TL;DR
- PCI DSS 4.0.1 raises the certification bar with requirement 6.4.3 for script inventory and 11.6.1 for real-time change detection, making continuous client-side monitoring a must.
- The stakes are high for certification readiness: The average breach cost reached $4.88M in 2024 and 43% of attacks hit small businesses, so fines, remediation, and lost trust add up fast.
- A clear certification path works best: Scope your environment, map cardholder data flows, run a gap analysis, implement controls, complete SAQ or QSA assessments, and maintain continuous monitoring.
- Feroot’s PCI compliance platform strengthens certification outcomes by automatically monitoring scripts, detecting unauthorized changes in real time, and producing audit-ready evidence that speeds PCI DSS 4.0.1 approval.
The stakes for protecting payment data have never been higher. In 2024, the global average cost of a data breach reached $4.88 million, a 10% increase over the previous year (IBM).
For any business handling credit card transactions, PCI DSS compliance certification is essential to safeguard customer trust, meet regulatory obligations, and prevent costly breaches.
With the release of PCI DSS 4.0.1, organizations face new challenges, especially with requirement 6.4.3 (script inventory and management) and requirement 11.6.1 (change detection on payment pages). These updates demand more visibility into client-side risks and stronger monitoring capabilities.
This guide provides a step-by-step roadmap for achieving certification, analyzing costs, and adopting automated solutions that simplify compliance while reducing risk.
What is PCI DSS Compliance Certification?
PCI DSS certification verifies that an organization meets the security requirements defined by the Payment Card Industry Security Standards Council (PCI SSC). This global framework, developed in collaboration with major card brands (Visa, Mastercard, American Express, Discover, JCB), sets strict standards to protect cardholder data.
Certification applies to:
- Merchants of all sizes that accept credit card payments
- Service providers processing or storing cardholder data
- Organizations managing payment infrastructure
Your compliance level depends on transaction volume:
- Level 1: Over 6 million annual transactions
- Level 2: 1–6 million annual transactions
- Level 3: 20,000–1 million e-commerce transactions
- Level 4: Fewer than 20,000 annual transactions
Why PCI DSS Certification is Critical for Your Business
Rising cyber threats and financial impact
Non-compliance is not just a regulatory issue; it is a financial risk. Data breaches involving payment card data can trigger:
- Non-compliance fines ranging from $5,000 to $100,000 per month
- Reputational damage that can permanently reduce customer trust
- Breach remediation costs averaging millions in incident response and legal fees
Regulatory requirements and business trust
Compliance is also about competitive advantage. Being PCI DSS certified demonstrates:
- Legal adherence to card brand rules and contractual obligations
- Customer confidence in the security of your payment systems
- Stronger partnerships with banks and payment processors who require certification
What are the New Requirements in PCI DSS 4.0.1?
PCI DSS 4.0.1 continues to enforce the 12 core requirements across six control objectives. However, two new controls stand out as particularly impactful:
- Requirement 6.4.3: Organizations must maintain a script inventory and manage all scripts executing on payment pages.
- Requirement 11.6.1: Businesses must deploy real-time change detection on payment pages to prevent unauthorized script injections or malicious alterations.
These requirements specifically target client-side risks, which traditional compliance programs often overlook. Manual methods like spreadsheets or quarterly scans are not sufficient to meet these continuous monitoring demands.
Enhanced Script Management and Change Detection
Payment environments are increasingly dependent on third-party scripts, plugins, and integrations. While they improve functionality, they also introduce risk.
Challenges include:
- Tracking every script that loads in the browser across multiple payment pages
- Detecting unauthorized or malicious modifications in real time
- Preventing supply chain attacks originating from vendors or compromised scripts
Without automation, compliance teams struggle to maintain the continuous oversight PCI DSS 4.0.1 requires.
The Complete PCI DSS Certification Process: 12 Essential Steps
- Understand the PCI DSS requirements – Review the 12 requirements and their objectives.
- Determine your PCI compliance level – Identify whether you fall under Level 1, 2, 3, or 4.
- Document cardholder data flows – Map how cardholder data moves through your systems.
- Conduct a risk assessment – Identify vulnerabilities and evaluate risks.
- Perform a gap analysis – Compare your current controls to PCI DSS standards.
- Implement security controls – Apply necessary measures like encryption, firewalls, and monitoring.
- Execute quarterly vulnerability scans – Test network and application security.
- Complete the Self-Assessment Questionnaire (SAQ) – Document compliance for lower levels.
- Conduct internal audits – Ensure controls are working as designed.
- Schedule an external QSA assessment – For Level 1 merchants and service providers.
- Achieve certification – Obtain the Attestation of Compliance (AOC) or Report on Compliance (ROC).
- Establish continuous monitoring – Maintain compliance with ongoing testing and monitoring.
