What you’ll learn in this article
- Why PCI DSS 4.0.1 Requirements 6.4.3 and 11.6.1 extend compliance into the browser.
- How Content Security Policy (CSP) establishes a preventive baseline but stops short of full visibility.
- Where client-side monitoring adds detection, integrity validation, and audit-ready proof.
- How to align CSP and monitoring to create a sustainable, evidence-driven compliance process.
- A 30-day roadmap to move from manual reporting to continuous assurance.
Navigating PCI DSS 4.0.1 with clarity and confidence
Preparing for PCI DSS 4.0.1 can feel complex, especially when so much of compliance now lives in the browser. Your assessor’s main goal is simple: to confirm that your controls are not only in place but also working as intended. Two requirements matter most for e-commerce environments.
- Requirement 6.4.3 calls for a full inventory and authorization process for every script that runs on a payment page.
- Requirement 11.6.1 requires a tamper detection mechanism that alerts your team when a script or HTTP header changes unexpectedly.
Many organizations start with Content Security Policy (CSP). It’s a sensible place to begin because CSP gives browsers a set of rules about what content to load. However, as assessment time approaches, most teams realize CSP alone doesn’t generate the proof or visibility that a Qualified Security Assessor (QSA) expects to see. Days are often spent compiling spreadsheets, screenshots, and approvals that could have been automated with the right tools.
Compliance becomes simpler once visibility and verification move from manual tasks to continuous processes. The shift from point-in-time evidence to continuous assurance helps teams stay ready year-round.
Why these requirements exist
The PCI Security Standards Council introduced Requirements 6.4.3 and 11.6.1 in response to a simple but growing reality: attackers now target the browser itself. Research shows that a significant majority of modern web and payment breaches exploit vulnerabilities in client-side JavaScript and third-party scripts. That means the biggest risks often hide in scripts that load silently within the customer’s browser, not in the server infrastructure most teams have traditionally focused on.
These new requirements were designed to help organizations see what’s happening inside that browser environment, authorize what belongs there, and detect what does not.
What CSP solves (and doesn’t) for a PCI DSS audit
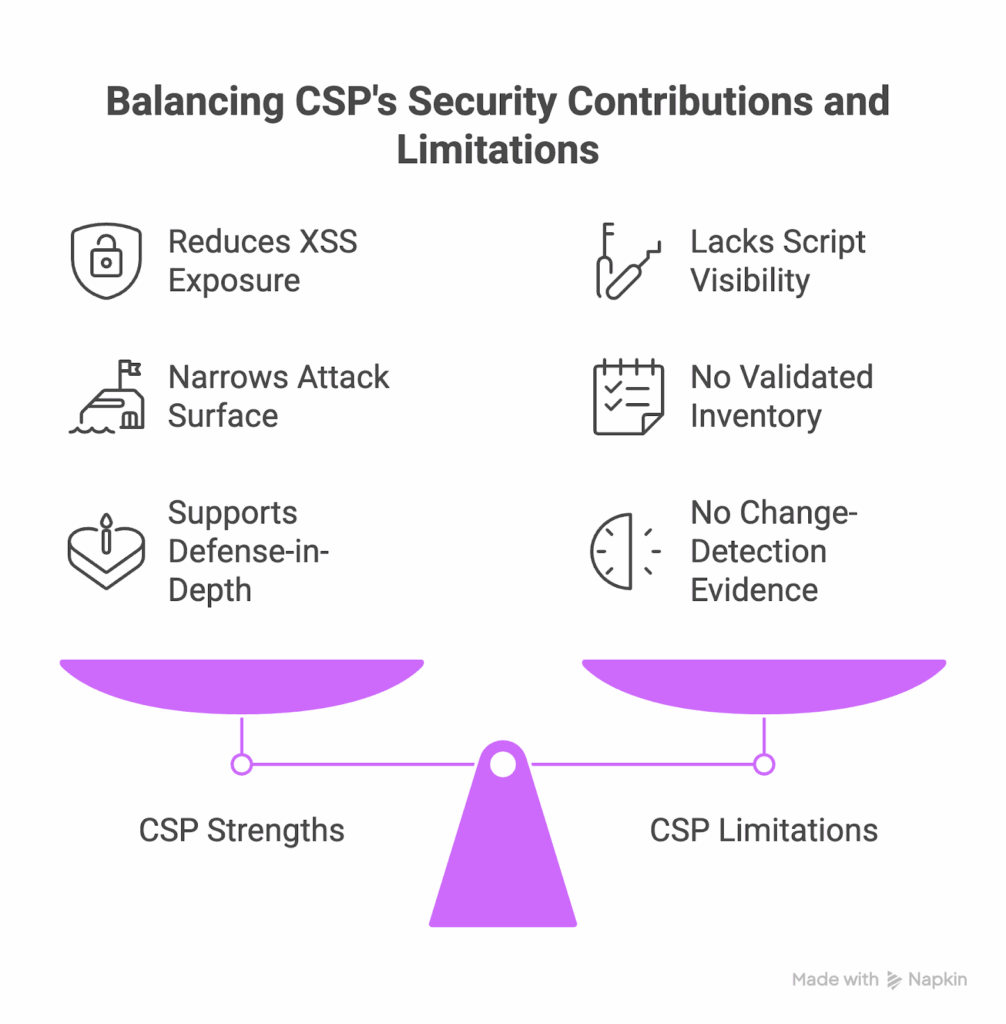
CSP is a valuable preventive layer. It helps your team narrow where the browser can load scripts from, reducing exposure to unapproved or malicious domains. Properly configured, it limits cross-site scripting and enforces a “known good” baseline.
