Magecart: A Definition
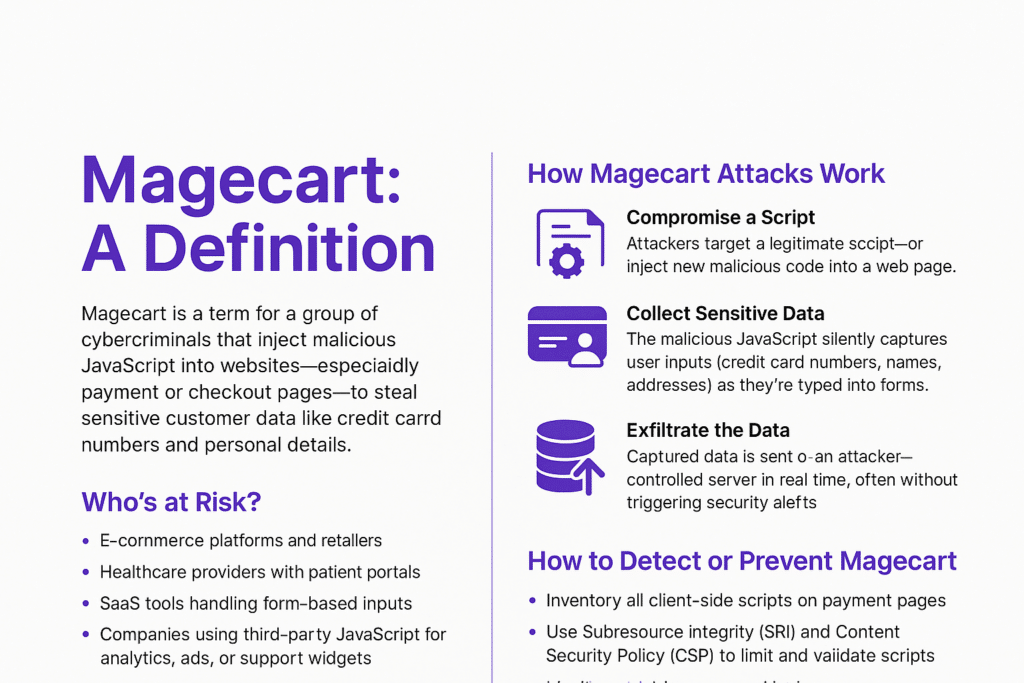
Magecart is a term for a group of cybercriminals that inject malicious JavaScript into websites—especially payment or checkout pages—to steal sensitive customer data like credit card numbers and personal details. These browser-based attacks are fast, invisible to traditional defenses, and increasingly common.
How Magecart Attacks Work
Magecart attacks typically follow this pattern:
- Compromise a Script
Attackers target a legitimate script—often from a third-party vendor—or inject new malicious code into a web page.
- Collect Sensitive Data
The malicious JavaScript silently captures user inputs (credit card numbers, names, addresses) as they’re typed into forms.
- Exfiltrate the Data
Captured data is sent to an attacker-controlled server in real time, often without triggering security alerts.
Who’s at Risk?
Any organization with a customer-facing website can be vulnerable, especially:
- E-commerce platforms and retailers
- Healthcare providers with patient portals
- SaaS tools handling form-based inputs
- Companies using third-party JavaScript for analytics, ads, or support widgets
How to Detect or Prevent Magecart
- Inventory all client-side scripts on payment pages
- Use Subresource Integrity (SRI) and Content Security Policy (CSP) to limit and validate scripts
- Monitor script behavior, not just source
- Set up real-time alerts for unauthorized changes
- Audit all third-party scripts and vendors regularly
How Feroot Helps
- Feroot helps security teams and compliance leads protect against Magecart by:
- Providing a real-time inventory of all scripts running in users’ browsers
- Scoring script behavior to flag suspicious or high-risk actions
- Offering tamper detection and change alerts
- Helping teams build and test CSP policies for safer script execution
- Generating audit-ready compliance reports
Want to see how Feroot can protect your site from Magecart?
Request a demo → feroot.com/demo
FAQ
Is Magecart a type of malware?
Not in the traditional sense. Magecart uses JavaScript embedded in web pages to steal data during checkout. It doesn’t infect devices or servers like viruses do.
Can firewalls block Magecart?
Not effectively. These attacks occur in the browser, bypassing most server-side defenses.
Why is Magecart hard to detect?
Because it uses legitimate scripts and looks like normal behavior unless you’re monitoring the browser side in real time.