You only really get to influence your PCI-DSS audit in two places: how you design your controls, and who you let judge them. QSA selection is the second one, and it’s usually underestimated relative to how much it shapes your next 3–5 years.
Under PCI DSS 4.0.1, the assessor’s judgment matters more because several requirements move the discussion into client-side behavior. Scripts, page changes, and third-party components now factor into how compliance is validated. Requirements 6.4.3 and 11.6.1 highlight this shift, and different QSAs read these areas in slightly different ways because the browser surface is dynamic by nature.
What you’ll learn
- How to evaluate QSAs for their understanding of PCI DSS 4.0.1 client-side requirements, especially 6.4.3 and 11.6.1, and why this shapes your next 3-5 years of compliance
- What QSAs actually look for when assessing script management and change detection, including the evidence formats and operational maturity they expect to see
- Which questions expose whether a QSA is comfortable with modern web architectures, automated monitoring tools, and browser-based security controls
- How PaymentGuard AI reduces audit prep effort by up to 95% by generating assessment-ready evidence that maps directly to Requirements 6.4.3 and 11.6.1
The quality of your preparation, the evidence you collect, and even how you narrate your architecture will land very differently depending on which QSA you bring into the room.
What to look for when you’re choosing a QSA
You’re not just buying “QSA services,” you’re buying their worldview on what “good enough” looks like under PCI DSS 4.0.1
Start with industry experience. Ask how they handle your specific patterns like multi-tenant SaaS, heavy use of third-party processors, single-page apps, CDNs, or embedded payment widgets.
Probe their 4.0.1 readiness by going straight to 6.4.3 and 11.6.1. You want to know how do they expect you to detect unauthorized changes to payment pages and scripts, what telemetry do they consider acceptable, and how do they treat client-side controls that are implemented via third-party tools rather than homegrown scripts.
Team composition is another place where expectations can drift. The introductions are often handled by senior staff, but the actual testing may be handed to junior staff who are smart but lack context, leading to inconsistent calls. It helps to understand who will be doing the work and how they keep decisions consistent across reviewers.
Communication style shows up when there’s disagreement. Ask how they handle a situation where you believe a control design meets intent but doesn’t fit their default template; you’re looking for someone who is firm on the standard but willing to engage in evidence-based discussion.
Finally, get painfully specific on evidence expectations. Ask about formats, depth, sampling, screenshots vs logs, architectural diagrams, client-side monitoring exports, and change tickets.
The more aligned you are early, the smoother the review tends to run.
A few red flags are worth calling out. An assessor who hints at an outcome before seeing your environment might be working from assumptions. One who can’t explain how they approach the client-side requirements in 4.0.1 may not be comfortable with those areas. And if modern web architectures feel new to them, the review often becomes harder than it needs to be.
How QSAs understand requirements 6.4.3 and 11.6.1
QSAs know that 6.4.3 and 11.6.1 are where most organizations are weakest because they expose everything that happens after deployment, when changes to the browser surface go unnoticed.
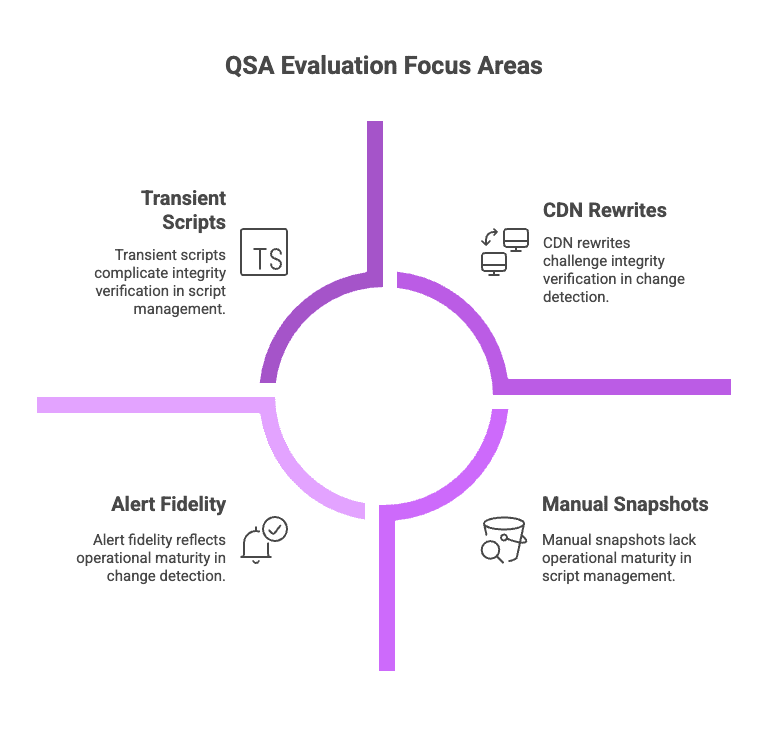
For 6.4.3 (Script Management), QSAs check whether the inventory matches what they see in a live browser inspection, including transient scripts injected by tag managers, A/B testing tools, fraud solutions, and marketing pixels. They look for who approved each script, how long it has existed, and whether you can prove it hasn’t drifted over time.
