SOC 2 compliance refers to a framework developed by the American Institute of Certified Public Accountants (AICPA) for managing customer data based on five “Trust Services Criteria”: security, availability, processing integrity, confidentiality, and privacy.
Designed specifically for SaaS and cloud-based service providers, SOC 2 ensures that an organization’s systems are designed to keep sensitive data secure.
What does SOC 2 Compliance Mean?
SOC 2 compliance ensures that a service provider’s data management practices meet rigorous security and privacy standards. It evaluates how well a company’s controls align with the AICPA’s Trust Services Criteria, which include:
- Security: Protection against unauthorized access.
- Availability: System uptime and performance monitoring.
- Processing Integrity: Accuracy and completeness of operations.
- Confidentiality: Data is accessible only to authorized parties.
- Privacy: Protection of personal information.
Key Components of a SOC 2 Audit
A SOC 2 audit is performed by an independent CPA or accredited audit firm. The audit includes:
- A detailed review of internal controls and policies.
- Assessment of risk mitigation and incident response plans.
- Evidence collection over a specific period (for Type II).
- A final SOC 2 report detailing the effectiveness of controls.
The result is a valuable tool for demonstrating your organization’s commitment to information security and compliance.
SOC 2 Type I vs. SOC 2 Type II
SOC 2 Type I and Type II reports differ primarily in scope and duration. SOC 2 Type I assesses the design of security controls at a specific point in time, offering a snapshot of how those controls are structured. In contrast, SOC 2 Type II evaluates how effectively those controls operate over a defined period—typically ranging from 3 to 12 months—providing insight into their consistent implementation.
SOC 2 Type II reports offer greater assurance to clients, especially for long-term data security practices.
Who Needs SOC 2 Compliance?
SOC 2 is essential for any technology service provider that processes or stores customer data, including:
- SaaS providers
- Cloud computing platforms
- Data analytics firms
- Managed service providers (MSPs)
- Financial technology companies
SOC 2 certification is often a requirement for vendor onboarding, especially in regulated industries like healthcare, finance, and legal.
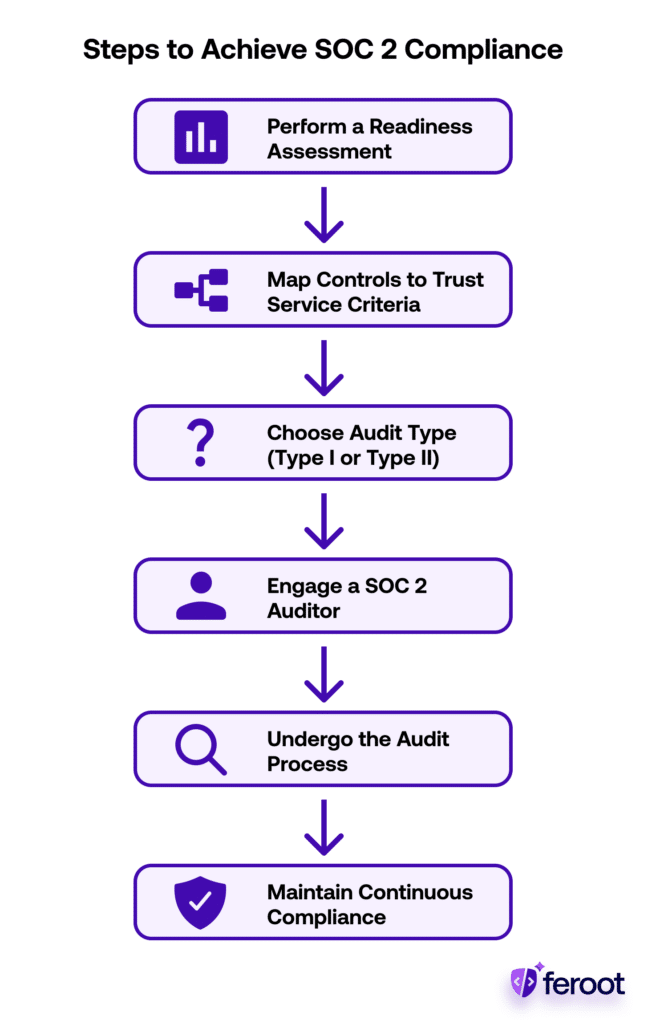
Steps to Achieve SOC 2 Compliance
- Perform a Readiness Assessment: Identify existing gaps in your current internal controls and document remediation steps.
- Map Controls to Trust Services Criteria: Implement technical and administrative controls aligned with AICPA guidelines.
- Choose Audit Type (Type I or Type II): Decide based on business goals and customer requirements.
- Engage a SOC 2 Auditor: Select a reputable CPA or audit firm with SOC 2 experience.
- Undergo the Audit Process: Prepare documentation, respond to inquiries, and validate system behaviour.
- Maintain Continuous Compliance: Build compliance into operations to retain certification long term.
Conclusion
SOC 2 compliance isn’t just a checkbox—it’s a powerful framework for establishing trust, minimizing risks, and securing sensitive data. For SaaS and cloud providers, it’s often essential for growth, partnerships, and enterprise credibility.