TL;DR
- Shadow code is any code running on your website or app that was added without security review or visibility—often from third-party scripts or plugins.
- It matters because it introduces unseen risk, such as data leaks, compliance failures, or malicious injections.
- Think of shadow code as the “shadow IT” of the front end—running silently, often dangerously, outside your security team’s control.
Introduction: Why Shadow Code Matters
If you’re in security, dev, or compliance, chances are your organization’s digital assets rely heavily on third-party tools, plugins, and scripts. These integrations make websites faster, more interactive, and more useful—but they also introduce code that’s outside your visibility and governance.
That’s shadow code:
Code introduced (often dynamically) through third-party services, content delivery networks (CDNs), or marketing tools that runs in the browser, yet escapes formal review.
In this article, we’ll cover:
- What shadow code is and how it works
- Where it shows up (real-world examples)
- The risks it introduces
- How to detect and manage it effectively
What is Shadow Code?
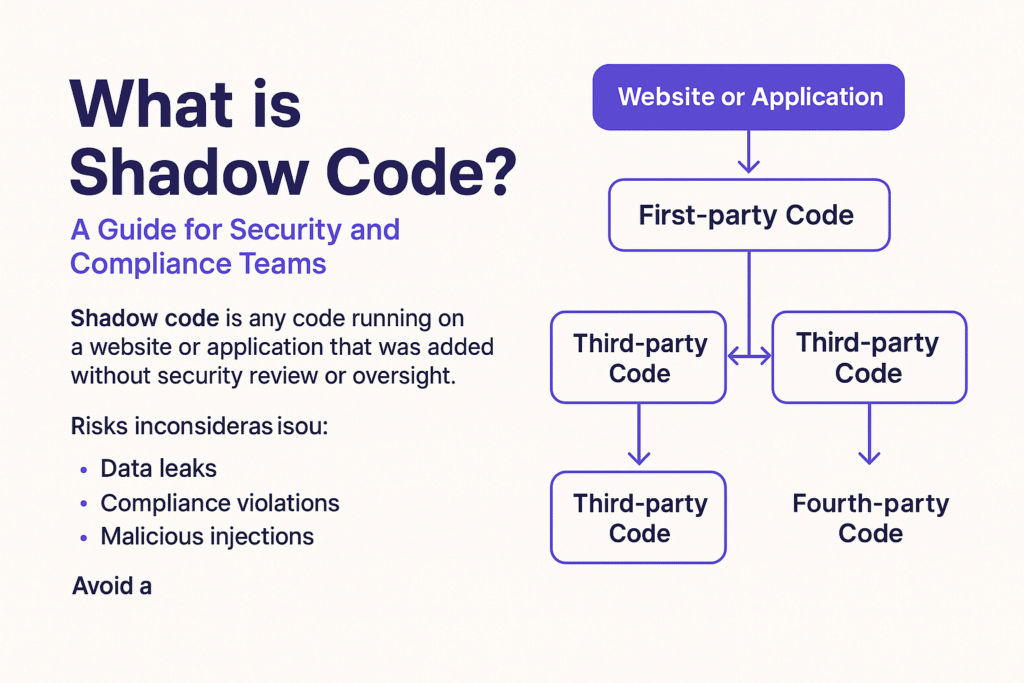
Shadow code refers to scripts and components executing on your application or website that have not been reviewed, tested, or approved by your internal teams. It typically originates from:
- Third-party scripts (e.g., analytics, ads, A/B testing tools)
- Tag managers loading external resources dynamically
- Browser extensions or injected plugins
- Fourth-party calls (scripts loading even more scripts)
Unlike back-end vulnerabilities, shadow code lives in the client-side environment—often JavaScript—and is difficult to track post-deployment.
Real-World Examples of Shadow Code
Here’s where shadow code typically hides:
- Marketing scripts added via tag managers without developer oversight
- Ad tech code that loads trackers or auto-plays media from untrusted sources
- Third-party JavaScript libraries with auto-update features (like jQuery via CDN)
- Widgets (chatbots, payments, video players) that call external APIs
For example, a simple embedded YouTube video might silently load 8–10 scripts from various Google and third-party services—none of which are visible in your codebase or controlled by your team.
Risks of Shadow Code
Unchecked shadow code poses significant threats:
- Data leakage: Sensitive info (PII, credentials, payment data) may be exposed to unknown third parties
- Compliance failures: Violates PCI DSS 4.0 (e.g., Requirements 6.4.3 and 11.6.1), GDPR, CCPA
- Malicious code injections: Attackers exploit insecure scripts to plant skimmers (Magecart) or cryptominers
- It also creates openings for client-side attacks like cross-site scripting (XSS), where malicious code is injected and executed in the user’s browser [source].
- Operational fragility: Updates or removals by third-party vendors can break functionality or introduce bugs
Shadow code also erodes user trust—especially if unauthorized trackers or pop-ups appear.
How to Detect and Manage Shadow Code
Best practices for managing shadow code:
- Use JavaScript runtime monitoring: Capture what code actually executes in user browsers (not just what’s in your repo).
- Apply CSPs (Content Security Policies): Limit which scripts can run or connect outbound.
- Inventory all scripts: Continuously scan and map first, third, and fourth-party code.
- Set change detection alerts: Know when new scripts are injected or behaviors shift.
- Audit tag managers regularly: Ensure only approved containers and scripts are active.
- Align with compliance controls: PCI DSS 4.0 now explicitly requires detection of unauthorized script changes.
FAQ
What is an example of shadow code?
A heatmap script added via Google Tag Manager without your dev team’s knowledge is shadow code—it runs client-side but is unmanaged.
How is shadow code different from shadow IT?
Shadow IT involves unauthorized hardware or software; shadow code refers to unapproved scripts or code running in your browser environment.
Is shadow code always malicious?
No. Most shadow code isn’t intentionally harmful, but it’s still risky because it bypasses security and compliance processes.
How do I prevent shadow code in my web apps?
Use runtime monitoring tools, lock down tag managers, enforce CSP headers, and continuously audit all front-end scripts.
Does PCI DSS 4.0 address shadow code?
Yes. Requirement 6.4.3 and especially 11.6.1 require monitoring for unauthorized changes to browser-executed scripts.


