How do you choose a tool that can actually show what third-party scripts are doing on your payment pages? It starts with recognizing the scale of what runs there.
What you’ll learn in this article
- How to evaluate a third-party script monitoring tool beyond simple script counts, including the three layers that matter for absolute payment page script security.
- How PCI DSS requirements in 6.4.3 and 11.6.1 translate into concrete capabilities: discovery, behavioral monitoring, change/tamper detection, and audit-ready evidence.
- How to compare vendors using practical, PCI-focused questions, avoid common pitfalls, and choose a solution that supports continuous compliance, not just audit-season prep.
Why script monitoring requires more than counting
More than 99% of websites use third-party code, and for many organizations, those scripts make up 50–70% of page functionality. And that’s where the gap becomes clear, that the browser often carries far more than what teams originally planned.
That’s why a useful monitoring tool has to go beyond counting scripts. It needs to see the full mix of third- and fourth-party code in the consumer’s browser and track how that behavior shifts over time.
PCI DSS 6.4.3 and 11.6.1 reflect this reality. They focus on knowing which scripts are present, why they’re authorized, and how you detect meaningful changes as pages are rendered.
This piece walks through what that requires in practice so you can choose a tool that aligns with PCI’s expectations.
What script monitoring actually means

At the simplest level, a third-party script monitoring tool is software that shows you which scripts are running in your users’ browsers and what they’re doing, especially on sensitive pages like checkout and login.
From a practical standpoint, there are three layers to consider.
The first is discovery. You need a clear view of all scripts that load on your payment pages, including third-party and fourth-party code. This is where PCI DSS 6.4.3 begins: it expects you to maintain an inventory of payment page scripts and to have a business justification for each one.
The second layer is behavioral understanding. It is not enough to know that “live-chat.js” is present. A functional PCI DSS script monitoring capability will show that your chat widget is reading form fields, interacting with specific DOM elements, and making requests to external domains. That level of insight is what makes payment page script security meaningful rather than theoretical.
The third layer is browser-based change management. PCI DSS 11.6.1 introduces a requirement for change and tamper detection on payment pages as they are rendered to the consumer. In practical terms, that means being able to see when a benign analytics script first reads card fields or when a new domain appears in checkout network calls.
To comply with PCI DSS 6.4.3, you need to demonstrate that scripts are authorized and inventoried.
For 11.6.1, you need to show that you are evaluating those scripts and detecting unauthorized modifications over time. Together, these layers move you from a static list of filenames to accurate monitoring: continuous understanding of which scripts are present, what they do, and when they change in ways that could affect cardholder data.
Essential capabilities to evaluate
When you evaluate a third-party script monitoring tool, you are really asking one question: Will this help my team understand, control, and prove what scripts are doing on our payment pages in a way that stands up to PCI DSS scrutiny?
That answer depends on a few core capabilities that should work together, not in isolation. Let’s explore them.
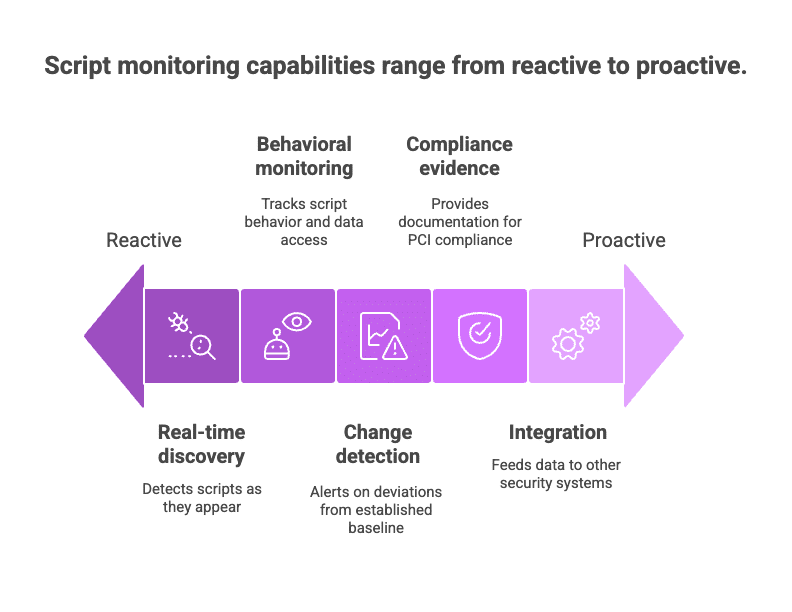
Real-time discovery
A natural place to begin is simple discovery. Most teams want a clear view of every script that runs in the browser across their key flows, including first-, third-, and fourth-party code that vendors introduce. That view becomes more useful when it shows when a script first appeared, which pages it touched, and how its footprint has changed over time.
