Cyberattacks on healthcare providers are becoming alarmingly routine — and far more costly. In 2025, Weiser Memorial Hospital joined a growing list of medical institutions grappling with data breaches, compromising the personal and protected health information (PHI) of over 34,000 patients.
This breach, along with recent incidents at Minnesota Orthodontics, Ascension Healthcare, and others, underscores a dangerous reality: healthcare organizations remain ill-equipped to monitor and secure their client-side environments, where sensitive patient data is often exposed.
What Happened at Weiser Memorial Hospital?
On September 4, 2024, Weiser Memorial Hospital in Idaho identified suspicious network activity and took immediate steps to secure its systems. Following a forensic investigation, it was confirmed that an unauthorized third party had accessed and exfiltrated sensitive patient data — affecting 34,249 individuals, including 14 residents of Maine.
The compromised data included:
- Full names
- Dates of birth
- Social Security numbers
- Medicare/Medicaid identifiers
- Insurance policy details
- Diagnoses, procedures, and treatment information
- Government-issued ID numbers
While the intrusion was detected in 2024, the hospital did not complete its file review until April 2025 — a common delay in the healthcare sector, where breach detection and reporting can take months due to complex systems and siloed data.
Weiser Memorial offered affected patients complimentary credit monitoring services. But like most breached entities, the organization is now reacting — rather than preventing — a catastrophic event that could have been avoided with better client-side visibility.
Other 2025 Healthcare Breaches That Set the Tone
While Weiser Memorial’s incident is among the largest this year, it follows a worrying pattern seen across U.S. healthcare:
Minnesota Orthodontics and Dentofacial Orthopedics
In February 2025, MN Ortho discovered that attackers had accessed and copied sensitive patient data including health forms, insurance information, financial details, and employment records. A placeholder notification to the HHS Office for Civil Rights listed 501 affected individuals, though the final number is expected to rise significantly.
Ascension Healthcare (May 2025)
A ransomware attack at Ascension Healthcare — one of the nation’s largest nonprofit systems — disrupted operations across 140 hospitals and 2,600 sites of care. EHR systems, diagnostic tools, and patient portals were temporarily shut down, jeopardizing critical care delivery.
Aspen Dental
Also this year, Aspen Dental disclosed a breach affecting nearly 1.5 million patients, exposing a combination of PII and PHI through compromised front-end applications and unauthorized code execution.
The Common Denominator: Client-Side Risk
While the scale and methods differ, these breaches have one thing in common: they involve vulnerabilities in front-end web systems, such as patient portals, intake forms, insurance integrations, and appointment schedulers.
These client-side components often rely on:
- JavaScript libraries from third-party vendors
- Inline scripts for tracking, validation, or form behavior
- External APIs for insurance verification or telehealth sessions
- Browser-based storage for autofill or user preferences
Unfortunately, these tools create a blind spot in traditional security programs — because they run directly in the user’s browser, outside the reach of endpoint protection, firewalls, and server-side monitoring.
How Browser-Based Attacks Steal PHI
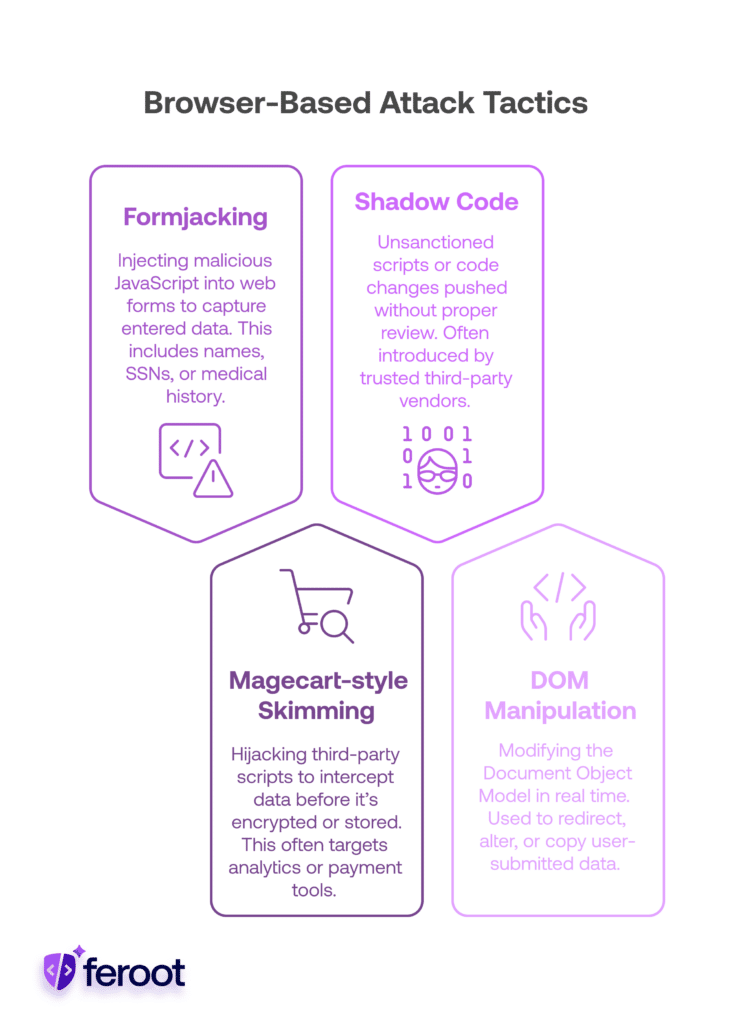
Attackers increasingly target the client side using tactics like:
Formjacking
Injecting malicious JavaScript into web forms to capture entered data like names, SSNs, or medical history.
