TL;DR
- HIPAA Security Rule is getting its first major update in over a decade—introducing mandatory MFA, encryption, asset inventories, and more.
- New requirements of the HIPAA Security Rule will significantly raise cybersecurity expectations for covered entities and business associates alike.
- Healthcare leaders are pushing back, citing budget, staffing, and operational concerns—especially for small or rural providers.
- CISOs must prepare for enforced technical safeguards like penetration testing, formal risk assessments, and incident response drills.
Now is the time to modernize your security stack, including client-side protections many current tools ignore.
What’s in the 2025 HIPAA Security Rule Update?
The Department of Health and Human Services (HHS), through the Office for Civil Rights (OCR), has proposed the first major changes to the HIPAA Security Rule since 2013. These updates to the HIPAA Security Rule—released in January 2025 as a Notice of Proposed Rulemaking (NPRM)—aim to address rising cybersecurity threats across the healthcare sector.
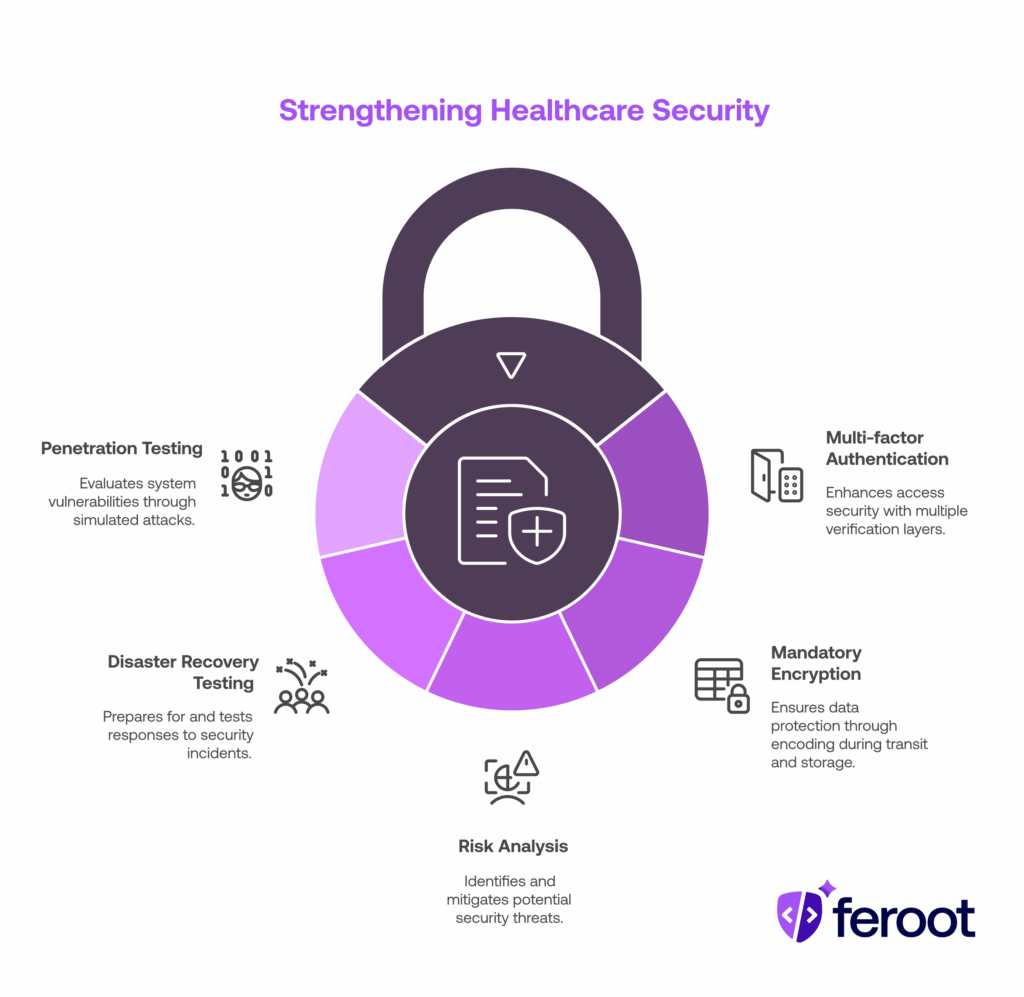
If finalized, the rule would move key technical safeguards from “addressable” to required, including:
- Multi-factor authentication (MFA) for systems accessing ePHI
- Mandatory encryption of ePHI in transit and at rest
- Formal risk analyses based on data-flow mapping and asset inventories
- Disaster recovery testing and tabletop incident response exercises
- Penetration testing and network segmentation
OCR’s goal is to create a modernized baseline that better reflects today’s threat landscape—especially given the surge in ransomware, phishing, and third-party compromise incidents.
