followed by investigation and remediation within 24-48 hours. Define response SLAs that match your risk tolerance and document them in your incident response plan.
Do we need separate tools for 6.4.3 and 11.6.1?
Not necessarily. Many client-side security platforms address both requirements by maintaining script inventories (6.4.3) while continuously monitoring for unauthorized changes (11.6.1). The key is proving both capabilities to your QSA.
What if we recently deployed monitoring but lack historical data?
QSAs accept recently deployed controls if you can demonstrate they’re actively working. Provide current logs, at least one complete monitoring cycle matching your defined frequency, and documentation showing the control is operational, not just configured.