How Automated Solutions Simplify PCI DSS 4.0.1 Compliance
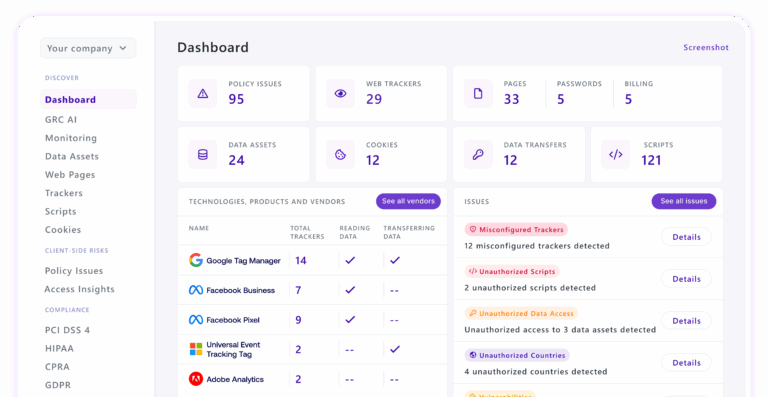
Automated script inventory management (Requirement 6.4.3)
Automation continuously catalogs every script executing on payment pages, ensuring complete visibility. This eliminates manual effort and helps detect unauthorized or unapproved scripts immediately.
Real-time change detection (Requirement 11.6.1)
Automated monitoring flags any change to payment pages in real time. Compared to periodic manual reviews, this ensures faster detection and prevention of malicious activity.
Continuous monitoring and compliance reporting
Automation also ensures:
- Ongoing compliance with continuous evidence collection
- Audit-ready reports that reduce preparation time
- Lower resource strain on internal teams
How Feroot’s AI Agent Platform Helps with PCI DSS 4.0.1
Feroot’s PaymentGuard AI gives CISOs and compliance leaders the visibility and automation they need to meet requirements 6.4.3 and 11.6.1 without adding overhead.
- Monitors and inventories every script on payment pages
- Detects unauthorized script changes in real time to prevent data theft
- Maps compliance gaps directly to PCI DSS requirements for faster remediation
- Generates audit-ready evidence to streamline certification and re-assessments
With Feroot, organizations accelerate PCI DSS readiness, reduce audit preparation time, and protect their payment environments from client-side risks that traditional compliance tools miss.
FAQ
Who needs PCI DSS certification?
Any entity that stores, processes, or transmits payment card or cardholder data must comply with PCI DSS. This includes merchants of all sizes who accept credit, debit, or other PCI‐brand cards and service providers (payment processors, gateways, hosting providers, cloud services, etc.) that handle cardholder data or whose systems affect the security of cardholder data. Even if a business outsources much of its card handling (e.g., using third‐party payment processors), there are still parts of PCI DSS that apply (e.g., ensuring the provider is compliant, securing the connections, etc.)
How long does PCI DSS certification last?
The Attestation of Compliance (AoC) or similar validation of PCI DSS compliance is generally valid for one year. After that, you must re‐validate via SAQ or Report on Compliance, a comprehensive document produced by a Qualified Security Assessor (QSA) – depending on your level – to maintain compliance.
What happens if I’m not PCI DSS compliant?
Consequences of non-compliance can include:
1. Fines and penalties from card brands or acquirers – Non-compliant merchants or service providers may be fined by card brands (Visa, Mastercard, etc.) or their acquiring bank. These can vary by the severity of non‐compliance, how long it has persisted, and whether there has been a breach.
2. Increased liability in case of a breach – If there is a data breach involving cardholder data, being non‐compliant can worsen legal/regulatory exposure, lead to class actions, regulatory scrutiny, increased compensation costs, and loss of trust.
3. Loss of ability to process cards or higher costs – Your acquiring bank or payment brand may refuse to let you accept cards until you become compliant. Or they may impose higher fees, require remediation plans, etc.
4. Reputational damage – Customers, partners, and investors may lose trust if you are considered insecure. Publicized breaches especially damage reputation.
How long does PCI DSS certification take?
It depends on the size of the business, the complexity of the environment, and how many of the required controls are already in place. Smaller businesses often average around 6 months, while big/complex merchants or service providers (Level 1) can be longer (sometimes up to 12 months), especially if there are significant gaps to remediate.
What is a QSA assessment?
QSA stands for Qualified Security Assessor. This is an individual (and firm) approved by the PCI Security Standards Council (PCI SSC) to perform formal, external audits of an entity’s PCI DSS compliance. A QSA assessment (often resulting in a Report on Compliance, RoC) is a full audit by a QSA (or QSA company) of all relevant PCI DSS requirements. QSA assessments are required for merchants and service providers at the highest levels (e.g. Level 1) or when required by the card brand or acquiring bank.
What is a SAQ, and which one do I need?
SAQ refers to the Self‐Assessment Questionnaire. It’s a tool consisting of a set of questions you answer yourself to attest whether your environment meets PCI DSS requirements. It is used when a full QSA audit isn’t required (lower merchant/service provider levels or simpler card‐handling environments).
There are multiple types of SAQs. Which type you need depends on how you accept payments, whether you store cardholder data, whether your payment systems interact with other systems, etc.
Find the right SAQ type for your organization here.