TL;DR
- Payment pages are now in scope for stricter PCI DSS 4.0 client-side controls, especially under Requirements 6.4.3 and 11.6.1.
- Inline forms, third-party scripts, and marketing tags are all risk factors — and audit triggers.
- SAQ A eligibility is harder to claim without proving control over client-side behavior.
- Feroot PaymentGuard AI monitors, detects, and enforces client-side security policies, helping teams comply without manual reviews.
- Built for CISOs, PaymentGuard AI generates audit-ready reports and reduces the risk of missed browser-based threats.
Why Are Payment Pages Now a PCI DSS 4.0 Compliance Hotspot?
Because PCI DSS 4.0 shifts focus to client-side risk, payment pages — especially those using JavaScript, third-party scripts, or marketing tags — are under increased scrutiny.
Even if your backend is secure, what happens in the browser can expose cardholder data or create audit failure risk.
Key risks:
- Inline payment forms embedded in your app
- Third-party scripts that can inject malicious code
- Inadequate control over script origin and behavior
- Shadow code or forgotten marketing tools
Legacy assessments ignored this. PCI DSS 4.0 does not.
What Payment Page Scenarios Create Risk Under PCI DSS 4.0?
1. Inline Hosted Forms
If the payment form is part of your domain (e.g., embedded via JavaScript), you’re responsible for all scripts on the page, including any third-party ones.
2. Redirect or iFrame Solutions
While these used to offer full SAQ A eligibility, that’s no longer guaranteed unless you can prove scripts can’t tamper with the iframe or redirect.
3. Third-Party Scripts and Tags
Tracking pixels, A/B testing tools, and personalization scripts often have access to the DOM, increasing your compliance scope — and your attack surface.

What Are PCI DSS 4.0 Requirements 6.4.3 and 11.6.1 — And Why Do They Matter?
These two requirements are at the core of PCI DSS 4.0’s client-side security mandate:
Requirement 6.4.3
All scripts authorized to execute on payment pages must be inventoried, have a business justification, and be actively managed.
You must:
- Know what scripts run
- Know why they’re running
- Prevent unauthorized additions
Requirement 11.6.1
Real-time change detection is required to identify unauthorized modifications to payment pages.
This means:
- Monitoring client-side changes continuously
- Flagging script injection or unauthorized activity
- Logging changes for audit evidence
What Should CISOs Look for in a PCI DSS 4.0 Compliance Solution?
At this stage, most CISOs know that PCI DSS 4.0 requires more than backend controls — it demands client-side visibility and real-time monitoring. But not all compliance tools are built to meet those needs.
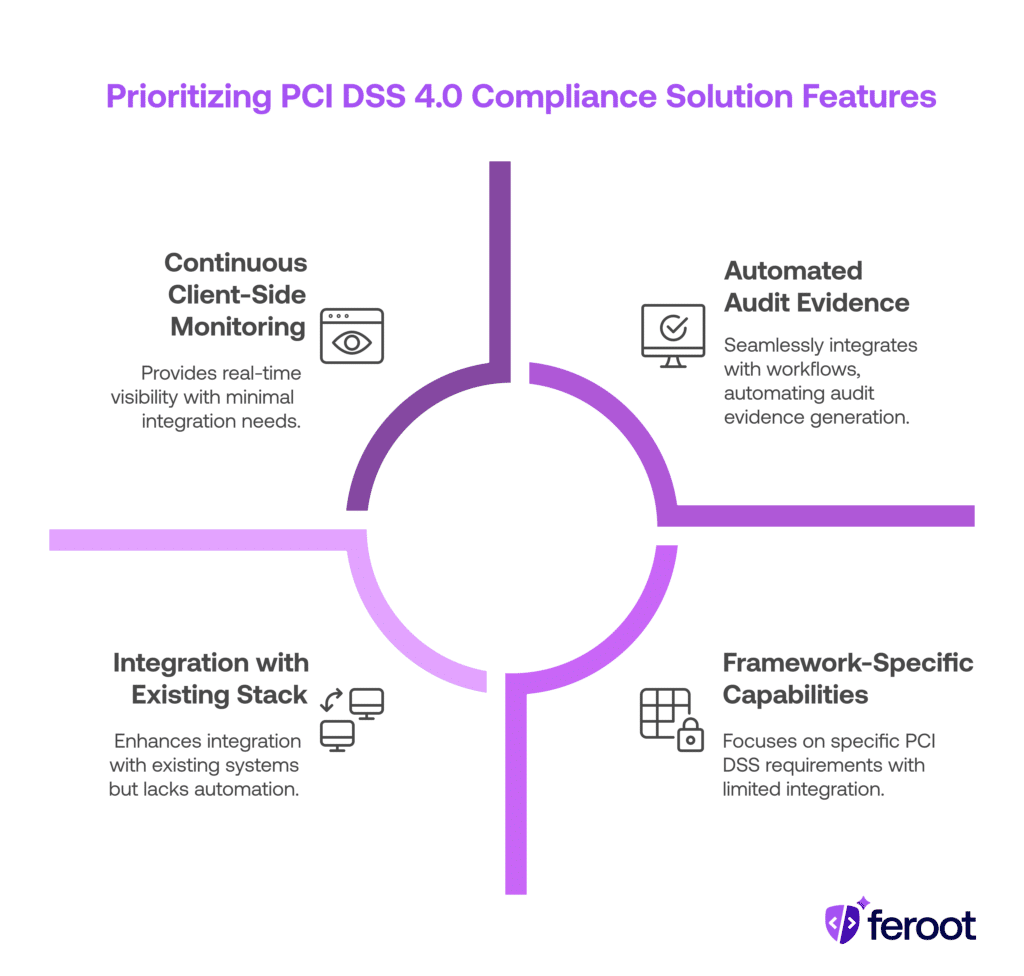
Here’s what to prioritize when comparing solutions:
Framework-Specific Capabilities
Look for tools that explicitly map to Requirements 6.4.3 and 11.6.1 — not generic “compliance dashboards.” The solution should track scripts, justify their purpose, and detect unauthorized changes on payment pages.