Magecart-style Skimming
Hijacking third-party scripts (e.g., analytics, payment tools) to intercept data before it’s encrypted or stored.
Shadow Code
Unsanctioned scripts or code changes pushed without proper review or audit, often by trusted third-party vendors.
DOM Manipulation
Modifying the Document Object Model (DOM) in real time to redirect, alter, or copy user-submitted data.
In the case of Weiser Memorial, while the specific attack vector hasn’t been disclosed, the timeline and data types suggest a prolonged compromise, potentially via web application injection or insecure third-party access — both of which are commonly exploited through client-side vulnerabilities.
Why Compliance Isn’t Enough
Healthcare providers are required to meet strict standards under:
- HIPAA (Health Insurance Portability and Accountability Act)
- HITECH (Health Information Technology for Economic and Clinical Health Act)
- OCR Breach Notification Rule
Yet, many remain unprotected on the front end because these regulations focus more on data access and storage than live execution environments. Traditional HIPAA audits often miss:
- Active script behavior on patient portals
- Script-to-script communication risks
- Inline form security flaws
- Runtime changes made by tag managers or A/B testing tools
In other words, compliance checks do not equal real-time protection.
How Feroot Security Prevents Healthcare Data Breaches
At Feroot, we focus on protecting healthcare organizations where they are most vulnerable: in the patient’s browser.
HealthData Shield AI: PHI Protection at Runtime
Our HealthData Shield AI solution provides intelligent, automated defense against client-side attacks. It continuously scans and analyzes scripts, page elements, and runtime behavior to prevent unauthorized access or data theft.
Key features include:
- Script inventory and tracking: Identify every script running across patient-facing apps
- Behavioral monitoring: Detect suspicious form activity or data exfiltration in real time
- Risk scoring: Prioritize vulnerabilities based on PHI exposure
- Access control: Limit which scripts can interact with sensitive data
- Anomaly detection: Catch deviations from baseline behavior — including zero-day threats
Full Visibility Across Your Web Ecosystem
Feroot gives your security team a real-time dashboard showing exactly:
- What scripts are active
- Who deployed them
- Where they’re communicating
- Whether they touch PHI or financial information
This visibility empowers IT and compliance teams to detect and stop threats before data leaves the page.
Seamless Integration with Existing Infrastructure
HealthData Shield AI works across:
- Telehealth platforms
- EHR and practice management systems
- Insurance portals
- Custom health apps
- Public websites and intake forms
It integrates easily with your current security stack, supporting SOC/SIEM tools, incident response workflows, and audit readiness.
Final Thoughts: Breaches Like Weiser Are Preventable
The healthcare breaches of 2025 are not just cautionary tales — they’re warnings of a new threat surface many providers still ignore.
Weiser Memorial, MN Ortho, and Ascension all followed basic cybersecurity practices. They likely had firewalls, encryption, access controls. But they didn’t have visibility into the browser-side environment, where attackers increasingly operate.
If you can’t see what’s running in your patients’ browsers, you can’t secure it.
Take the first step toward proactive PHI protection — schedule your demo with Feroot Security today.