TL;DR
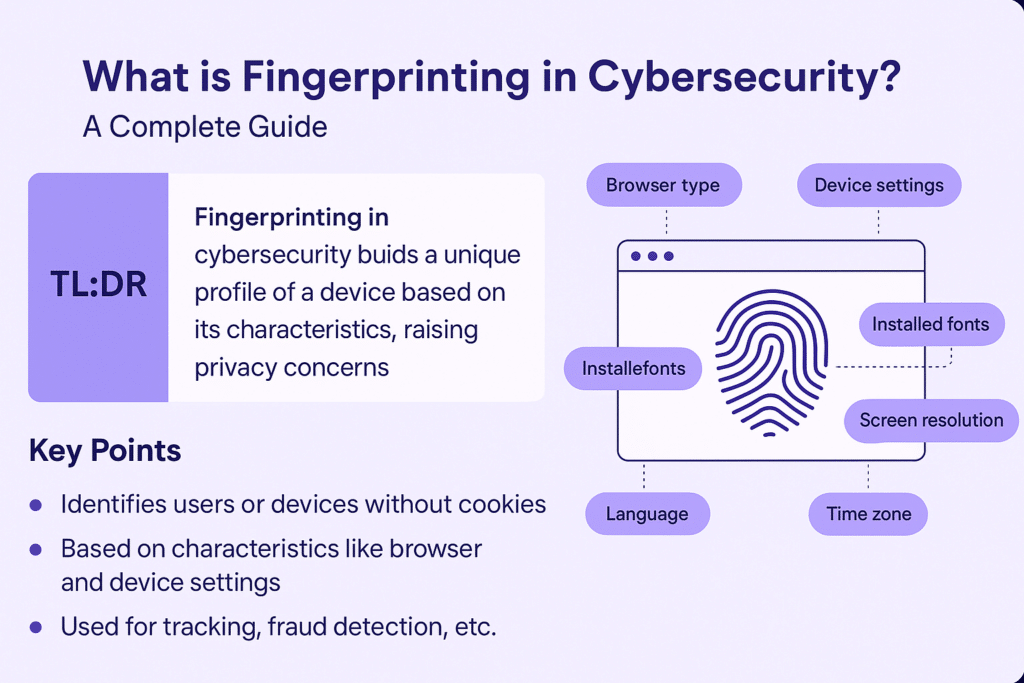
- Fingerprinting in cybersecurity refers to the method of identifying users or devices based on unique characteristics such as browser type, device settings, and behavior patterns.
- It matters because it allows both legitimate and malicious actors to track users across websites without cookies or consent.
- Browser fingerprinting builds a unique profile of your device without needing cookies, raising serious privacy concerns.
Introduction
Who this is for:
This guide is for privacy professionals, security teams, compliance officers, developers, and marketers who need to understand how fingerprinting works and how to detect or mitigate its risks.
Why it matters:
As third-party cookies phase out, browser fingerprinting has emerged as a powerful—often hidden—tracking technique. While useful for fraud prevention, it also opens the door to invasive surveillance and compliance risks under regulations like GDPR, CCPA, and PCI DSS 4.0.
What we’ll cover:
- What fingerprinting is and how it works
- Real-world use cases
- Privacy and compliance risks
- How to detect and mitigate fingerprinting
- FAQs and next steps
What Is Browser Fingerprinting?
Fingerprinting is a technique used to identify and track users based on a combination of device, browser, and behavioral characteristics. Unlike cookies, which store data on the user’s device, fingerprinting works passively—collecting data like:
- Browser version
- Operating system
- Screen resolution
- Installed fonts
- Time zone
- Language settings
- WebGL and Canvas rendering
- Device memory and CPU info
By combining these attributes, fingerprinting tools create a unique “fingerprint hash” that can persist across sessions—even if users clear cookies or browse in private mode.
Real-World Examples of Fingerprinting
Fingerprinting is used both legitimately and maliciously:
Legitimate Use Cases:
- Fraud detection: Banks and eCommerce platforms detect suspicious activity using fingerprinting.
- Account protection: Some services use it to verify trusted devices during login.
Malicious or Grey-Area Uses:
- Advertising trackers: Ad tech companies use fingerprinting to bypass cookie restrictions.
- Surveillance scripts: Threat actors or overzealous platforms may track users across websites without consent.
- Data brokers: Aggregate user fingerprints for sale or analysis without user awareness.
Notably, many third-party scripts—like tracking pixels, session replay tools, or JavaScript SDKs—can be used for fingerprinting even when users opt out of tracking.
Privacy and Compliance Risks
Fingerprinting poses several risks under data protection laws:
- Lack of consent: Most fingerprinting occurs without explicit user consent, violating regulations like GDPR and CCPA.
- Invisibility: Fingerprinting doesn’t show up in browser storage or cookie audits, making it hard to detect.
- Cross-site tracking: Users can be tracked across unrelated websites using the same fingerprint.
- PCI DSS 4.0 compliance: Requirement 11.6.1 emphasizes protection from unauthorized script behavior, including fingerprinting attempts.
Organizations unaware of hidden fingerprinting scripts may be exposed to regulatory fines or data leaks.
How to Detect and Prevent Fingerprinting
Detection:
- Use script behavior analysis tools to identify hidden fingerprinting activities.
- Monitor for known fingerprinting libraries (e.g., FingerprintJS).
- Run dynamic audits of client-side code execution.
Prevention:
- Content Security Policy (CSP): Restrict script sources to trusted domains.
- Subresource Integrity (SRI): Verify third-party scripts haven’t been tampered with.
- Script monitoring solutions like Feroot can alert you to fingerprinting behavior.
- Limit reliance on third-party libraries unless essential and vetted.
Make sure you follow secure development practices outlined by Google Web Fundamentals.
FAQ
What’s the difference between fingerprinting and cookies?
Cookies store data on the user’s device; fingerprinting collects information about the device to create a unique ID without storing anything locally.
Is browser fingerprinting legal?
It depends on jurisdiction and intent. Without user consent, fingerprinting may violate laws like GDPR, CCPA, and ePrivacy Directive.
Can users prevent fingerprinting?
Partially. Tools like Firefox’s Enhanced Tracking Protection and browser extensions can reduce fingerprintable data, but complete prevention is difficult.
Which companies use fingerprinting?
Ad networks, analytics firms, fraud detection platforms, and even some customer support tools may employ fingerprinting.
How does fingerprinting relate to PCI DSS?
Fingerprinting scripts, especially those injected via third parties, may violate PCI DSS 4.0 if they introduce unauthorized or unmonitored behavior in payment pages.


