TL;DR
PCI DSS 11.6.1 (4.0) requires merchants and TPSPs to deploy change- and tamper-detection mechanisms that monitor and alert on unauthorized modifications to payment page scripts and HTTP headers, as seen in the customer’s browser. Monitoring must occur weekly or per a risk-based schedule. Tools like CSP, script behavior monitors, and alerting systems help ensure compliance and prevent e-skimming threats like Magecart.
Introduction
As e-commerce continues to grow, securing payment pages against threats like e-skimming and Magecart attacks is critical. The PCI DSS 4.0 compliance for websites introduces Requirement 11.6.1, which focuses on deploying a change- and tamper-detection mechanism to protect payment pages. This blog explores the testing procedures and assessment evidence needed to meet this requirement, helping merchants and third-party service providers (TPSPs) implement payment page security solutions and achieve secure payment processing compliance.
Understanding PCI DSS Requirement 11.6.1
PCI DSS Requirement 11.6.1 mandates a mechanism to:
- Alert personnel to unauthorized modifications in security-impacting HTTP headers and script contents of payment pages as rendered in a consumer’s browser.
- Evaluate received HTTP headers and payment pages.
- Perform these functions at least weekly or at a frequency defined by the entity’s targeted risk analysis (TRA) per PCI DSS Requirement 12.3.1.
This requirement is vital for e-skimming prevention for e-commerce, addressing risks like malicious script detection and ensuring HTTP header integrity monitoring. It applies to merchants and TPSPs managing payment pages, whether through merchant-hosted forms, embedded iframes, or redirection mechanisms.
Testing Procedures for Requirement 11.6.1
To confirm compliance with PCI DSS 11.6.1 compliance software, entities must follow specific testing procedures outlined in the PCI DSS v4.0 framework. These procedures ensure the mechanism is effective in detecting unauthorized change detection for web apps. Below are the key testing procedures and their purposes:
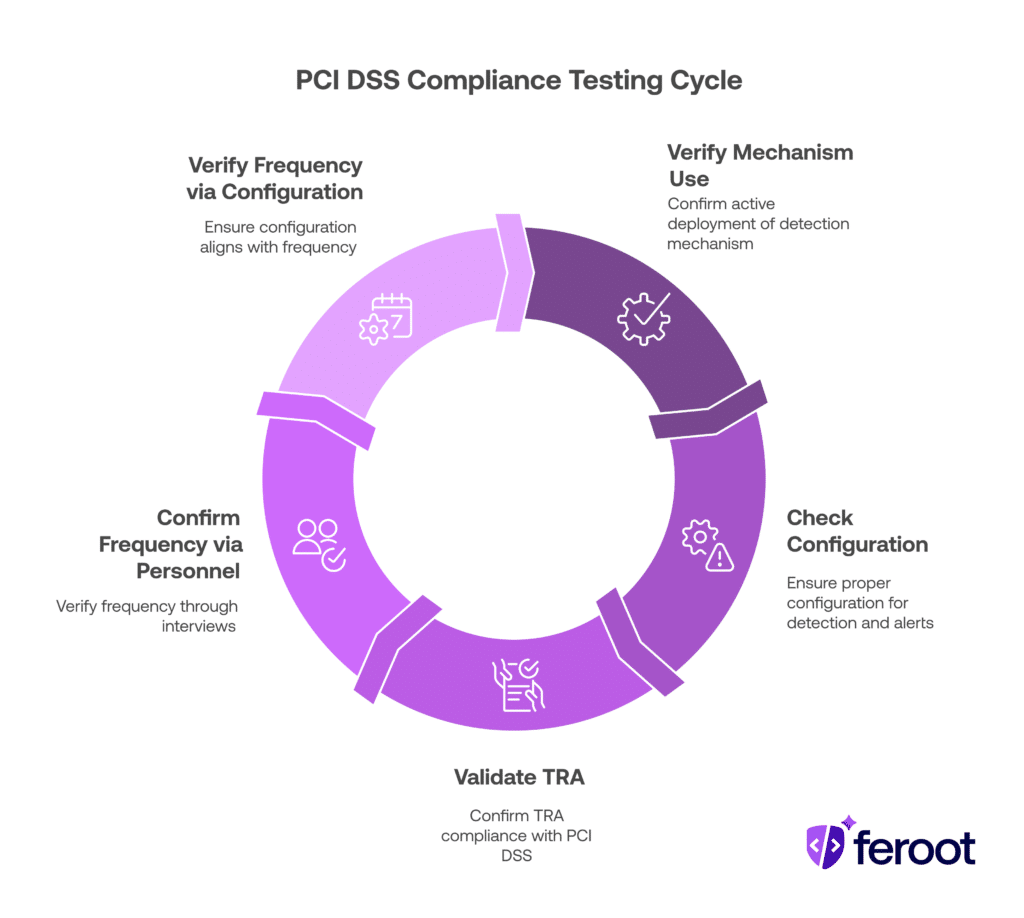
- 11.6.1.a: Verify the Mechanism is in Use
- Purpose: Confirm that a change- and tamper-detection mechanism is actively deployed.
- Expected Evidence: Documentation or system configurations showing system settings, monitored payment pages, and results from monitoring activities (e.g., logs, reports).
- 11.6.1.b: Check Configuration
- Purpose: Ensure the mechanism is configured to detect and alert on unauthorized modifications to HTTP headers and script contents while evaluating received headers and pages.
- Expected Evidence: System configuration settings demonstrating detection and alerting capabilities.
- 11.6.1.c: Validate TRA (if applicable)
- Purpose: If the entity uses a TRA to define a frequency other than weekly, confirm the TRA complies with PCI DSS Requirement 12.3.1.
