TL;DR
- PCI DSS 11.6.1 requires real-time detection of unauthorized JavaScript changes on payment pages
- A “script change” includes any modification, injection, or replacement of client-side code—even by trusted third parties
- Manual checks and traditional CSP headers are not sufficient for meeting this requirement
- Feroot’s client-side monitoring automates script integrity checks and alerts security teams to unapproved changes
- Built for CISOs and security teams facing 4.0 audits, Feroot helps meet 6.4.3 and 11.6.1 without slowing DevSecOps
Why Did PCI DSS Add 11.6.1 in Version 4.0?
To address a rising attack vector: client-side JavaScript tampering on payment pages.
New in PCI DSS v4.0, Requirement 11.6.1 mandates that organizations:
“Deploy a method to detect and alert on unauthorized changes to HTTP headers and the contents of payment page scripts as received by the consumer browser.”
This shift acknowledges a long-standing blind spot: what actually executes in the customer’s browser—especially on payment pages—often differs from what was deployed by developers.
Common risks include:
- Script injection via compromised third-party libraries
- Shadow code added by marketing or analytics teams
- Malicious modifications via tag managers
- Supply chain attacks targeting JavaScript CDNs
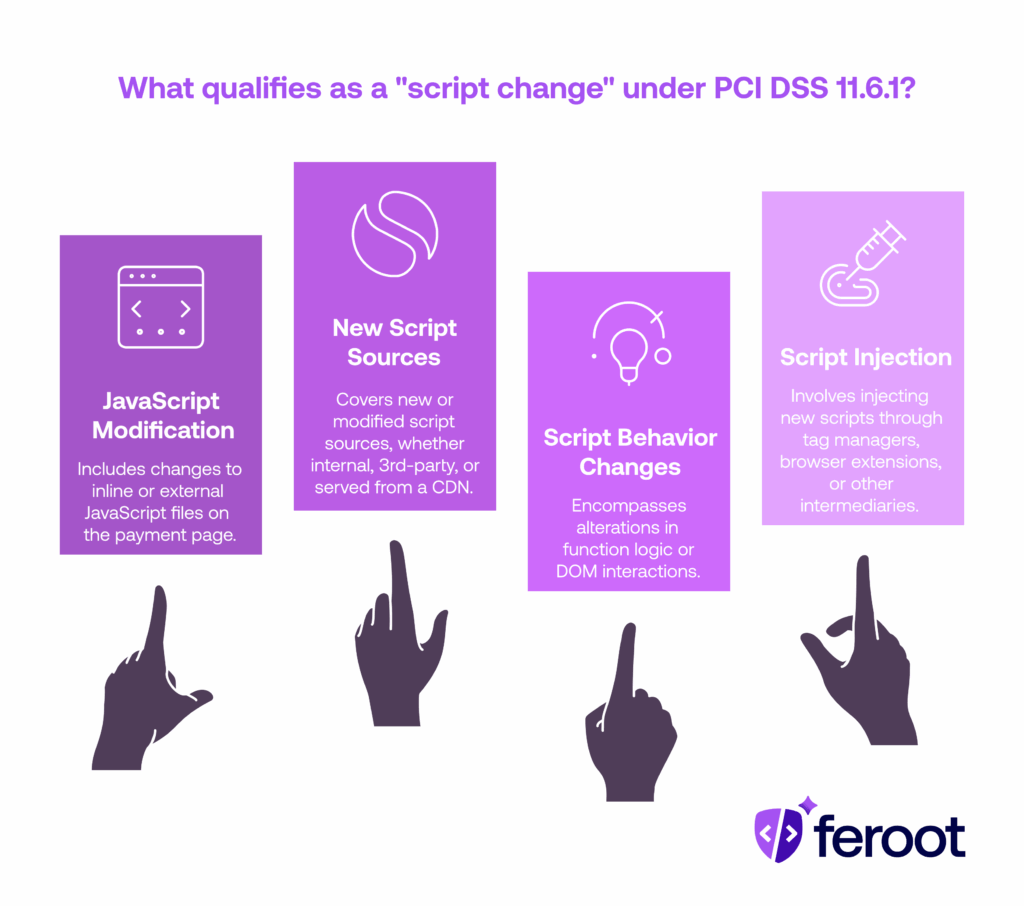
What Qualifies as a “Script Change” Under PCI DSS 11.6.1?
