TL;DR
- Tracking pixels can unintentionally leak PHI and violate HIPAA
- Most healthcare websites lack visibility into what third-party scripts are doing
- Auditing, consent management, and client-side protection are essential
- Feroot’s HealthData Shield AI helps detect and block risky pixels before they cause a data leak
Introduction
Web tracking pixels — also known as pixel tags or web beacons — are tiny, often invisible snippets of code embedded in websites, emails, and apps.
In healthcare, they’re used for:
- Analytics: Measuring traffic and user engagement
- Personalization: Customizing content and recommendations
- Patient portals: Monitoring interactions with appointment booking or health record systems
- Marketing insights: Evaluating ad performance and campaign ROI
While these uses can support patient engagement and service optimization, they also introduce significant privacy risks — especially if they cause a data leak of Protected Health Information (PHI).
What Are the Risks of Data Leaks from Tracking Pixels?
When misconfigured or unmonitored, tracking pixels can lead to unintended sharing of sensitive data. These risks include:
- Data leaks of PHI such as IP addresses, appointment info, or medical record identifiers
- Non-compliance with HIPAA, triggering investigations, penalties, or class-action lawsuits
- Security gaps that expose systems to malicious scripts, cross-site tracking, or third-party data harvesting
Healthcare remains the most breached industry, with the average cost of a data leak reaching nearly $11 million per incident.
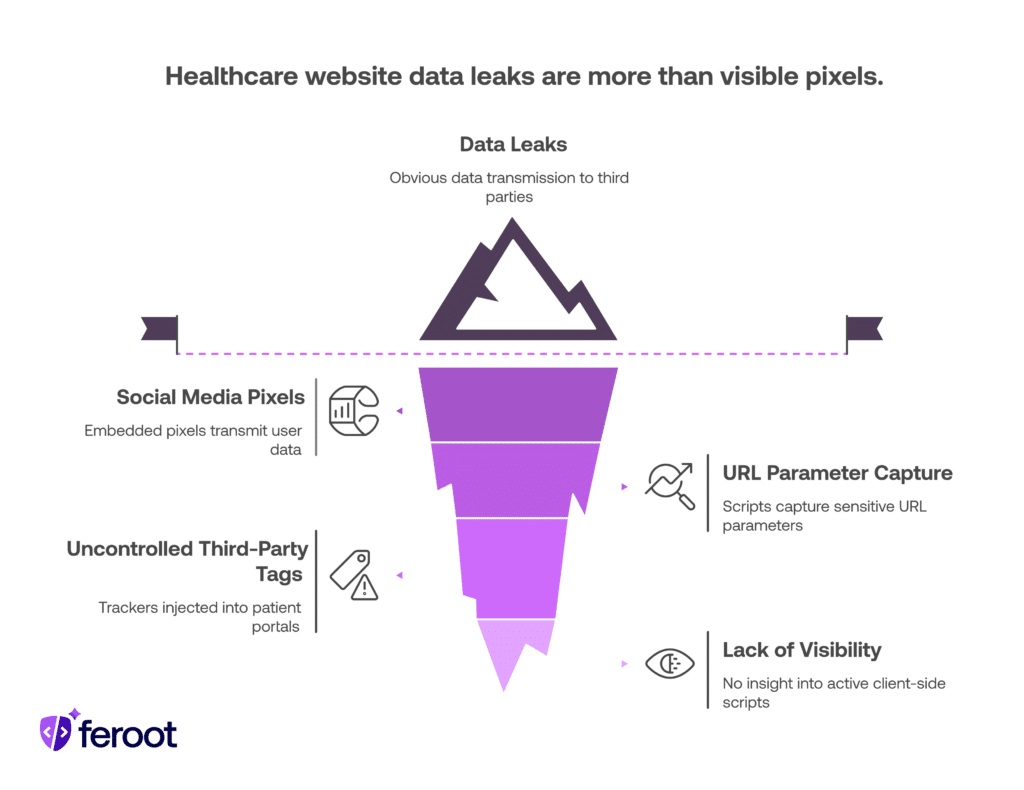
How Do Data Leaks Happen on Healthcare Websites?
Common ways data leakage occurs from tracking pixels include:
- Embedded pixels from social media platforms (e.g., Meta Pixel) transmitting user data without patient consent
- Scripts that auto-capture URL parameters, such as user ID or appointment confirmation codes
- Uncontrolled third-party tags that inject trackers into patient portals or health-related content
- Lack of visibility into what scripts are active on the client side of the web app
How Can Healthcare Organizations Prevent Data Leakage?
1. Audit Your Tracking Technologies
Start by gaining visibility into what’s currently deployed.
- Inventory all tracking pixels and third-party JavaScript on your website
- Map what data each pixel collects and where it sends it
- Identify any scripts loading without consent or proper configuration
2. Tighten Consent and Governance Controls
Avoid compliance gaps by aligning pixel usage with privacy requirements.
- Use consent management tools to record patient opt-in/out preferences
- Restrict tracking on pages that display or transmit PHI
- Document policies for pixel deployment and third-party integrations
- Train marketing, web, and DevOps teams on data leak risks
3. Control Client-Side Scripts
Tracking pixels run in the browser — a layer often ignored by traditional security tools.
- Use tools that give real-time visibility into client-side behaviors
- Block unauthorized scripts and enforce least-privilege policies
- Alert on attempts to exfiltrate sensitive data from forms or session cookies
4. Monitor and Maintain Compliance Continuously
Preventing data leaks isn’t a one-time effort.
- Set up automated scans to detect new or modified scripts
- Regularly test user journeys for unauthorized tracking
- Include client-side risks in HIPAA security risk assessments
What Should Security and Compliance Leaders Do Next?
If you’re responsible for healthcare data privacy, here are key takeaways:
- Assume risk is already present: Many tracking pixels are deployed by third parties or legacy systems
- Prioritize visibility: You can’t prevent a data leak if you don’t know what’s running on your site
- Collaborate across teams: Marketing, IT, legal, and security all need to align
- Automate what you can: Manual audits miss fast-moving client-side changes
What Role Does Feroot Play in Preventing Data Leakage?
Feroot gives CISOs and compliance teams real-time visibility and protection for client-side scripts — where most web-based data leaks begin.
Feroot’s HealthData Shield AI helps healthcare organizations:
- Detect tracking pixels that collect PHI
- Map data flows against HIPAA and security frameworks
- Enforce JavaScript security policies in real-time
- Generate audit-ready reports showing what’s blocked and why
FAQ
What is a data leak in the context of healthcare websites?
A data leak occurs when patient information is unintentionally shared or exposed — often through browser-based tracking pixels or third-party scripts.
Are tracking pixels HIPAA-compliant?
Only if properly configured. If they capture or transmit PHI without valid patient consent, they violate HIPAA.
Can we use tracking pixels for marketing without violating HIPAA?
Yes, but you must avoid collecting PHI, use proper consent flows, and limit pixels to non-sensitive pages.
Do traditional web security tools detect tracking pixel risks?
Not always. Most focus on server-side threats and ignore client-side scripts that cause data leaks.
How does Feroot’s HealthData Shield AI help?
Feroot’s HealthData Shield AI provides browser-side monitoring and enforcement that detects risky trackers, maps them to compliance frameworks, and prevents data exfiltration in real time.