Integrity verification is another subtle checkpoint. QSAs look for consistent baseline values, visibility into changes to scripts or other assets that load on the payment page, and evidence that verification reflects what runs in end-user browsers, not just what is deployed.
For 11.6.1 (Change Detection), QSAs look for how you detect changes you didn’t make; CDN rewrites, injected error pages, modified headers in adverse network conditions, or scripts added by compromised third parties.
They probe alert fidelity, meaning they want to know how often false positives occur, how noise is triaged, whether alerts map to real incidents, and whether your evidence shows that monitoring runs 24/7, not just during audit month.
QSAs are evaluating operational maturity, not tooling. Manual snapshots fail because they can’t prove continuity. What QSAs really want is the ability to replay history, something most organizations don’t realize until they’re in the audit.
How PaymentGuard AI supports your audit preparation
When a QSA starts probing 6.4.3, the first real test is whether your “script inventory” is a living system or a spreadsheet someone updates before the audit.
PaymentGuard AI effectively turns that into telemetry instead of a document. It automatically discovers every script that executes on your payment pages, including those injected via tag managers, A/B tools, or third-party widgets, and keeps a continuously updated inventory mapped to business purpose and risk.
For 6.4.3, that means you are not manually proving what is running and why. The platform maintains authorization records, tracks changes to each script over time, and links them to justifications that align with PCI language. QSAs can see that only authorized scripts are present, how long they have been in place, and how integrity has been verified, all through a single export from the dashboard.
On 11.6.1, PaymentGuard AI shifts the conversation from “we scan weekly” to “here’s every unauthorized change we would have seen.” It monitors rendered payment pages in real time, detecting DOM-level changes, header modifications, and new or altered assets as they appear in the browser. Events are logged with precise timestamps and can feed into SIEM, Slack, or email, giving you both live alerting and a rich trail of change-detection evidence.
The audit-readiness piece is where it really changes the QSA dynamic. Instead of assembling screenshots and ad-hoc logs, you generate reports that map directly to requirements 6.4.3 and 11.6.1, with script inventories, approvals, and tamper-detection logs already structured in “assessment-ready” form.
Organizations running PaymentGuard AI report drastically lower prep effort (up to 95% reduction) and far less back-and-forth. This way, QSAs get what they need in the first package, which shortens the debate cycle and lets everyone focus on real gaps instead of reconstructing history
Smart questions that help you get to know your QSA
You learn more about a QSA from the questions they struggle to answer than from the materials they send you. These questions help you understand how they interpret newer PCI DSS 4.0 controls and how they work with real evidence in real environments.
Ask your assessor:
- How have you assessed Requirement 6.4.3 with other clients? What evidence did you find most useful?
- What does continuous monitoring mean to you for Requirement 11.6.1?
- If we provide automated evidence reports from a client-side security platform, how does that integrate into your assessment process?
These questions tend to surface two themes. One is experience with client-side controls, which becomes obvious when they describe work they have done with other teams. The other is how comfortably they incorporate automated evidence into their process. If that part feels unfamiliar to them, the assessment may move more slowly.