Another useful angle is how consistently the tool identifies the same script across releases. Payment pages change often, and stability in the inventory makes it easier to keep PCI records aligned without extra reconciliation. For PCI DSS 6.4.3, QSAs usually look for an inventory that reflects what is actually on the payment page, with timestamps and ownership, rather than a spreadsheet that drifts out of date.
Behavioral monitoring
The second capability is behavioral monitoring. It is not enough to know that a script exists; PCI DSS 6.4.3 is explicit that you must understand and justify what it does on payment pages. That means tracking data access, network activity, DOM manipulation, and storage patterns in the browser.
In real Magecart campaigns, skimmers often stay dormant until the final checkout step, then activate only when all card fields are present. A good monitoring platform should show you that pattern: which scripts read payment fields, which endpoints they contact, and under what conditions.
Change detection
Change detection is the third pillar. Scripts change frequently, and PCI DSS 11.6.1 requires you to detect unauthorized modifications to payment page content and scripts as they are rendered to customers. A helpful tool will establish a baseline and then alert when behavior deviates in meaningful ways.
Hash verification for static resources can help, but the real value lies in contextual alerting that distinguishes a planned release from a suspicious alteration. When you evaluate tools, it is reasonable to look into how they model an update versus a threat and what signals they use to make that distinction.
Compliance evidence
The fourth capability is compliance evidence. For environments that handle cardholder data, PCI compliance is mandatory, and auditors will look beyond marketing claims. You will want clear support for PCI DSS 6.4.3 and 11.6.1, including documentation that shows how script inventory, authorization, integrity checks, and tamper detection are implemented.
Audit-ready reports that tie each script to a business justification, a change history, and a monitoring record over time are beneficial to a QSA. The ability to demonstrate continuous monitoring, not just an annual assessment, is what gives this tool category its real value.
Integration
A script monitoring tool works best when it fits into the systems you already use. Most teams want their findings to flow into GRC, SIEM, CI/CD, and ticketing tools so that activity is recorded in the right places and audit evidence builds naturally over time.
Export capabilities for reports, inventories, and timelines will make PCI reviews far less painful. In the end, you are not buying a dashboard. You are putting in place a system that helps you see what your scripts are doing on payment pages, respond when something looks wrong, and prove to yourself and your assessors that those controls are working.
Deployment models
When comparing deployment models, it helps to be honest about what each can and cannot prove. Agent-based or tag-based approaches sit inside the browser and see what real users see. They require code deployment, but they are often the most direct way to show a QSA that you are evaluating payment page scripts “as received by the consumer’s browser,” as PCI DSS 11.6.1 expects.
Gateway and proxy models sit at the edge, which simplifies deployment but limits native visibility into client-side behavior. Without some form of rendering or client-side component, a proxy-only approach will often struggle to detect tampering in the browser accurately. Hybrid models combine both views and tend to be the most comprehensive, although they are also more complex to operate.
There is no single model that fits everyone. Still, organizations that process payments typically gravitate toward agent-based or hybrid designs because they generate the kind of continuous, browser-side evidence assessors now look for under PCI DSS 6.4.3 and 11.6.1.