Why Are Hospitals and Insurers Pushing Back?
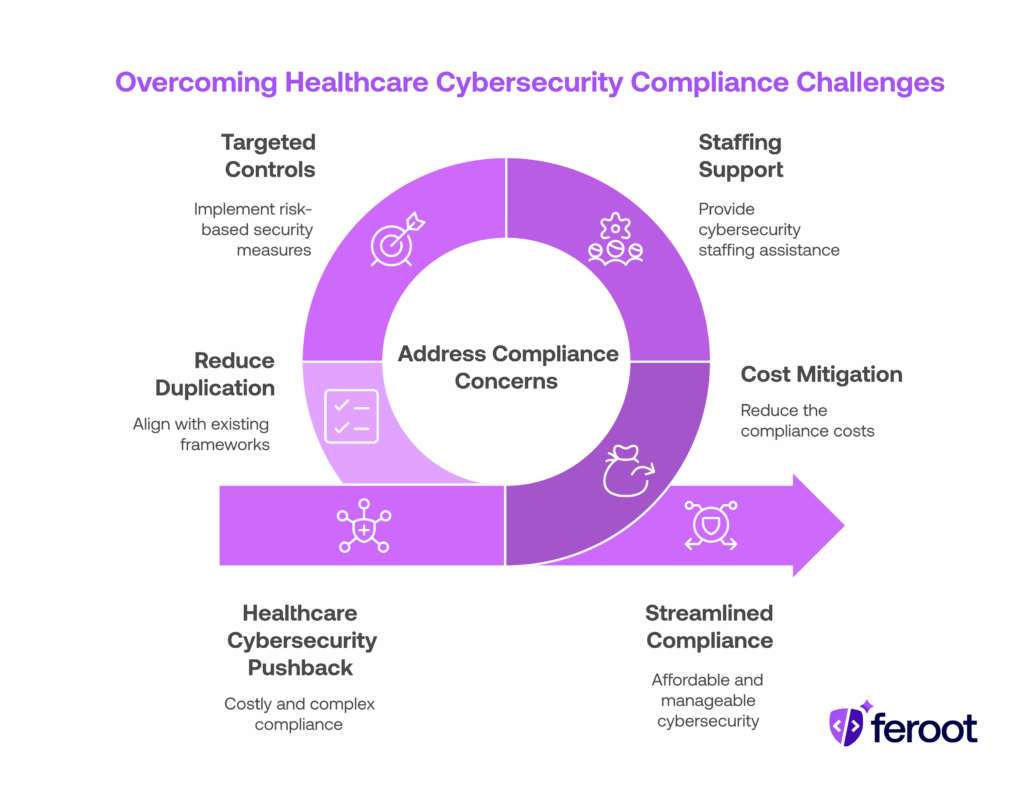
While the HIPAA Security Rule updates are rooted in sound cybersecurity principles, the healthcare industry—especially providers—is pushing back.
In public comments submitted to HHS in July 2025, hospitals, health systems, and insurance organizations raised strong concerns about:
- Cost: An HHS estimate pegged first-year compliance costs at nearly $9 billion across covered entities.
- Staffing: Smaller clinics, rural providers, and non-profit systems say they lack the personnel to handle complex cybersecurity programs.
- Overreach: Critics argue the rules impose “military-grade” controls without financial or technical assistance from the federal government.
- Duplication: Some say requirements duplicate existing obligations under state law or frameworks like NIST or HITRUST.
From a political and operational standpoint, this friction could delay or soften the final rule—but CISOs should not bank on a full rollback. OCR is clear: status quo security practices are no longer enough.
Which Security Controls Are Now Required?