This clarity helps you choose an assessor who supports a smoother, more predictable engagement.
Choosing a QSA with confidence
Selecting a QSA is one of the most influential choices you make in your PCI DSS journey. It shapes how efficiently issues are resolved, how smoothly evidence is reviewed, and how confidently your team moves through the assessment cycle. The right assessor aligns with your environment and uses your preparation to accelerate the audit, not slow it down.
Now is the time to evaluate how you collect evidence for Requirements 6.4.3 and 11.6.1. If your current process depends on manual reviews or point-in-time snapshots, consider how PaymentGuard AI can automate monitoring, preserve historical proof, and strengthen your QSA relationship from day one.
FAQ
What is a QSA and why does their selection matter so much?
A Qualified Security Assessor (QSA) is a certified professional authorized by the PCI Security Standards Council to conduct PCI DSS compliance audits. Their selection matters because QSAs have interpretive latitude in how they assess requirements, especially the newer client-side controls in PCI DSS 4.0.1. Different QSAs read requirements like 6.4.3 and 11.6.1 in different ways because the browser environment is inherently dynamic. The assessor you choose will shape how smoothly your audit runs, what evidence they accept, and ultimately how you build your compliance program for the next 3-5 years. A good QSA partnership accelerates your audit; a poor match creates friction and extends timelines.
How do I know if a QSA understands modern web architectures and client-side security?
Ask them directly about Requirements 6.4.3 and 11.6.1. How do they expect you to detect unauthorized changes to payment pages and scripts? What telemetry do they consider acceptable? How do they treat client-side controls implemented via third-party tools rather than homegrown scripts? QSAs who are comfortable with these areas will provide specific examples from recent assessments. They’ll understand concepts like tag managers, single-page applications, CDN behavior, and fourth-party script dependencies. If they struggle to articulate how they’ve assessed these requirements with other clients, or if modern web architectures feel unfamiliar to them, the review will likely be more difficult than it needs to be.
What should I ask a QSA during the selection process?
Start with industry-specific experience. Ask how they handle your particular patterns, like multi-tenant SaaS, heavy use of third-party processors, single-page apps, or embedded payment widgets. Probe their PCI DSS 4.0.1 readiness by asking how they’ve assessed Requirements 6.4.3 and 11.6.1 with other clients and what evidence they found most useful. Understand team composition by asking who will actually perform the testing and how they maintain consistency across reviewers. Ask how they handle disagreements when you believe a control design meets intent but doesn’t fit their default template. Finally, get specific about evidence expectations: formats, depth, sampling requirements, screenshots versus logs, and whether they accept automated monitoring exports from platforms like PaymentGuard AI.
What exactly are QSAs looking for when they assess Requirement 6.4.3?
For Requirement 6.4.3 (Script Management), QSAs verify that your script inventory matches what they see during live browser inspection. This includes transient scripts injected by tag managers, A/B testing tools, fraud solutions, and marketing pixels. They look for documented approval for each script, how long it has existed, and whether you can prove it hasn’t drifted over time. They also check integrity verification, looking for consistent baseline values, visibility into changes to scripts or other assets that load on payment pages, and evidence that verification reflects what runs in actual end-user browsers, not just what you deploy to your servers. Organizations using PaymentGuard AI can provide this evidence through a single dashboard export that shows the complete script inventory, authorization records, change history, and integrity verification, all mapped directly to PCI language.
How do QSAs evaluate Requirement 11.6.1 for change detection?
For Requirement 11.6.1 (Change Detection), QSAs focus on how you detect changes you didn’t authorize. This includes CDN rewrites, injected error pages, modified headers in adverse network conditions, or scripts added by compromised third parties. They probe alert fidelity by asking how often false positives occur, how noise is triaged, whether alerts map to real incidents, and whether your evidence shows monitoring runs continuously, not just during audit month. Manual snapshots fail this requirement because they can’t prove continuity. QSAs want the ability to replay history and see exactly when changes occurred. PaymentGuard AI addresses this by monitoring rendered payment pages in real time, detecting DOM-level changes, header modifications, and new or altered assets as they appear in the browser, with precise timestamps and a complete audit trail.
