TL;DR
PCI 6.4.3 and 11.6.1 are critical requirements for protecting payment pages from JavaScript-based attacks in e-commerce. JavaScript powers modern e-commerce but also exposes sites to digital skimming attacks. Common threats include supply chain compromises, Magecart injections, and CDN breaches. To combat this, PCI DSS 4.0 mandates script management and tamper detection. Protecting your payment pages with real-time monitoring tools and client-side security is essential for compliance and customer trust.
Introduction
As e-commerce continues to dominate the digital landscape, JavaScript scripts have become the backbone of modern online payment systems. However, these same scripts that enhance user experience and enable seamless transactions also represent one of the most vulnerable attack vectors for cybercriminals. Understanding how JavaScript scripts can be compromised is crucial for any organization processing credit card payments online. This guide will help you navigate PCI DSS 4 compliance for websites and explore payment page security solutions.
The Growing Threat of JavaScript-Based Attacks in E-commerce and the Need for E-skimming Prevention Tools
Modern websites depend heavily on JavaScript for analytics, payment processing, and user interactions. Unfortunately, this opens the door to e-skimming—attacks that skim credit card data in real-time from payment pages.
Why It’s Getting Worse
The Payment Card Industry Security Standards Council (PCI SSC) responded to this trend with PCI DSS 4, introducing key mandates like:
- Requirement 6.4.3: Managing and authorizing JavaScript
- Requirement 11.6.1: Detecting unauthorized script changes
These updates reflect the increasing sophistication of attackers and the urgent need for active script monitoring.
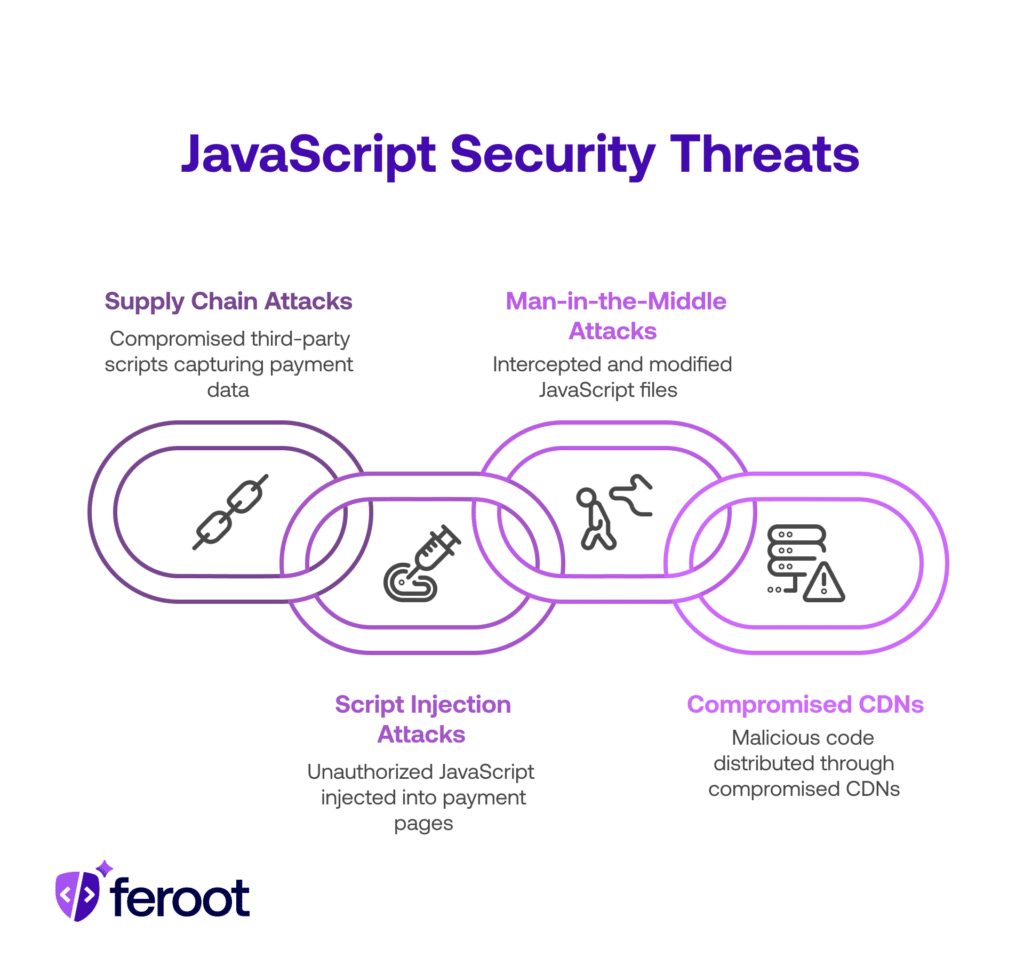
Common Ways JavaScript Scripts Get Compromised: Understanding Malicious Script Detection
1. Supply Chain Attacks (Third-Party Script Compromise):
Supply chain attacks represent one of the most significant threats to e-commerce security. Many websites load JavaScript from third-party service providers for functions like payment processing, analytics, and customer support. When attackers compromise these third-party scripts, they can insert malicious code that captures payment data without the merchant or third-party provider immediately detecting the breach. This highlights the importance of malicious script detection tools.
