Introduction
For businesses in the hospitality and travel sectors, PCI compliance is no longer just a technical checkbox—it’s a business-critical priority. Every online reservation, front desk check-in, or mobile booking involves sensitive cardholder data that must be protected.
With the rising frequency of targeted attacks and the complexity of PCI DSS 4.0 requirements, failing to properly implement compliance measures can lead to severe consequences—including legal fines, brand damage, and revenue loss.
This guide outlines how to avoid costly PCI mistakes in hospitality and travel, focusing on client-side vulnerabilities, vendor risks, and modern solutions like Feroot’s client-side security tools.
Why PCI Compliance is Crucial for Travel and Hospitality
The hospitality and travel industries are data-intensive by design. From online bookings and concierge services to on-premise point-of-sale systems, these businesses handle thousands of credit card transactions daily.
Why this matters:
- A single breach can expose sensitive guest information, trigger compliance violations, and erode customer trust.
- Regulatory fines for PCI DSS non-compliance can reach up to $100,000/month.
- The average cost of a hospitality data breach exceeds $3.36 million according to IBM’s 2024 Cost of a Data Breach report.
In a globalized, customer-first industry, even a small vulnerability can have wide-reaching financial and reputational impacts.

5 Common PCI Compliance Mistakes in Hospitality
- Choosing the Wrong SAQ (Self-Assessment Questionnaire): Different SAQs apply to different payment environments (e.g., SAQ A for third-party hosted, SAQ D for full control). Many hotels use the wrong SAQ, exposing them to audit failure.
- Neglecting Client-Side Security: Attackers exploit front-end vulnerabilities with JavaScript skimming attacks that bypass server-side defenses. Most hospitality sites fail to monitor scripts loaded in the guest’s browser.
- Not Monitoring Third-Party Scripts: Websites in this sector frequently use third-party services for live chat, analytics, loyalty programs, or embedded reviews. If these scripts are not audited, they may introduce malicious behavior.
- Improper Data Storage: Storing CVV codes or full card numbers—even when encrypted—violates PCI DSS. This is especially common in legacy hotel systems or custom-built booking platforms.
- Treating Compliance as a One-Time Event: Hotels and travel platforms often treat compliance as a checklist completed once per year. However, PCI DSS 4.0 emphasizes continuous monitoring and proactive risk reduction.
Understanding Client-Side Risks in Travel Payments
Modern travel websites are highly dynamic—filled with personalized content, embedded widgets, and third-party integrations. All of this introduces client-side risk, where the browser environment is left unprotected.
Key Client-Side Threats:
- JavaScript injection altering payment forms
- Skimming credit card data via compromised third-party scripts
- Unauthorized network requests sending data to rogue domains
Client-side monitoring is now a PCI DSS 4.0 requirement, not a nice-to-have.
Vendor Oversight and Third-Party Exposure
Many PCI compliance failures in hospitality don’t originate from internal systems—they come from third-party vendors. These vendors often have direct or indirect access to your payment flows or customer-facing interfaces, which can become conduits for malicious activity if left unchecked.
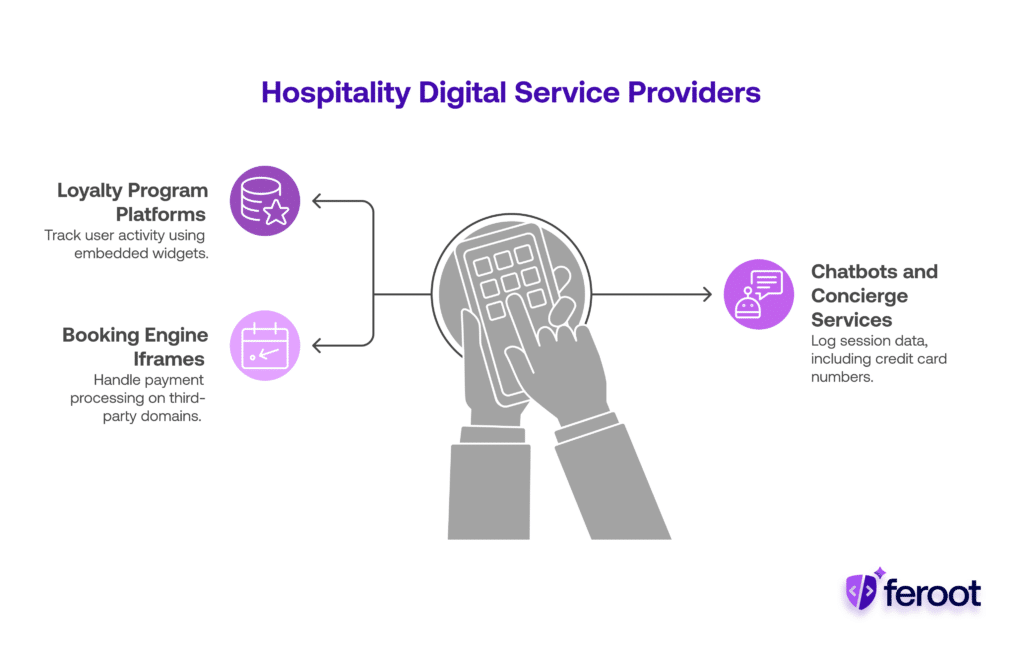
In the hospitality and travel space, businesses rely on a variety of external providers for digital services, including:
- Loyalty program platforms that use embedded widgets or pop-ups to track user activity.
