TL;DR
- Infostealer malware uses client-side attacks — drive-by downloads, fake updates, and malicious ads — to silently steal credentials and sensitive data.
- Even “safe” websites can become delivery mechanisms if their front-end is compromised.
- RedLine, Raccoon, and Lumma Stealer are among the top malware families exploiting insecure web environments.
- Traditional endpoint or server-side protections miss these client-side threats.
- Feroot’s client-side security platform blocks unauthorized scripts, detects malicious behavior in real time, and helps teams meet PCI DSS, HIPAA, and GDPR requirements.
Why Are Infostealer Attacks So Hard to Detect?
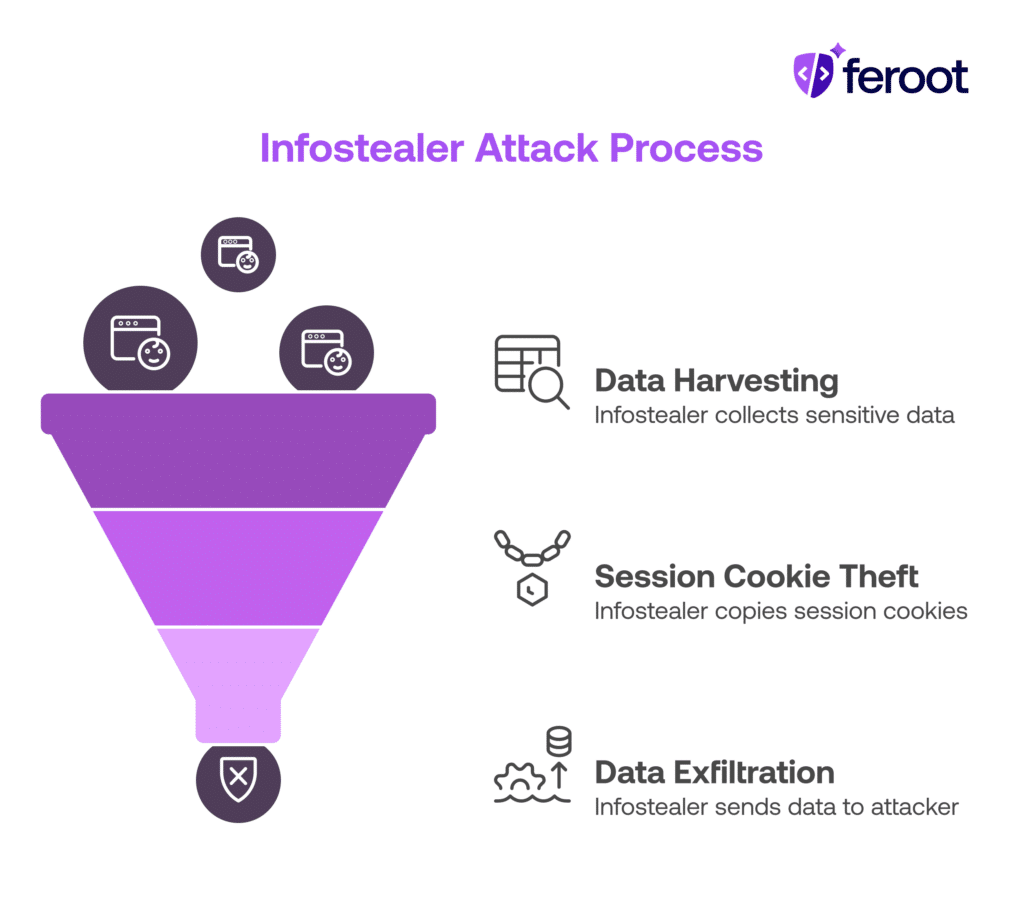
Infostealers don’t behave like traditional malware. They work silently in the browser — the client side — harvesting saved passwords, session tokens, credit card data, and more.
Attackers use common browser behaviors (JavaScript execution, third-party scripts, DOM manipulations) to:
- Hook into autofill and form fields
- Copy session cookies
- Exfiltrate data to attacker-controlled servers
These threats often bypass traditional server-side or endpoint protection, making them invisible to most security tools unless you’re monitoring the browser itself.
How Do Websites Become Vectors for Infostealer Malware?
What Is a Drive-By Download Attack?
Drive-by downloads exploit browser vulnerabilities or compromised scripts on websites. A user visits a page — no clicks required — and malware is downloaded via a hidden iframe, JavaScript loader, or misused third-party library.
This tactic is especially dangerous because:
- The site may be legitimate (e.g., news, shopping, software)
- No user action is required
- Endpoint protection often misses browser-based delivery
How Does Malvertising Install Malware?
Malvertising (malicious advertising) tricks users into clicking fake software offers, games, or giveaways — but the click triggers malware instead.
Attackers embed malicious code in:
- Ads purchased via legitimate ad networks
- Pop-ups designed to impersonate trusted brands
- Redirect chains that load obfuscated scripts
Even major ad networks have unknowingly served malicious campaigns through poorly vetted partners.
Why Are Fake Browser Updates So Effective?
A top social engineering tactic is the “critical update” scam. The user sees a fake pop-up:
“Your browser is out of date – click to update now.”
Instead of a patch, the click triggers a malware dropper that installs a credential stealer like Lumma Stealer or RedLine.
These fake prompts are often injected into websites via:
- Compromised JavaScript libraries
- Third-party chat widgets or analytics tools
- Malicious redirects from user comments or embeds
What Infostealers Are Dominating the Threat Landscape?