Critical vendor questions
Most demos show you a clean lab environment. Real life is different. When evaluating a third-party script monitoring tool, the right questions reveal how it behaves in your actual checkout flows and whether it can provide PCI evidence without creating busywork.
Detection
You want to know whether the engine truly sees what matters.
- Can you detect dynamically loaded scripts, including those in SPAs and tag managers?
- Can you handle minified or bundled JavaScript, not only readable, but also separate files?
- How do you track changes to CDN-hosted content when the URL stays the same?
Behavioral monitoring
For meaningful PCI DSS 6.4.3 compliance, you need more than a list of scripts.
- How do you establish behavioral baselines for scripts on payment pages?
- Can you detect behavior changes even when the script hash or filename does not change?
- How do you surface patterns like a Magecart-style script that only activates on the final checkout step?
This is the difference between simple detection and proper security for payment page scripts.
False positives
Another area worth understanding is how the tool handles noise. Every environment sees routine vendor updates, small shifts in behavior, and the kind of low-impact changes that do not need attention.
That’s why a monitoring platform is most helpful when it can filter that out and surface only what is meaningful on payment pages. In practice, this comes down to how often alerts fire in production, how flexible the tuning model is, and whether the system can distinguish expected movement from activity that deserves a closer look.
Compliance and audit evidence
PCI-specific questions reveal whether the tool is ready for PCI audits. Some platforms map their reports directly to the language in PCI DSS 6.4.3 and 11.6.1, while others require additional interpretation.
So while evaluating a platform, ask:
- Do your reports map directly to PCI DSS 6.4.3 and 11.6.1 language?
- Have customers successfully passed PCI assessments using your evidence?
- Can you export historical script inventories with business justification and authorization status?
Edge cases
Edge cases tend to reveal how mature a script monitoring tool really is. Conditional scripts, cross-domain iframes, and multi-step flows can behave differently from simple pages, and a useful platform needs to pick up those nuances without adding noise.
It is also worth understanding how the tool keeps findings clean when browser extensions appear in the mix. These small areas often determine whether the monitoring model holds up in day-to-day use.
Common pitfalls
There are a few common pitfalls that tend to show up when teams evaluate or deploy script monitoring tools. They are subtle, but understanding them early makes the work smoother.
Counting without context
A pattern we see often is relying on a tool that can count scripts but does little beyond that. An inventory is useful, but PCI DSS 6.4.3 expects teams to understand why each script is present and how its integrity is managed. A platform that reports “how many” without helping you track purpose and approval tends to leave that picture incomplete.
Partial coverage
Another area that causes friction is treating partial coverage as if it were full coverage. PCI DSS 6.4.3 focuses on inventory and authorization. Requirement 11.6.1 adds change and tamper detection in the browser. When a tool handles one well but not the other, you still have to explain the gap during an assessment.
Operational alignment
Operational work is also easy to underestimate. Script justifications, approvals, and monitoring records need to stay aligned as the environment evolves. When the tool does not support that flow, teams often find themselves stitching together the story in spreadsheets before each audit.
Testing the wrong pages
We also see teams test only the homepage. PCI assessors focus on payment pages and any place where cardholder data is entered. Fourth-party scripts on those pages are treated the same as first-party code and still require authorization and monitoring.
Monitoring cadence
Both 6.4.3 and 11.6.1 point toward regular monitoring rather than one-off scans. The challenge usually shows up when a tool cannot produce evidence across the full assessment period, which leads to late-cycle reconstruction and extra manual work.
Industry-specific priorities
E-commerce
For retail, the priority is to protect the checkout process and stay within PCI requirements. A third-party script monitoring tool should focus on payment page coverage, Magecart attack prevention, and clear evidence for PCI DSS 6.4.3 and 11.6.1. The goal is simple: show exactly which scripts run on checkout and how you detect unauthorized changes.
