Protecting your e-commerce platform from unauthorized changes and skimming attacks is paramount for maintaining trust and ensuring compliance with PCI DSS 4.0, specifically requirement 11.6. This guide will walk you through utilizing Feroot platform to set up effective monitoring and response mechanisms for your payment pages.
Setting Up Change and Tamper-Detection with Feroot Inspector
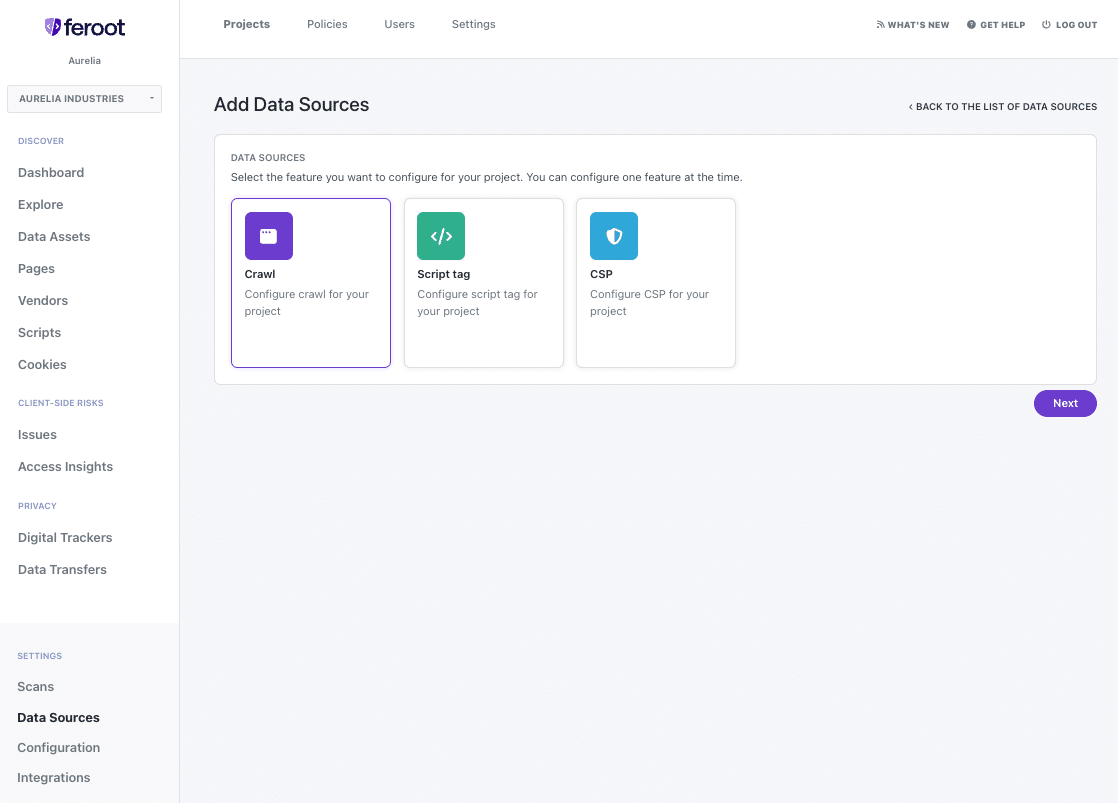
Step 1: Configure Feroot Inspector Crawler
- Objective: Regularly check for unauthorized modifications of payment pages.
- How to Configure:
- Access your Feroot platform and navigate to the Data Sources option.
- Click on Inspector Crawl source type and click on Next
- Schedule the Crawler to perform scans of your payment pages at least weekly or according to the frequency determined by your entity’s targeted risk analysis, adhering to Requirement 12.3.1.
Step 2: Activate Alerts for Unauthorized Changes
- Objective: Ensure prompt notification of any unauthorized script/code changes on payment pages.