- Chatbots and virtual concierge services that may log session data, including typed credit card numbers or emails.
- Booking engine iframes hosted on third-party domains that handle the actual payment processing interface.
When these integrations are improperly vetted or lack security controls, they introduce invisible risk into the client-side environment. Even reputable providers can inadvertently become vectors for malware if their own code is compromised, as seen in several Magecart-style attacks targeting analytics or review widgets.
Mitigation Steps:
- Perform Regular Vendor Security Audits: Assess the security posture of all third-party providers—especially those with code embedded in your web or mobile platforms. Evaluate whether they’ve passed SOC 2 or PCI DSS assessments.
- Require PCI Compliance Clauses in Contracts: Your contracts should explicitly state that vendors must follow PCI DSS 4.0 requirements and provide evidence upon request. This strengthens your legal protection in case of a breach.
- Continuously Monitor Active Scripts: Use client-side monitoring tools to watch for new or modified scripts introduced by vendors. Set alerts for unauthorized domain calls or data transfers outside of trusted networks.
- Limit Script Permissions via CSP: Use a well-defined Content Security Policy to restrict what external scripts can do in the browser—preventing unauthorized access or data exfiltration.
Best Practices for PCI DSS 4.0 Compliance
Implementing PCI DSS 4.0 goes beyond checkbox compliance—it demands a proactive and layered approach to data security. Below are essential best practices that align with both the letter and spirit of the PCI DSS framework.
- Implement a Content Security Policy (CSP): A robust CSP serves as a browser-level firewall that controls which domains are allowed to execute JavaScript on your site. In the hospitality context, this ensures that only pre-approved vendors (e.g., payment gateways, booking platforms) can run scripts on key pages such as checkout and booking confirmation.
- Tokenize Payment Data: Tokenization replaces real cardholder data with algorithmically generated values that have no exploitable value outside of your system. This reduces data-at-rest risk and significantly simplifies your compliance footprint.
- Deploy Script Behavior Monitoring: Instead of merely approving known scripts, use tools that analyze behavioral patterns—flagging when a script changes behavior (e.g., starts accessing input fields or exfiltrating data).
- Use a Secure Payment Gateway: Look for gateways that support client-side tokenization and allow you to integrate securely without exposing payment fields to your servers.
- Train Staff and Conduct Mock Audits: Your compliance strategy is only as strong as your weakest human link. Many breaches stem from misconfiguration, phishing, or privilege misuse—all preventable with better training.
The most secure environments combine technical controls with organizational awareness—both are required under PCI DSS 4.0.
How Feroot Secures the Client-Side Environment
Modern PCI compliance demands visibility and control where breaches most often begin—in the browser. Feroot’s PaymentGuard AI provides the next generation of client-side protection, purpose-built for ecommerce and web-based payment workflows.
Hospitality and travel websites are particularly vulnerable to client-side threats due to their complex integrations with maps, review plugins, loyalty programs, and chat interfaces. Feroot’s platform secures these layers by:
- Mapping All Active JavaScript: Understand what scripts are running, where they originate, and what data they touch—across every web property.
- Detecting and Blocking Anomalies: Feroot detects unauthorized changes in script behavior, such as accessing guest form fields or connecting to unknown domains.
- Aligning With PCI DSS 4.0: Feroot automates compliance with PCI 6.4.3 (script management) and 11.6.1 (tamper detection), saving your team time during audits.
In 2023, over 40% of ecommerce breaches were tied to client-side attacks. Feroot helps your team stay ahead by addressing a frequently overlooked layer of risk that legacy tools cannot see.
With easy deployment, intuitive dashboards, and real-time alerts, Feroot enables hospitality businesses to protect payment flows, enhance brand trust, and meet evolving compliance demands with confidence.
Conclusion
In hospitality and travel, PCI compliance is not optional—it’s essential to running a secure, legally sound, and guest-trusted business. By identifying common mistakes like improper SAQ selection or ignoring client-side threats, organizations can stay ahead of breaches and avoid costly penalties.