Healthcare
Healthcare teams care as much about privacy as they do about card data. Monitoring needs to catch PHI leakage through pixels, analytics tags, and patient portal widgets, while supporting HIPAA risk assessments. The same client-side visibility that supports PCI can also reveal where sensitive visit or identifier data is leaving the browser.
Financial services
Banks and fintechs usually bring stricter controls and heavier stacks. Here, script monitoring must integrate with existing SIEM, GRC, and change management systems while supporting SOC 2 and PCI objectives. The deployment model needs to be secure, auditable, and compatible with locked-down environments and strict network egress rules.
SaaS
For SaaS providers, script behavior spans multiple domains, environments, and customer tenants. A monitoring tool should handle complex front ends, developer workflows, and frequent releases without slowing teams down.
Strong APIs, CI/CD integration, and scalable data collection matter as much as dashboards, because engineering often owns the browser layer.
Media and publishing
Media sites carry a high script load from ad networks, analytics, and personalization. Priorities include privacy-law alignment, performance, and controlling third-party behavior in crowded pages. Monitoring should help teams see which tags affect user data, how they impact load time, and where script chains pull in unvetted partners.
Total cost of ownership
When evaluating a third-party script monitoring tool, the price on the slide is only the starting point. Total cost of ownership is determined by how the product is licensed, how hard it is to deploy, and how much effort it takes to run day to day.
Vendors will usually frame licensing around a few variables: domains in scope, pageviews, number of scripts, or a flat subscription. None of these models is inherently good or bad, but they influence how you think about growth.
Implementation is the second component. You will want a clear view of professional services costs, internal engineering time, and any work needed in tag managers or templates. If the tool cannot be rolled out to payment pages without constant developer intervention, the friction will show up in delayed projects.
Operational cost is where many teams feel the real impact. Alert triage, false positive handling, and tuning all require time.
The most expensive tool is not always the most costly decision. A cheaper product that generates constant manual work can be far more expensive in practice than a solution that reduces operational burden and produces audit-ready evidence with less effort.
Making the Decision
When you reach the point of choosing a third-party script monitoring tool, it helps to keep the sequence clear in your mind,
- First: Does it work?
- Second: Can your team run it?
- Third: Will it stand up to a PCI review?
Effectiveness comes first. The tool has to discover scripts in the browser, understand their behavior on payment pages, and detect unauthorized changes in a way that genuinely supports PCI DSS 6.4.3 and 11.6.1. If that foundation is weak, everything else is negotiation around a gap.
Operational fit comes next. Ask whether your team can live with this platform day to day. Can it integrate with your SIEM and ticketing systems? Can you tune alerts without a project, and will it help you maintain script inventories and justifications without rebuilding spreadsheets before every audit?
Then look at compliance alignment. For PCI environments, a straightforward test is to ask: Can this tool help us pass our next audit and maintain continuous compliance between audits? That means:
- Document your use cases and PCI requirements up front, especially 6.4.3 and 11.6.1.
- Shortlist a small number of vendors who explicitly support PCI evidence generation.
- Run production POCs, ask for sample audit reports, and involve security, compliance, and audit prep stakeholders.
- Test alert accuracy, script inventory quality, and the ability to prove continuous monitoring over time.
In the end, choose a solution that helps you maintain compliance year-round, not just during audit season.
Staying ahead of E-skimming with Feroot PaymentGuard AI
Choosing a third-party script monitoring tool is ultimately about trust: can you see what is running on your payment pages, can you control it, and can you prove it when PCI auditors ask hard questions?
Feroot’s PaymentGuard AI is built for that reality. It gives your team real-time visibility into first-, third-, and fourth-party script behavior in the browser and ties it directly to PCI DSS 6.4.3 and 11.6.1 evidence.
It automates script discovery, behavioral monitoring, and tamper detection, and it generates the inventories and change records you need for PCI work. The result is a clearer audit trail without having to rebuild it each time.
If your goal is continuous compliance rather than a once-a-year scramble, request a demo and see PaymentGuard AI on your own checkout.