CSP narrows where scripts may load, but it doesn’t observe what approved code does once it executes. It cannot record data access, network calls, or behavioral changes, and it doesn’t generate the validated inventory or alert evidence auditors expect under PCI DSS 4.0.1.
In fast-moving environments—tag managers, vendor updates, and frequent release cycles—allowlists drift. A trusted CDN can still deliver an unexpected update that remains within CSP’s approved boundaries.
In short, CSP prevents many issues before they start, but it doesn’t provide visibility or proof that everything is still working as it should.
QSA evidence requirements for 6.4.3 and 11.6.1
Your assessor wants to confirm that your team not only set up controls but can also prove they function correctly.
| Requirement | What your QSA expects |
| 6.4.3 | A script inventory for each page, listing source, owner, purpose, approval date, hash/signature reference, and last review timestamp, along with documentation of the authorization process. |
| 11.6.1 | Alert and log evidence showing timestamps, affected pages, new destinations, alert ID, disposition (true/benign), escalation timestamp, and triage notes, along with proof of SIEM integration and defined service levels. |
Teams that rely on manual spreadsheets and screenshots often spend weeks preparing for audits. Teams that automate their monitoring and reporting can usually produce everything in a few hours. What we’ve seen is that this shift doesn’t just save time, it builds confidence.
How CSP and client-side monitoring work together
Think of CSP as your gatekeeper and client-side monitoring as your observer. CSP sets the boundaries for what the browser can load. Monitoring watches what actually happens in real time and records it for evidence.
When both layers work together, compliance becomes easier to sustain. CSP sets boundaries for what may load; monitoring records runtime behavior, tracks changes, and alerts the team when something new appears. This visibility ensures that no change goes unnoticed and that every alert is tied to a clear action plan.
The combination allows security, engineering, and compliance teams to collaborate seamlessly. Instead of hunting for missing evidence, they can focus on maintaining a consistent, auditable state of control.
A 30-day implementation roadmap
Introducing client-side monitoring alongside CSP does not need to feel disruptive. What we’ve seen work best is a gradual approach over the course of about a month. This allows your teams to build confidence in each step before moving to the next. Let’s look at this together.
Week 1: Establish visibility
The first step is simple observation. Enable monitoring in report-only mode and review how your current CSP behaves in production. This gives your team a clear picture of which scripts are active and where they come from, without changing how your site functions. The goal in this stage is awareness. You’re learning what’s happening in your environment before making adjustments.
Week 2: Assign ownership and test alerts
Once you can see the landscape, the next step is assigning responsibility. Each script should have a defined owner, so that alerts reach the right people. During this week, teams can test detection workflows and simulate small changes to confirm that alerts and notifications behave as expected. This step helps everyone feel comfortable with the process and confident that no alert will go unnoticed.
Week 3: Move from observation to enforcement
Now that visibility and ownership are in place, it’s time to turn CSP policies from observation into enforcement. Service levels are finalized, and monitoring data is mapped directly to PCI DSS requirements 6.4.3 and 11.6.1. This gives compliance teams a clear view of how evidence will be collected and reported. The focus here is on control and consistency, not disruption.
Week 4: Automate and sustain
In the final week, automation begins. Regular reports are scheduled, monitoring is integrated into CI/CD pipelines, and quarterly reviews are planned. These routines keep the process sustainable over time. The goal is to ensure that compliance becomes part of normal operations rather than a special project that needs to be rebuilt every year.
By the end of thirty days, your team has more than just new controls. It has a process that proves your site is protected, compliant, and ready for any assessment, all without slowing business growth.
Demonstrating control effectiveness to your QSA
When assessors review your controls, they look for evidence that shows those controls working in real life. For example, imagine a vendor tag update that introduces a small change. Under CSP alone, the change might go unnoticed because the domain is already approved. With CSP and client-side monitoring, an alert appears immediately, the team investigates, confirms legitimacy, and documents the decision.
This sequence tells a clear story: the control detected, the team responded, and the record proves it. It is exactly the type of operational maturity QSAs value because it shows that your organization does not just have controls, it actively manages them.
Common QSA questions answered
Is CSP still necessary in 2025?
Yes. CSP remains a foundational control. It prevents many issues before they occur and is expected by auditors.
Can CSP alone satisfy 6.4.3 or 11.6.1?
Not entirely. CSP helps with prevention, but it doesn’t create the visibility or audit evidence that QSAs require.
Will continuous monitoring slow checkout?
No. Monitoring solutions observe passively, so performance impact is minimal. Many teams test this in a lower environment and confirm that user experience remains unaffected.
The path forward
The most sustainable approach is to keep CSP as your preventive foundation and enhance it with client-side monitoring for visibility and evidence.
We recommend following these best practices:
- Start by tightening CSP policies to remove unnecessary wildcards.
- Add monitoring to capture real-time behavior and verify control effectiveness.
- Map monitoring reports directly to PCI DSS 4.0.1 requirements 6.4.3 and 11.6.1.
- Review quarterly to stay current as your payment environment evolves.
Compliance programs perform best when control verification becomes part of daily operations rather than an annual exercise. By layering prevention with verification, your team can demonstrate control confidently, show evidence instantly, and maintain compliance with calm assurance, all while keeping business running smoothly.
See how PaymentGuard AI automates compliance, book your free demo today.