- How to Activate:
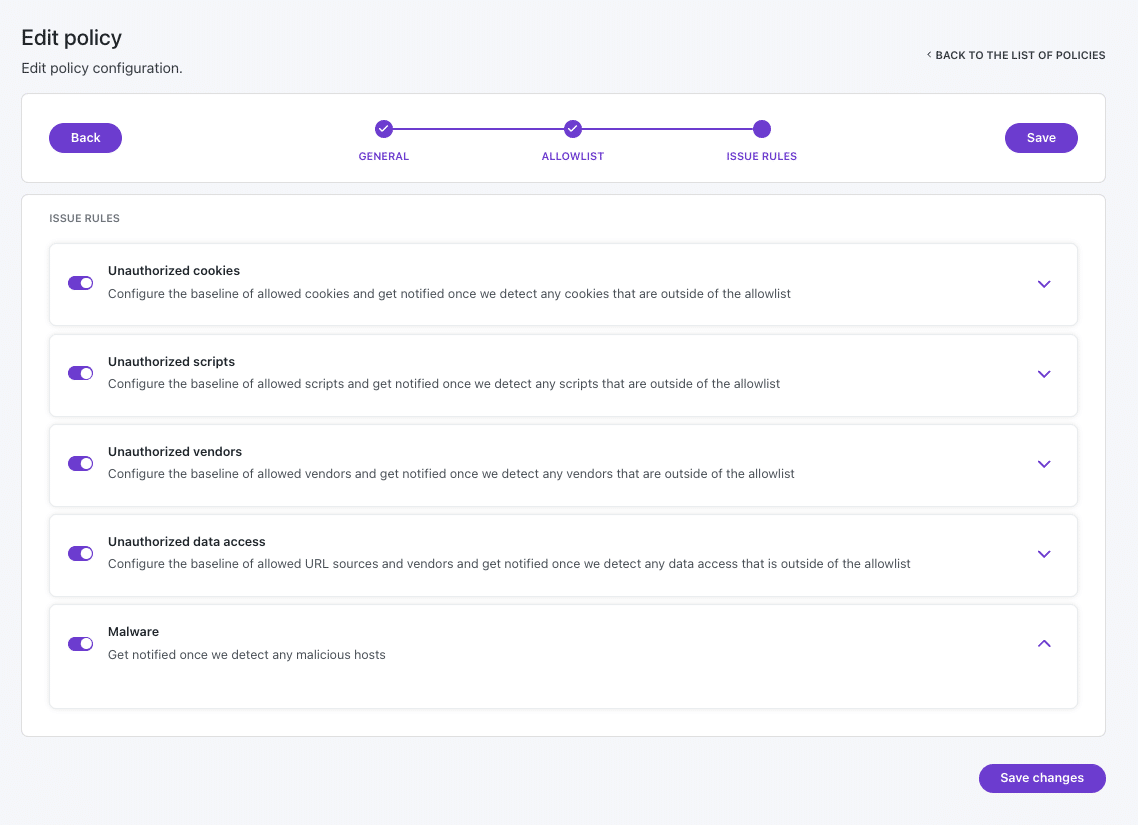
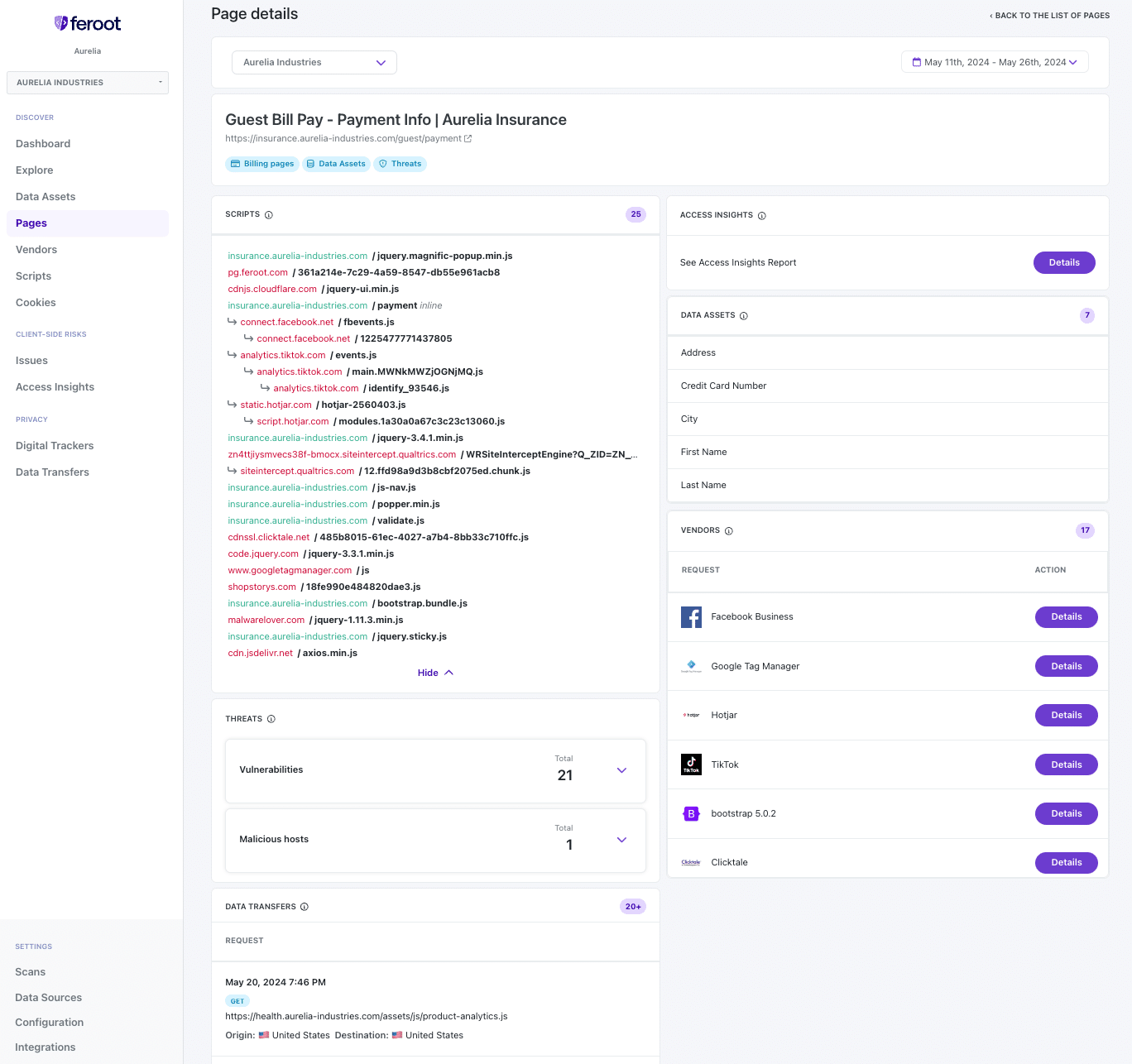
- Use Feroot Inspector’s Access Insight Report and Page Details Scripts report to maintain an inventory of authorized code.
- Configure alerts within Feroot Inspector to notify relevant personnel should unauthorized scripts/code be detected.