The standard does not restrict “script changes” to internal code.
In practice, a “script change” includes:
- Any modification to inline or external JavaScript files on the payment page
- New or modified script sources, whether internal, 3rd-party, or served from a CDN
- Changes to script behavior, such as altered function logic or DOM interactions
- Injection of new scripts through tag managers, browser extensions, or other intermediaries
Even legitimate changes (e.g., a new version of a 3rd-party payment SDK) must be monitored and authorized.
Per the PCI DSS 11.6.1 guidance:
“Organizations must be able to detect changes in real time and alert security personnel to unauthorized or unexpected script activity.”
Why Are Script Changes So Hard to Monitor with Legacy Tools?
Because most security and compliance tools don’t inspect the browser runtime environment—where PCI DSS 11.6.1 requires enforcement.
Limitations of traditional approaches:
- CSP headers are not dynamic — they can’t detect runtime injection or script modification
- Static code reviews or SAST tools stop at build-time, not execution-time
- WAFs and SIEMs don’t provide visibility into front-end JavaScript activity
- Manual page inspections don’t scale and miss real-time threats
Even DevSecOps workflows often skip client-side validation, leaving a gap between what’s shipped and what runs.
How Does Feroot Detect and Block Unauthorized Script Modifications?
Feroot’s client-side security platform is purpose-built for compliance with PCI DSS 6.4.3 and 11.6.1.
With Feroot, security teams can:
- Monitor all scripts executing in the browser, including inline, 3rd-party, and dynamically injected code
- Track real-time changes to JavaScript files, script sources, and HTTP headers
- Receive alerts for unauthorized modifications, including those caused by tag managers or CDN version drift
- Automatically classify changes as authorized or suspicious using AI-driven behavioral baselining
- Export audit-ready evidence reports to demonstrate compliance with PCI DSS 11.6.1 and 6.4.3
What Results Do Security Teams See with Automated Script Monitoring?
Security and compliance teams using Feroot report:
- Up to 90% reduction in manual payment page reviews
- Faster PCI DSS 4.0 readiness—from months to weeks
- Early detection of hidden or injected scripts from third-party vendors
- Passing PCI DSS audits with no remediations related to 11.6.1 or 6.4.3
“Feroot helped our team gain outside-in visibility into the security of the customer experience making our platform even more secure.”