Continuous Client-Side Monitoring
Make sure the platform provides real-time visibility into browser behavior, not just static inventories or policy lists. This is critical for detecting live threats and satisfying PCI DSS auditors.
Automated Audit Evidence
The right tool will generate exportable, time-stamped reports that prove control enforcement — reducing your dependency on screenshots, manual reviews, or spreadsheets.
Integration with Your Stack
A scalable solution should plug into your CI/CD, ticketing, and GRC workflows. If it doesn’t work across teams, it won’t work during an audit.
How does Feroot PaymentGuard AI help CISOs automate compliance?
Feroot’s PaymentGuard AI was built to solve these exact challenges. It delivers real-time visibility and control over everything happening in the browser — so your team doesn’t have to do it manually.
With PaymentGuard AI, CISOs can:
- Automatically inventory every script executing on payment pages
- Map each script to a business justification to meet 6.4.3
- Continuously monitor for unauthorized changes or injections (11.6.1)
- Export audit-ready reports for PCI DSS 4.0 evidence
- Integrate with existing workflows (SIEM, GRC, Jira, CI/CD) for scalable compliance
“Feroot automated our PCI compliance process. What took our team weeks now happens automatically. Perfect audit documentation, every time.” — Director of Security, Enterprise E-commerce Platform
What Makes PaymentGuard AI Different from Traditional Compliance Tools?
Most compliance platforms stop at the server, network, or API layer. But PCI DSS 4.0 mandates visibility into what actually happens in the browser — and that’s where traditional tools fall short.
Feroot PaymentGuard AI is purpose-built to close this gap.
Key differentiators:
1. Client-Side Intelligence
Continuously inventories, analyzes, and enforces controls on every script executing in the browser — not just what’s declared in code.
2. Real-Time Change Detection
Meets PCI DSS 4.0 Requirement 11.6.1 by detecting unauthorized changes to payment pages as they happen, not days or weeks later.
3. Inline and Third-Party Script Monitoring
Whether you use embedded forms, iFrames, or redirects, PaymentGuard tracks how third-party code interacts with sensitive elements.
4. Automated Audit Readiness
Generates downloadable reports that map directly to PCI DSS 4.0 Requirements 6.4.3 and 11.6.1 — no screenshots or spreadsheets needed.
5. DevSecOps-Ready Integrations
Works with CI/CD pipelines, Jira, SIEMs, and GRC tools so that security and compliance stay in sync at every stage of the release process.
FAQ
How does compliance automation improve audit outcomes?
Automation ensures that control evidence is always up-to-date, reducing gaps and accelerating audit readiness.
Can Feroot help us qualify for SAQ A under PCI DSS 4.0?
Yes — by monitoring and controlling client-side scripts, Feroot helps you meet the stricter conditions for SAQ A eligibility.
Is Feroot PaymentGuard AI approved by PCI auditors?
While PCI SSC doesn’t “approve” tools, Feroot is used by companies whose audit firms accept its reports as valid control evidence.
What if our Dev team owns the front-end?
Feroot integrates into CI/CD, so AppSec and Dev teams can share control, while Compliance maintains visibility and audit access.
Does Feroot integrate with our existing tools like AWS and Jira?
Yes — PaymentGuard AI integrates with cloud providers, CI pipelines, ticketing systems, and SIEMs for full-stack workflow alignment.
Conclusion
Client-side compliance is no longer optional in PCI DSS 4.0 — especially for payment pages.
With Feroot PaymentGuard AI, CISOs can:
- Automate script monitoring and change detection
- Reduce manual audit prep and evidence collection
- Eliminate blind spots in browser-based environments
- Stay ahead of new PCI DSS 4.0 mandates
Focus on securing your payments — not chasing down rogue scripts.