TL;DR
- What it is: The NIST Cybersecurity Framework (CSF) and related Special Publications (e.g., NIST SP 800-53, 800-171) set U.S. standards for managing cybersecurity risk and protecting sensitive information.
- Why it matters: National Institute of Standards and Technology is the foundation for many federal, defense, and private sector security programs, including FedRAMP, CMMC, and supply chain risk management.
- Who it applies to: Federal contractors, defense suppliers, SaaS providers handling government data, financial services, healthcare, and enterprises seeking to align with a best-practice framework.
- Common pitfalls: Lack of visibility into client-side data flows, weak third-party script governance, insufficient audit evidence, and unmonitored shadow IT.
- How Feroot helps: Feroot provides continuous monitoring, mapping, and reporting of client-side risks—directly supporting NIST controls for data protection, monitoring, and incident response.
Does the National Institute of Standards and Technology Cybersecurity Framework (CSF) or NIST Special Publications apply to your business?
If your company works with the U.S. government, manages sensitive data, or seeks to align with recognized best practices, the answer is almost certainly yes.
National Institute of Standards and Technology requirements can be daunting. While many companies focus on firewalls, servers, and cloud environments, the client-side of the web application—where sensitive data is collected from customers and employees—is often left unprotected. This blind spot is a key compliance risk under NIST.
Feroot Security helps organizations go beyond PCI DSS and HIPAA by addressing these overlooked areas. Through continuous client-side monitoring, data flow visualization, and compliance reporting, Feroot aligns your web applications with NIST requirements—closing security gaps before auditors or attackers find them.
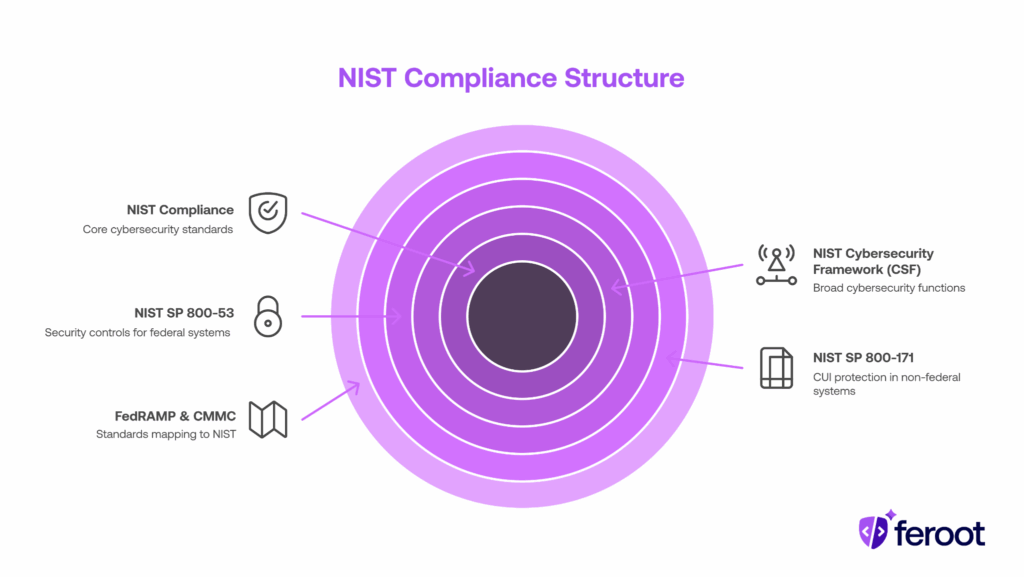
What Is National Institute of Standards and Technology Compliance?
The National Institute of Standards and Technology (NIST) is a U.S. government agency that develops cybersecurity standards used worldwide. While not a regulatory body itself, its frameworks and special publications underpin compliance for:
- NIST Cybersecurity Framework (CSF): Widely adopted, structured around five functions: Identify, Protect, Detect, Respond, Recover.
- NIST SP 800-53: Security and privacy controls for federal information systems.
- NIST SP 800-171 Rev. 3: Protecting Controlled Unclassified Information (CUI) in non-federal systems.
- FedRAMP & CMMC: Both map directly to NIST standards.
National Institute of Standards and Technology compliance applies to:
- Federal contractors and subcontractors (DoD, DHS, GSA, etc.)
- SaaS providers hosting government or sensitive data
- Healthcare, finance, and critical infrastructure sectors adopting NIST as a baseline
- Any business pursuing strong cybersecurity maturity or risk certifications
Key Compliance Requirements
Some of the most relevant National Institute of Standards and Technology controls that touch client-side security include:
- NIST CSF: PR.DS-5 – Protect data in transit and at rest
- NIST CSF: DE.CM-7 – Continuous monitoring for unauthorized access and activity
- NIST SP 800-53: AU-2 / AU-12 – Audit events and logging
- NIST SP 800-171: 3.1.13 – Monitor and control remote access sessions
- NIST SP 800-171: 3.13.11 – Employ FIPS-validated cryptography for data protection
- NIST SP 800-171: 3.14.1 – Identify, report, and correct system flaws in a timely manner
Common Compliance Failures
Organizations frequently fall short in National Institute of Standards and Technology compliance when it comes to web application client-side security:
- Unmonitored third-party scripts injecting unauthorized data collection.
- Shadow IT tag managers bypassing governance and capturing sensitive data.
- Failure to detect script changes that open vulnerabilities to Magecart-style attacks.
- Inadequate evidence for auditors, with no proof of real-time monitoring or response.
For example, multiple U.S. federal contractors have failed audits under DFARS/NIST 800-171 due to incomplete data flow mapping and insufficient monitoring of external integrations. Attackers often exploit these exact blind spots.