— Ralph Pyne, Sr. Director, Information Security at Adroll
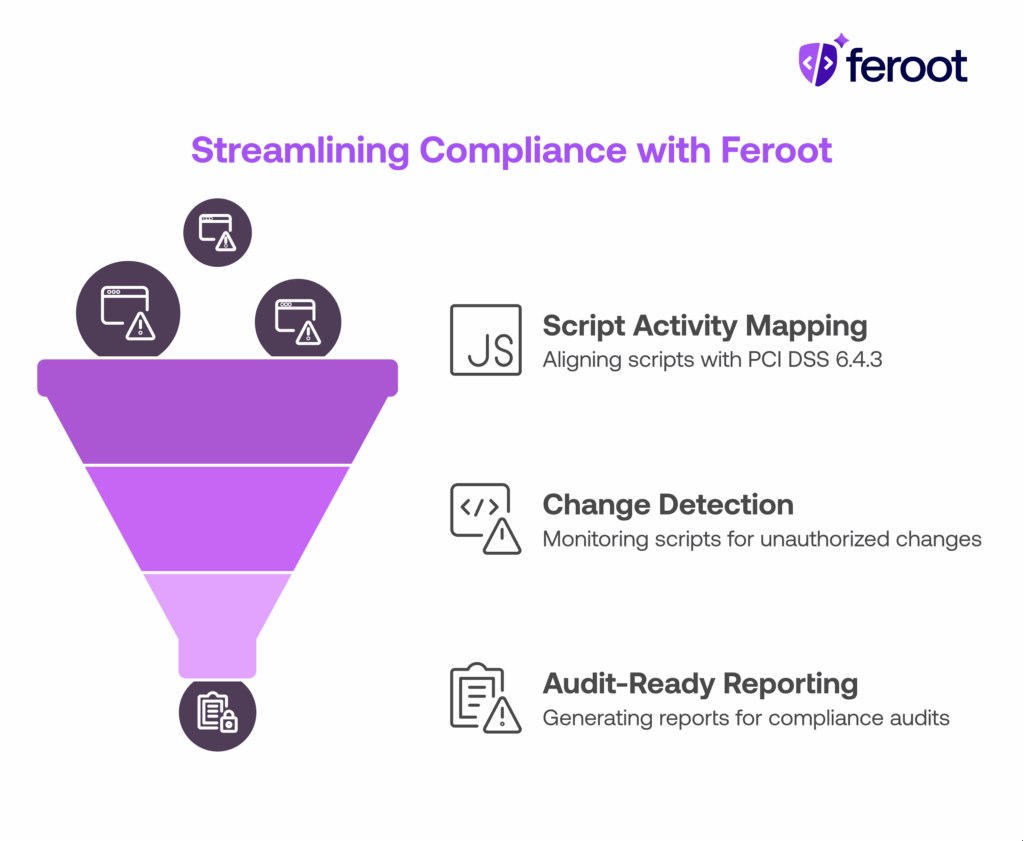
How Does Feroot Help CISOs Automate Compliance and Reduce Risk?
Feroot streamlines compliance with PCI DSS 11.6.1 and 6.4.3 by providing continuous visibility into the JavaScript that runs in your customers’ browsers.
Why this matters:
- Many PCI DSS violations originate from unmonitored client-side code
- Traditional tools stop at the server or build pipeline
- Feroot enforces compliance where it counts—at runtime
With Feroot’s platform:
- Map script activity to PCI DSS 6.4.3 (script authorization and approval)
- Monitor and alert per PCI DSS 11.6.1 (browser-side change detection)
- Produce audit-ready reports for every detected script change
“Feroot security gives us deep visibility into our website scripts, not just what is on the server, but the scripts that load from scripts that we were unaware of.” – Alex Bangle, Digital Developer, Enterprise
FAQ
What is considered an “unauthorized script change” under PCI DSS 11.6.1?
Any script modification not explicitly reviewed and approved—regardless of source.
How often do script changes need to be reviewed?
Real-time monitoring is expected. Manual periodic reviews no longer meet the requirement.
Does Feroot integrate with our CI/CD and DevSecOps tools?
Yes. Feroot integrates with CI/CD pipelines, SIEMs, and compliance platforms for continuous enforcement.
Is Feroot auditor-approved for PCI DSS 11.6.1?
Yes. Feroot provides exportable audit evidence mapped directly to PCI DSS controls.
Can we use Feroot for other compliance frameworks?
Yes. Feroot supports HIPAA, NIST, GDPR, and more with its client-side security monitoring.
Conclusion
Security leaders can’t meet PCI DSS 11.6.1 with traditional backend-focused tools. You need visibility into the browser—where malicious or unauthorized script changes happen.
Feroot gives you the automation, monitoring, and evidence collection needed to stay compliant with PCI DSS 6.4.3 and 11.6.1.
- Detect unauthorized script activity in real time
- Eliminate manual front-end checks
- Reduce audit prep time by weeks
- Prove compliance with zero gaps