2. Script Injection Attacks (Magecart/Formjacking):
Script injection attacks, also known as Magecart or Formjacking attacks, involve attackers directly injecting unauthorized JavaScript into payment pages. These attacks can occur through compromised content management systems (CMS), vulnerable plugins, or cross-site scripting (XSS) vulnerabilities. Once injected, these malicious scripts can capture payment card data and transmit it to attacker-controlled domains. Magecart attack prevention software PCI DSS 4.0 is vital for mitigating these risks.
3. Man-in-the-Middle (MITM) Attacks:
Attackers can intercept and modify JavaScript files as they’re transmitted between servers and browsers, injecting malicious code that steals payment information.
4. Compromised Content Delivery Networks (CDNs):
When CDNs hosting JavaScript libraries are compromised, malicious code can be distributed to thousands of websites simultaneously.
Types of E-skimming Attacks
Silent Skimming
In silent skimming attacks, malicious scripts operate transparently in the background. Customers complete their transactions normally, with no indication that their payment data is being stolen. These attacks are particularly dangerous because they can persist undetected for extended periods. This underscores the need for robust secure payment processing compliance.
Double-Entry Skimming
Double-entry attacks present customers with fake payment forms before the legitimate checkout process. While often discovered more quickly, they can still result in significant data theft.
PCI 6.4.3 and 11.6.1: Your Compliance Roadmap for Securing Payment Pages
Requirement 6.4.3: Payment Page Script Management
This section mandates:
- Authorization: Only approved scripts should run
- Integrity: Scripts must not be tampered with
- Inventory: Maintain a full list of scripts with clear justification
Requirement 11.6.1: Change and Tamper Detection
This requires:
- Alerts for unauthorized changes to scripts or HTTP headers
- Weekly monitoring or risk-based scheduling
- Use of script monitoring and tamper detection tools
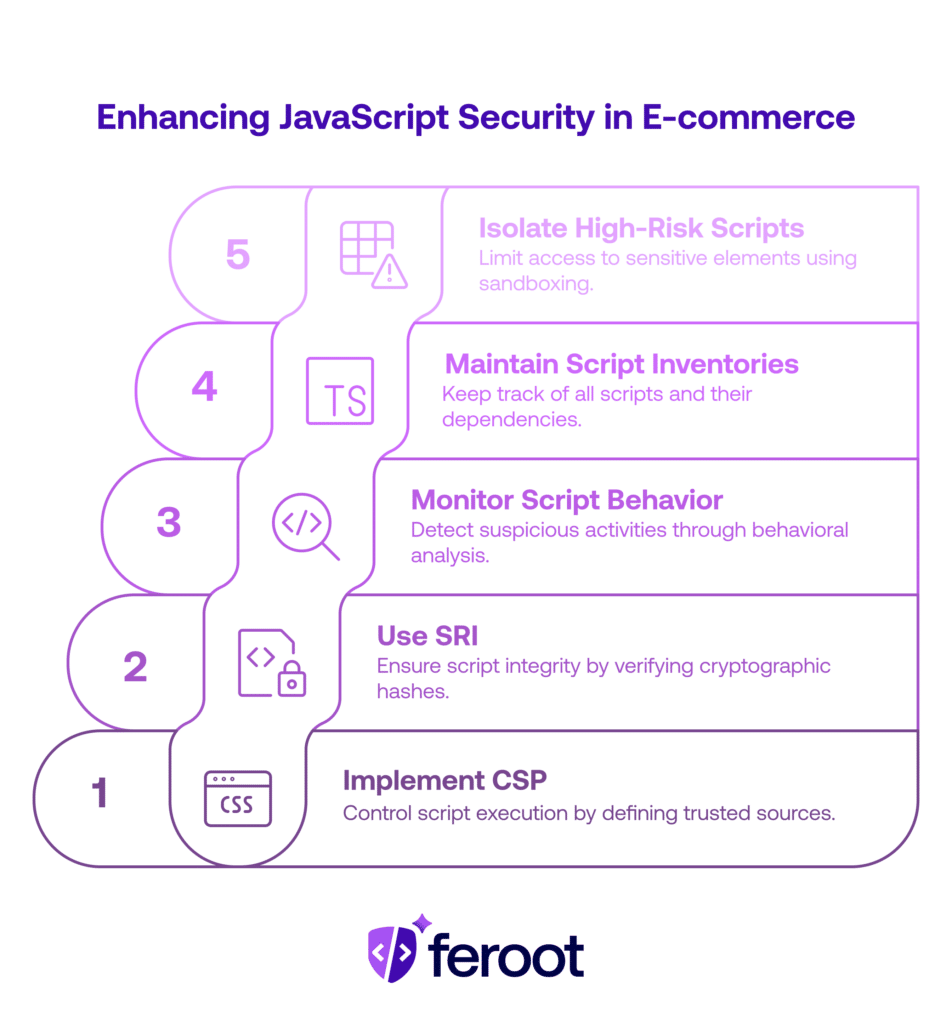
Best Practices for JavaScript Security in E-commerce: Leveraging Client-Side Protection
Implementing client-side protection platform PCI DSS 4 is key to a robust security posture.