How Feroot Helps with National Institute of Standards and Technology Compliance
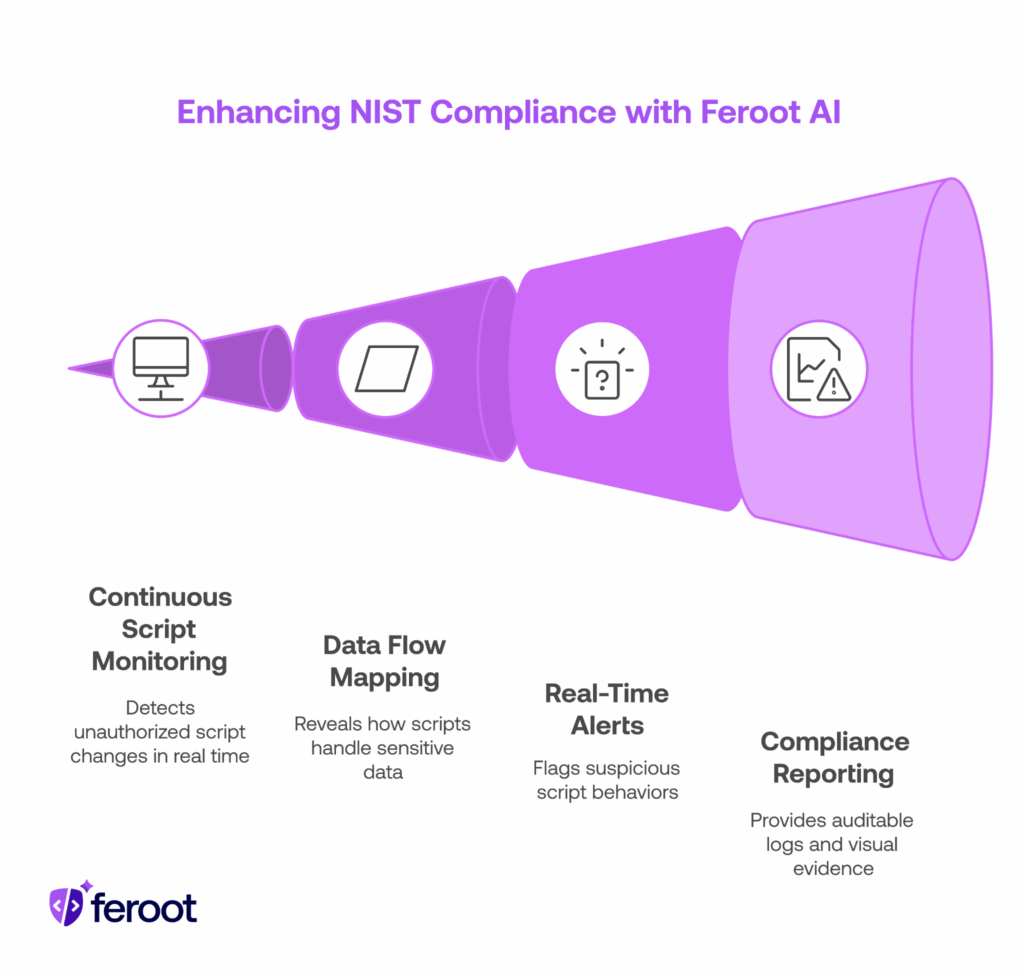
Feroot AI provides direct support for NIST requirements by securing the client-side attack surface. Here’s how:
Continuous Script Monitoring
- Detects unauthorized script injections and changes in real time.
- Supports NIST CSF DE.CM-7 (continuous monitoring) and NIST 800-171 3.14.1 (flaw remediation).
Data Flow Mapping
- Reveals how first- and third-party scripts handle sensitive data.
- Supports NIST CSF ID.AM-1 (asset management) and PR.DS-5 (data protection).
Real-Time Alerts – Rapid Incident Detection
- Flags suspicious script behaviors that could indicate an attack.
- Aligns with NIST CSF DE.CM-1 (detection processes) and RS.AN-1 (incident analysis).
Compliance Reporting & Audit Logs
- Provides auditable logs and visual evidence of client-side monitoring.
- Supports NIST SP 800-53 AU-2/AU-12 (audit events/logging) and 800-171 3.3.1 (system auditing).
By applying Feroot’s client-side security tools, organizations can demonstrate compliance while reducing the risk of breaches, fines, or lost contracts tied to NIST standards.
FAQ
What are the penalties for failing National Institute of Standards and Technology compliance?
Noncompliance can result in lost federal contracts, CMMC certification failures, reputational damage, and—if tied to breaches—legal or regulatory actions.
Does National Institute of Standards and Technology compliance apply to websites using third-party trackers?
Yes. Any uncontrolled script collecting or transmitting data may create a compliance gap under NIST CSF and 800-171 controls.
Can client-side monitoring help with NIST audits?
Absolutely. Continuous monitoring, logging, and visual reporting provide the evidence auditors expect.
How can I prove to auditors that my web apps are secure?
Feroot AI generates visual data flow maps, activity logs, and reports that can be shared directly with auditors.
What tools are available to detect unauthorized third-party data collection?
Feroot AI provides full visibility and control over client-side scripts and third-party trackers.
Conclusion
NIST standards form the backbone of modern cybersecurity and compliance frameworks. Yet too many organizations overlook the client-side risks of their websites and applications—where sensitive data is most exposed.
Feroot fills this gap with continuous script monitoring, data flow mapping, and compliance reporting designed to align directly with NIST CSF, SP 800-53, and SP 800-171.