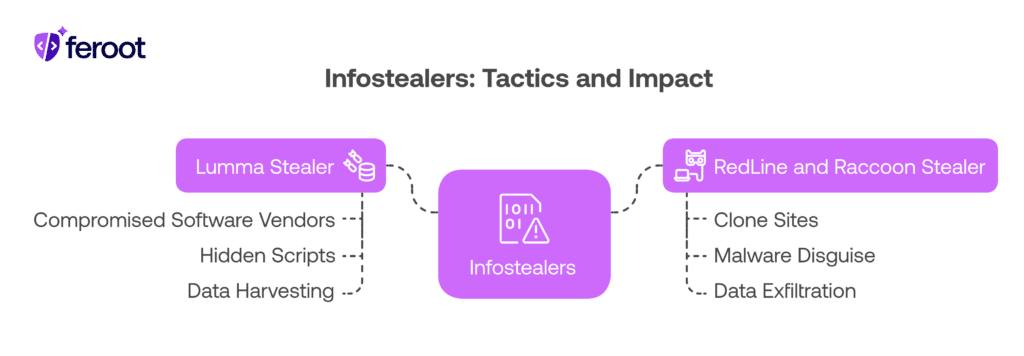
Lumma Stealer: Legitimate Websites, Hidden Payloads
In a 2025 campaign, attackers compromised popular software vendors. When users downloaded legitimate tools, hidden scripts installed Lumma Stealer, which immediately began:
- Harvesting browser-stored credentials
- Stealing clipboard contents
- Uploading stolen data to external servers
RedLine and Raccoon Stealer: The “Free Software” Trap
Attackers created clone sites offering cracked versions of Photoshop, Microsoft Office, and popular games. Victims unknowingly downloaded:
- Malware disguised as installation files
- Bundled infostealers alongside the legitimate app
- Background processes that silently exfiltrated banking credentials and photos
Why Traditional Tools Fail to Catch Client-Side Malware
Infostealers execute in the browser — not on the server or network perimeter. Most security solutions:
- Don’t monitor JavaScript behavior in real time
- Can’t detect DOM injections or credential harvesting
- Ignore third-party script behavior once loaded
This leaves a massive blind spot in your compliance and threat prevention programs — especially under PCI DSS 4.0, HIPAA, and GDPR.
How Does Feroot Help Stop Infostealer Malware at the Source?
Feroot protects your web applications where they’re most vulnerable — in the browser.
Why It Matters:
Client-side attacks are the #1 blind spot in modern web security. Compliance frameworks like PCI DSS 4.0 (Requirements 6.4.3 and 11.6.1) now explicitly require monitoring of client-side code changes and unauthorized script behavior.
What Feroot Does:
- Monitors and blocks unauthorized JavaScript in real time across your websites and apps
- Detects malicious code injections, fake update prompts, and credential harvesting attempts
- Maps risks to compliance requirements under PCI DSS, HIPAA, and GDPR
- Delivers audit-ready evidence with a full timeline of client-side script activity
- Integrates with your existing DevSecOps workflows for scalable protection
How Can Security Teams Mitigate the Risk of Infostealer Malware?
1. Monitor Client-Side Code
Use tools like Feroot to monitor, analyze, and control JavaScript running in browsers.
2. Harden Your Supply Chain
Audit all third-party scripts, tag managers, and libraries. Apply Subresource Integrity (SRI) where applicable.
3. Block Malicious Behavior at Runtime
Don’t just scan for malware — block execution of unknown or unapproved scripts as users interact with your site.
4. Educate End Users
Train users to avoid fake update prompts and pirated software — but don’t rely solely on awareness. Use technical controls.
What If You’re Already Infected?
If you suspect an infostealer is active:
- Immediately disconnect the infected device from the internet
- Run a malware scan using reputable endpoint protection
- Change all passwords from a clean device
- Investigate the origin: Was it a malicious ad, third-party script, or compromised download page?
- Start monitoring the front-end environment with Feroot to prevent recurrence
Conclusion: Protect the Part Most Tools Miss
Infostealer malware is designed to evade detection and exploit the modern web stack — especially where traditional tools fall short: the client side.
Feroot helps security teams:
- Stop silent credential theft in real time
- Maintain compliance with PCI DSS, HIPAA, and GDPR
- Eliminate blind spots in browser-based activity
FAQs
How does client-side security help prevent infostealer malware?
Infostealers live in the browser — client-side security tools like Feroot monitor, detect, and block the malicious scripts responsible for data theft.
Can Feroot help with compliance requirements?
Yes. Feroot supports PCI DSS 4.0, HIPAA, and GDPR by tracking client-side script behavior, alerting on unauthorized changes, and generating audit-ready reports.
What kinds of scripts does Feroot detect?
Feroot identifies and blocks risky behavior from:
- Shadow code
- Third-party analytics and ad scripts
- Malicious iframes and DOM-based attacks
Do we need Feroot if we already use endpoint protection?
Yes — endpoint protection doesn’t see what happens in the browser. Feroot complements your stack by securing the last-mile user experience.
Does Feroot integrate with our existing security stack?
Absolutely. Feroot integrates with cloud platforms, tag managers, CI/CD pipelines, and SIEM tools. It adds visibility and enforcement at the browser layer without disrupting your DevSecOps workflows.