Implementing Customized Approach for Anti-Skimming with Feroot PageGuard
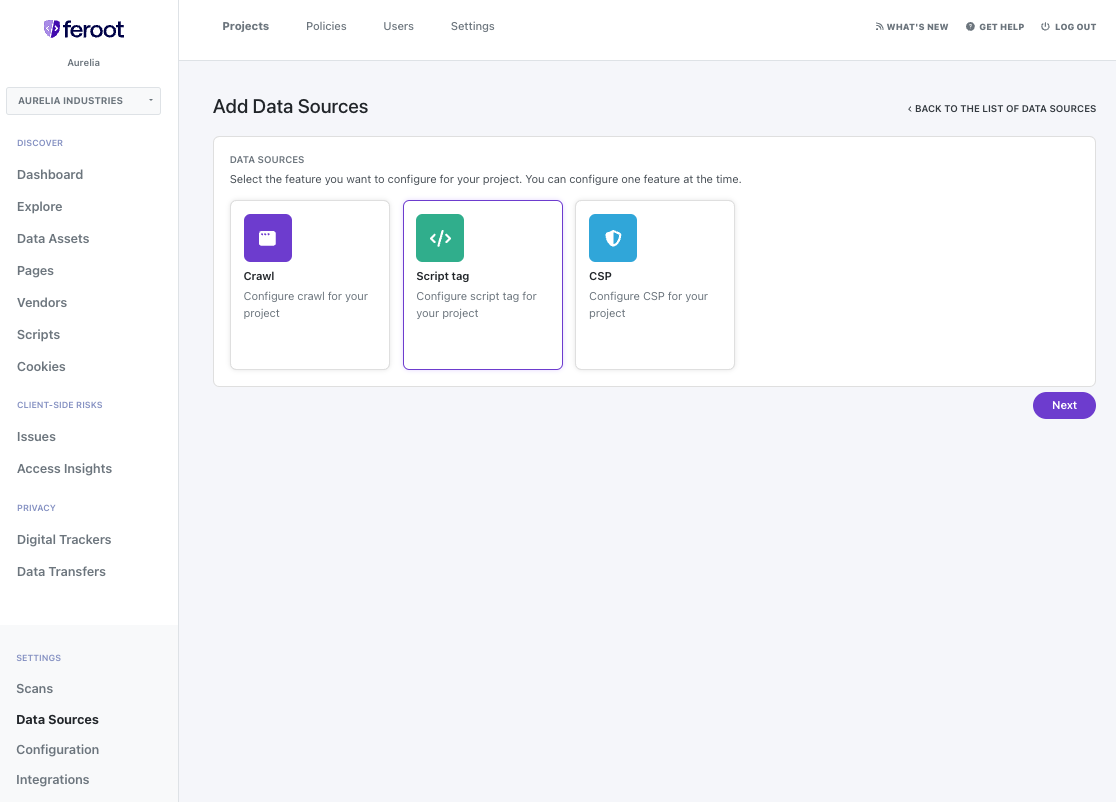
Step 1: Activate Security Policy and Tag Controls
- Objective: Prevent unauthorized content/scripts/code from being loaded onto the payment pages and remove unneeded scripts.
- How to Activate:
- Utilize Feroot PageGuard to enforce Security Policy and Tag Controls.
- Ensure that only necessary content, scripts, and code are permitted on the payment page.
Step 2: Monitoring and Response
- Objective: Timely alert generation for added e-commerce skimming code or techniques and immediate notification if anti-skimming measures are removed.
- How to Monitor and Respond:
- Regularly review Feroot PageGuard and Inspector reports for any alerts or indications of unauthorized changes or skimming attempts.
- Set up incident response protocols to quickly address any detected issues.
Regular Compliance Checks
Periodic Examination of System Settings and Monitoring Results
- Objective: Verify the effectiveness of change and tamper-detection mechanisms.
- How to Perform Checks:
- Periodically review system settings, monitored payment pages, and results from monitoring activities.
- Ensure that the change and tamper-detection mechanism is configured and functioning as intended.
Review of Configuration Settings
- Objective: Confirm that detection mechanisms are properly set up in line with PCI DSS requirements.
- How to Review:
- Examine configuration settings to verify that all elements specified in requirement 11.6 are addressed.
- Interview responsible personnel to ensure mechanisms function at the defined frequency.
Best Practices for Ensuring Payment Page Security
- Understand Your Content: Be aware of all external and internal scripts running on your payment pages. Regularly audit and justify their necessity.
- Stay Informed: Keep up-to-date with the latest security threats and ensure your monitoring tools are configured to detect these new threats.
- Educate Your Team: Ensure that all team members involved in website maintenance and security are aware of the importance of PCI DSS compliance and know how to respond to alerts.
By following this guide and utilizing Feroot’s Inspector and PageGuard tools, you can establish a robust defense against unauthorized changes and skimming attacks on your payment pages, ensuring compliance with PCI DSS 4.0 requirement 11.6.