Can I use automated monitoring tools like PaymentGuard AI for my PCI audit, or do QSAs require manual documentation?
Modern QSAs increasingly accept and prefer automated evidence from purpose-built client-side security platforms. PaymentGuard AI generates reports that map directly to Requirements 6.4.3 and 11.6.1, providing script inventories, authorization records, change histories, and tamper-detection logs in assessment-ready format. The key is confirming during QSA selection that they’re comfortable incorporating automated evidence into their process. Ask specifically: “If we provide automated evidence reports from a client-side security platform, how does that integrate into your assessment process?” Organizations running PaymentGuard AI report up to 95% reduction in audit prep effort and far less back-and-forth with QSAs because the evidence arrives structured correctly in the first package. This shifts the conversation from reconstructing history to addressing real gaps.
How much does QSA selection really affect my PCI audit timeline and effort?
QSA selection dramatically affects both timeline and internal effort. An assessor who understands your architecture and accepts automated evidence can cut audit prep time by weeks or months. Organizations working with QSAs experienced in PCI DSS 4.0.1 client-side requirements spend less time explaining their controls and more time demonstrating compliance. When QSAs are comfortable with platforms like PaymentGuard AI, you avoid the cycle of submitting manual documentation, receiving clarification requests, and resubmitting evidence. The right QSA reviews your first evidence package, identifies genuine gaps if any exist, and moves efficiently toward attestation. The wrong QSA may require extensive back-and-forth, request evidence formats that don’t match your tooling, or struggle to interpret how your client-side controls map to requirements.
What’s the difference between how QSAs evaluated PCI compliance before versus under PCI DSS 4.0.1?
Earlier PCI DSS versions focused primarily on server-side controls, network segmentation, and application security. QSAs could validate most requirements by reviewing server logs, firewall rules, and periodic penetration tests. PCI DSS 4.0.1 shifts significant attention to the client side with Requirements 6.4.3 and 11.6.1, which focus on what happens in the customer’s browser after your code deploys. This is where third-party scripts execute, where tag managers inject code, and where Magecart-style attacks occur. QSAs now need to validate that you can inventory, authorize, verify integrity for, and continuously monitor everything that loads on payment pages, including scripts you didn’t write and dependencies you don’t control. This requires different tooling, different evidence formats, and QSAs who understand browser-based security. Organizations relying on traditional server-side security tools often struggle with these requirements.
Should I choose a QSA before or after implementing client-side monitoring tools?
Ideally, implement client-side monitoring like PaymentGuard AI before engaging your QSA. This gives you time to build a complete evidence baseline, establish your monitoring cadence, and ensure your controls are operating continuously before the assessment begins. Starting with monitoring in place demonstrates operational maturity and gives you months of historical data to present. However, if you’re already in the QSA selection process, ask potential assessors how they handle situations where client-side monitoring is implemented mid-engagement. Some QSAs are comfortable with phased implementation if you can show the monitoring covers the full assessment period. Either way, having PaymentGuard AI running before your assessment starts positions you to provide the continuous monitoring evidence that Requirements 6.4.3 and 11.6.1 demand, rather than scrambling to reconstruct evidence manually during the audit.
How do I know if my current evidence collection process will satisfy my QSA’s expectations?
Ask your QSA explicitly about evidence expectations before the assessment begins. Get specific about formats, depth, sampling requirements, and whether they accept automated exports from security platforms. If your current process relies on manual script inventories updated periodically, point-in-time screenshots, or spreadsheets maintained before audits, you likely have gaps. QSAs evaluating Requirements 6.4.3 and 11.6.1 expect continuous monitoring evidence, not reconstructed documentation. They want to see authorization workflows, change detection alerts with timestamps, integrity verification logs, and proof that monitoring ran throughout the assessment period. PaymentGuard AI provides exactly this evidence structure, generating audit-ready reports that include script inventories, approval records, change histories, and tamper-detection logs mapped directly to PCI requirements. Organizations discover these gaps either during QSA selection or during the audit itself. It’s far easier to address them proactively.