TL;DR
- Formjacking is a type of e-skimming attack where malicious code is injected into web forms to steal user data like credit card numbers or login credentials.
- It matters because it enables silent data theft directly from trusted websites—often going undetected for weeks or months.
- Formjacking is the digital equivalent of credit card skimming, but for online transactions.

Introduction
Who should read this:
Security professionals, compliance teams, ecommerce site operators, and developers concerned with web supply chain risk.
Why it matters:
Formjacking attacks are increasingly targeting modern web apps and customer-facing forms, creating privacy, legal, and financial risks. High-profile breaches—from British Airways to Ticketmaster—have exposed millions of users.
What this guide covers:
- A deeper definition of formjacking
- How it works and real-world examples
- Detection and prevention strategies
- Links to compliance frameworks like PCI DSS 4.0
What is Formjacking?
Formjacking is the unauthorized injection of malicious JavaScript into a website’s form fields—often on checkout or login pages. The attacker’s goal is to intercept and exfiltrate sensitive data entered by users, such as:
- Credit card numbers
- Passwords
- Personally identifiable information (PII)
This stolen data is typically sent to a command-and-control server under the attacker’s control, often without affecting the website’s performance—making it hard to detect.
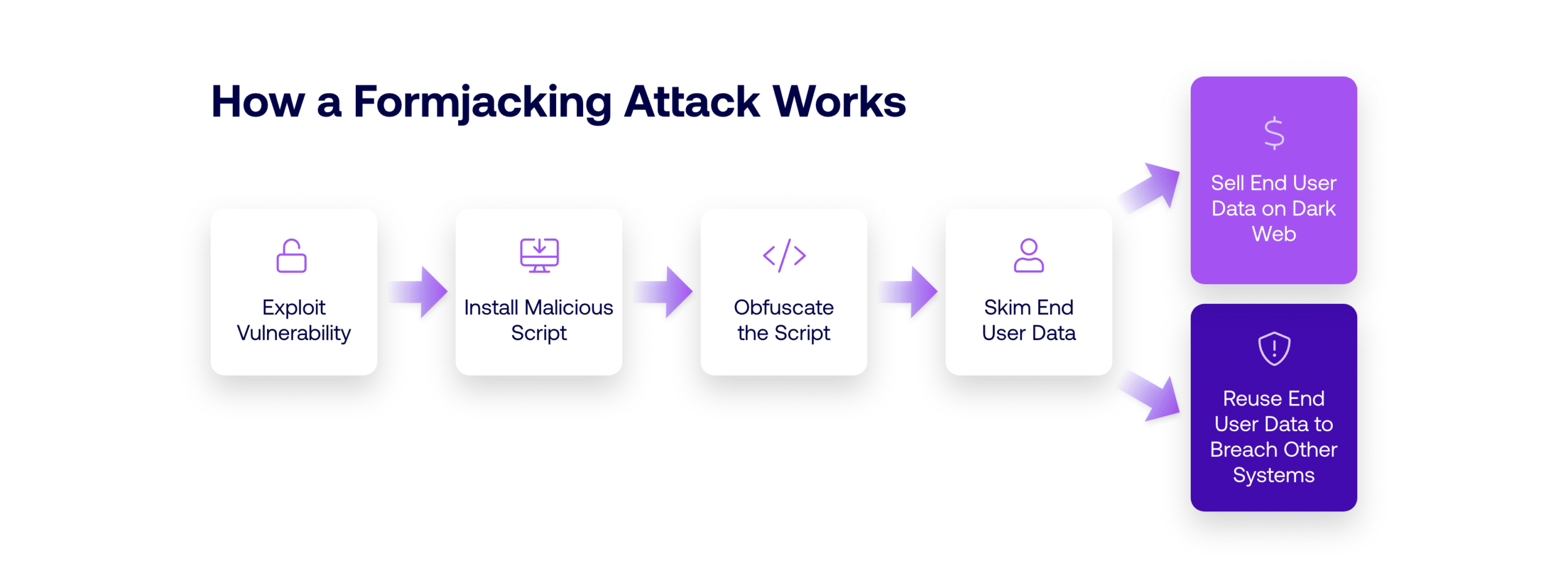
How Formjacking Attacks Work
Step-by-step breakdown:
- Compromise: Attackers gain access to a website directly or via a third-party script (e.g., chat widgets, analytics, ads).
- Injection: Malicious JavaScript is added to the form page.
- Exfiltration: When users enter information into the form, the script silently sends that data to an external server.
- Persistence: The attack often continues undetected, especially in apps using dynamic JavaScript loading.
Key entry points:
- Third-party scripts (e.g., CDNs, vendors)
- Insecure CI/CD pipelines
- Lack of runtime script monitoring
Real-World Examples
British Airways (2018)
Hackers injected malicious code into the BA payment page, stealing credit card details from over 380,000 transactions. Result: £20 million fine under GDPR.
Ticketmaster
Compromise occurred via a third-party chat plugin. This supply chain attack harvested sensitive user data without detection for several months.
Newegg
Magecart attackers inserted only 15 lines of JavaScript, resulting in weeks of customer data being siphoned from checkout pages.
The 2019 Symantec Report FORMJACKING: How Malicious JavaScript Code is Stealing User Data from Thousands of Websites Each Month reports the discovery of 1.5 million formjacking attack during the first quarter of 2019. That is approximately 500,000 formjacking attacks per month on average. The study further notes that, on average, websites compromised with formjacking stayed infected for 46 days.
How to Prevent Formjacking
Security best practices:
JavaScript Runtime Protection: Use client-side security tools to detect and block malicious scripts in real time.
- Subresource Integrity (SRI): Enforce cryptographic hashes on third-party scripts.
- Content Security Policy (CSP): Limit which domains can load scripts on your site.
- Script Behavior Monitoring: Continuously monitor script actions (especially DOM manipulation and network calls).
- PCI DSS 4.0 Compliance:
- Requirement 6.4.3: Prevent unauthorized script execution.
- Requirement 11.6.1: Detect and alert on changes to payment page scripts.
FAQ
What is the goal of formjacking?
To secretly collect sensitive user information—especially payment and identity data—from web forms and send it to malicious actors.
How is formjacking different from phishing?
Phishing tricks users into submitting data on fake sites. Formjacking targets real, trusted sites and silently steals data during normal interactions.
How do hackers inject formjacking scripts?
Commonly via compromised third-party scripts, plugin vulnerabilities, or insecure CI/CD environments.
Can formjacking affect single-page applications (SPAs)?
Yes. In fact, SPAs often rely heavily on JavaScript, making them a prime target for dynamic script injection attacks.
How long do formjacking attacks typically go unnoticed?
Weeks to months, especially when no runtime monitoring or behavioral analysis tools are in place.