- Expected Evidence: The documented TRA.
- 11.6.1.d: Confirm Frequency via Personnel
- Purpose: Verify through interviews that the mechanism’s functions are performed at least weekly or at the TRA-defined frequency.
- Expected Evidence: Interviews with personnel confirming the frequency of operations.
- 11.6.1.e: Verify Frequency via Configuration
- Purpose: Ensure system configurations align with the required frequency (weekly or TRA-defined).
- Expected Evidence: Configuration settings showing the mechanism’s operational schedule.
These procedures align with website payment page integrity monitoring tools and client-side protection platform PCI DSS 4.0, ensuring robust defenses against threats like Magecart attack prevention software PCI DSS 4.0.
Assessment Evidence for Requirement 11.6.1
Entities must provide specific evidence during a PCI DSS assessment to demonstrate compliance with PCI DSS 4.0 11.6.1 detection tools. This evidence supports the testing procedures and includes:
- System Configurations and Documentation: Show settings for the change- and tamper-detection mechanism, including monitored pages and monitoring results (e.g., logs, reports). This is critical for script monitoring for payment pages.
- Configuration Settings: Demonstrate that the mechanism detects unauthorized changes to HTTP headers and scripts and evaluates received headers and pages.
- Targeted Risk Analysis (TRA): If a non-weekly frequency is used, provide a documented TRA compliant with PCI DSS Requirement 12.3.1.
- Personnel Interviews: Confirm that personnel are aware of and adhere to the mechanism’s operational frequency.
- Alerting Methods: Evidence of alerting mechanisms (e.g., email, SMS, SYSLOG events) to notify personnel of unauthorized changes, supporting malicious script detection tools.
Entities can leverage the script inventory from PCI DSS Requirement 6.4.3 to configure the tamper-detection mechanism, ensuring synergy between PCI DSS 4.0 6.4.3 software solutions and PCI DSS 11.6.1 compliance software.
Tools and Techniques for Compliance
To meet Requirement 11.6.1, entities can use best PCI DSS 4 compliance tools for e-commerce, including:
- Content Security Policy (CSP): Limits script sources and detects unauthorized scripts, supporting script monitoring for payment pages.
- Webpage Monitoring: Agent-based or agentless solutions to observe script behavior and detect anomalies, ideal for top e-skimming prevention tools.
- Proxy-based Solutions: Intercept traffic to enforce policies and block unauthorized content, enhancing HTTP header integrity monitoring.
- File Hashing and Behavior Monitoring: Techniques to verify script integrity and detect suspicious activities, aligning with PCI DSS 11.6.1 detection tools.
These top software for securing payment pages can be internally developed, commercial, open-source, or hybrid, depending on the entity’s resources. For example, leading software for PCI DSS 4.0 requirements 6.4.3 and 11.6.1 often combines CSP with real-time monitoring for comprehensive protection.
Incident Response Integration
PCI DSS Requirement 12.10.5 requires that the incident response plan includes monitoring and responding to alerts from the change- and tamper-detection mechanism. Expected evidence includes:
- A documented incident response plan detailing alert monitoring and response processes.
- Opportunities to observe incident response processes or table-top exercises.
This integration ensures timely responses to potential unauthorized change detection for web apps, minimizing the risk of data breaches.
Best Practices for Merchants
- Small Merchants: Work with TPSPs offering embedded payment forms to confirm protection against script attacks, leveraging PCI DSS 11.6.1 detection tools.
- Medium and Large Merchants: Implement advanced website payment page integrity monitoring tools to evaluate and control scripts, reducing exposure to Magecart attack prevention software PCI DSS 4.0.

Conclusion
Meeting PCI DSS Requirement 11.6.1 is essential for PCI DSS 4.0 compliance for websites and protecting e-commerce platforms from e-skimming threats. By following the outlined testing procedures and providing robust assessment evidence, entities can ensure compliance with secure payment processing compliance. Leveraging top e-skimming prevention tools and client-side protection platform PCI DSS 4.0 empowers merchants and TPSPs to safeguard payment pages, maintain customer trust, and mitigate risks effectively.
For more resources, visit the PCI Security Standards Council Document Library for guidance on best PCI DSS 4 compliance tools for e-commerce and payment page security solutions.
FAQ
Do I need to monitor payment pages hosted by a third-party gateway?
If the payment page is fully redirected and not under your control, PCI DSS 11.6.1 may not apply. But embedded forms or iframes do require compliance.
What kind of changes should be detected?
A: Unauthorized modifications to client-side scripts or HTTP headers that could introduce security risks or data exfiltration.
Can Content Security Policy (CSP) alone meet PCI DSS 11.6.1?
No. CSP helps limit sources, but you also need mechanisms that detect and alert on tampering in real time or near real time.
What qualifies as an “alert”?
Email, SMS, Syslog events, or dashboard notifications that notify personnel of detected changes in payment page content.
What’s the difference between PCI DSS 6.4.3 and PCI DSS 11.6.1?
6.4.3 requires script inventory and justification. 11.6.1 adds the need to detect unauthorized changes to those scripts.
How do I prove compliance during an audit?
Provide configuration logs, alert reports, documented TRA (if applicable), and interview evidence confirming monitoring frequency.
I already scan my site with a WAF or SAST tool. Is that enough?
No. PCI DSS 11.6.1 focuses on runtime tamper detection from the user’s browser perspective, not just server- or code-level scanning.
Can open-source tools help with compliance?
Yes, if they support script monitoring, alerting, and can demonstrate logging and coverage of your payment page environment.