1. Implement Content Security Policy (CSP)
CSP is a powerful browser security feature that allows you to control which scripts can execute on your pages and define trusted sources for JavaScript files, effectively blocking unauthorized script execution.
2. Use Sub-resource Integrity (SRI)
SRI helps ensure that third-party scripts haven’t been tampered with by comparing cryptographic hashes of loaded scripts and blocking execution if they don’t match.
3. Monitor Script Behavior
Implement behavioral monitoring to detect suspicious script activities such as unexpected data collection from payment fields or communication with unauthorized domains. This is part of comprehensive website payment page integrity monitoring tools.
4. Maintain Script Inventories
Keep comprehensive inventories of all scripts used on payment pages, including their sources, purposes, and risk assessments for third-party dependencies.
5. Isolate High-Risk Scripts
Use iframe sandboxing and cross-origin isolation to limit script access to sensitive page elements and reduce the attack surface for malicious code.
Implementing Effective Monitoring Solutions: Top Software for Securing Payment Pages
To effectively secure your payment pages, consider deploying top software for securing payment pages.
Real-Time Monitoring
Deploy monitoring solutions that can detect script changes in real-time, alert security teams to suspicious activities, and automatically block unauthorized script execution. These are integral to PCI DSS 4 11.6.1 detection tools.
Regular Security Assessments
Conduct periodic assessments including static code analysis, dynamic testing of script behaviors, and penetration testing of payment page security.
The Role of Third-Party Service Providers: Best PCI DSS 4 Compliance Tools for E-commerce
When working with third-party service providers (TPSPs) for payment processing, it’s crucial to utilize the best PCI DSS 4 compliance tools for e-commerce.
- Verify PCI DSS Compliance: Ensure your TPSP maintains current PCI DSS certification.
- Understand Responsibility Matrices: Clearly define which security controls are managed by you vs. your TPSP.
- Implement Secure Integration: Follow TPSP security guidelines for iframe implementation and script integration.
- Monitor TPSP Communications: Stay informed about security updates and potential vulnerabilities.
Building a Comprehensive Security Strategy: Leading Software for PCI DSS 4.0 Requirements 6.4.3 and 11.6.1
For robust protection, consider leading software for PCI DSS 4.0 requirements 6.4.3 and 11.6.1.
Small Merchants
Partner with PCI-compliant payment processors that provide secure, embedded payment solutions, implement basic CSP policies, and use automated monitoring tools designed for small businesses.
Large Enterprises
Develop comprehensive script management policies, implement enterprise-grade monitoring and detection systems, conduct regular security training, and establish incident response procedures specific to e-skimming attacks.
Conclusion: Protecting Your E-commerce Business with Robust Payment Page Security
According to the Verizon Data Breach Investigations Report, web application attacks—including those targeting JavaScript—remain a top cause of data breaches and one of the most serious threats to e-commerce. With the rise of digital skimming, PCI DSS 4.0 offers a much-needed framework for detecting and preventing these attacks.
Success requires:
- Strong script authorization and inventory (6.4.3)
- Real-time tamper detection (11.6.1)
- Ongoing monitoring and proactive mitigation
FAQ
What are PCI DSS 6.4.3 and 11.6.1?
PCI DSS 6.4.3 requires organizations to manage all JavaScript on payment pages by authorizing scripts, ensuring integrity, and maintaining a full inventory.
PCI DSS 11.6.1 mandates tamper detection and monitoring for unauthorized script or header changes. Both requirements aim to prevent e-skimming and Magecart attacks.
How do JavaScript scripts get compromised?
Scripts can be compromised through supply chain attacks, formjacking (Magecart), CMS vulnerabilities, or compromised CDNs. These methods allow attackers to inject malicious code and steal payment data.
What is e-skimming?
E-skimming is a cyberattack where malicious JavaScript captures and exfiltrates payment data from online checkout pages in real-time. It’s often invisible to customers and hard to detect without monitoring.
What tools help meet PCI DSS 4.0 requirements?
Client-side security platforms like Feroot PaymentGuard AI help detect, prevent, and respond to unauthorized script changes. Other tools include CSP enforcement, SRI validation, and behavioral monitoring.
Why is script inventory important?
Maintaining a script inventory helps organizations track all JavaScript running on payment pages, justify their presence, and detect unauthorized or malicious additions—critical for PCI DSS 6.4.3 compliance.