Here’s a breakdown of the most impactful changes CISOs and compliance leaders must prepare for with the upcoming HIPAA Security Rule updates:
| Requirement | Previous status | New status | Action needed |
| Multi-Factor Authentication (MFA) | Addressable | Required | Implement MFA for all ePHI systems |
| Encryption (at rest and in transit) | Addressable | Required | Encrypt all devices, databases, cloud storage |
| Risk Analysis | General | Data-flow-based, detailed | Conduct PHI asset and flow mapping |
| Asset Inventory | Not specified | Mandatory | Maintain real-time inventory of all ePHI systems |
| Penetration Testing | Not required | Required | Perform regular pen tests and fix findings |
| Incident Response Testing | Not required | Required | Run annual IR tabletop exercises |
| Vendor Risk Management | General | Strengthened | Evaluate and document downstream vendor security |
How Can CISOs Prepare For The HIPAA Security Rule Update Without Breaking Their Budget?
Compliance with the proposed HIPAA Security Rule isn’t optional—but that doesn’t mean you need a seven-figure overhaul. CISOs can meet the new cybersecurity mandates by prioritizing automation, continuous visibility, and targeted coverage of overlooked risk surfaces. That’s exactly what Feroot’s HealthData Shield AI is designed to deliver.
1. Start with Inventory and Data Flows — Client-Side Included
Most PHI exposure maps focus on internal systems and cloud services. But HIPAA’s 2025 update specifically calls for full asset inventories and data-flow mapping. That includes:
Scripts and pixels running in patient-facing portals
Third-party tools (like chat, analytics, scheduling widgets)
Shadow code injected by browser extensions or CDNs
Feroot’s HealthData Shield AI:
- Automatically detects and classifies all client-side scripts that touch ePHI
- Maps data destinations and identifies risk-prone third-party services
- Builds a living inventory of your digital front end—no manual effort required
2. Enforce Encryption and Access Controls Across the Stack
Encryption is now mandatory—not optional. But most encryption audits focus on back-end systems. HIPAA-compliant organizations must now prove protections for browser-to-server data flows as well.
Feroot’s HealthData Shield AI:
- Flags scripts transmitting data over non-TLS connections
- Identifies client-side access control violations and misconfigurations
- Provides real-time evidence of HIPAA-compliant script behaviors
3. Detect Threats, Run Audits, and Prepare for Incident Response
The new HIPAA rule mandates routine penetration testing, IR simulations, and continuous monitoring. But traditional GRC tools don’t cover client-side assets—which is where attackers often breach first.
Feroot’s HealthData Shield AI:
- Detects real-time script injections, unauthorized changes, and data exfiltration attempts
- Sends alerts mapped to HIPAA safeguard violations (e.g., 164.312(b): Integrity controls)
- Supplies audit-ready logs and compliance reports without manual review
4. Strengthen Vendor Oversight Without More Headcount
HIPAA’s updates significantly increase the burden on vendor risk management. You’re now accountable not just for business associate agreements (BAAs), but also for downstream data behavior.
Feroot’s HealthData Shield AI:
- Continuously monitors script behavior from vendors (e.g., GA4, Meta Pixel, LiveChat)
- Flags unsanctioned data flows to foreign or unvetted domains
- Documents vendor-side behavior in automated reports aligned to HIPAA requirements
How Does Feroot’s HealthData Shield AI Help Covered Entities Comply with HIPAA Security Rule Changes?
Feroot’s HealthData Shield AI was built specifically for healthcare organizations dealing with PHI exposure at the client side—a blind spot in most compliance strategies.
Why this matters:
- Most web apps, patient portals, and intake forms include third-party scripts
- Those scripts often leak PHI via trackers, analytics, or misconfigured APIs
- OCR’s updated rule now holds entities accountable for all PHI disclosures, even accidental ones
Feroot’s HealthData Shield AI delivers:
- Real-time monitoring of all scripts executing in patient-facing apps
- Automated classification of scripts based on data access, flow, and risk
- Policy enforcement to block high-risk or noncompliant behaviors
- Audit-ready documentation showing compliance with encryption, access control, and transmission security rules
- Seamless integration with your existing compliance workflows—no custom dev work needed
FAQ
What is the timeline for the HIPAA Security Rule update to take effect?
The NPRM was released in January 2025. Final rule publication could occur late 2025, with a 180- to 365-day compliance window.
Are these HIPAA changes legally binding now?
Not yet—they’re still in the rulemaking process. But the direction is clear, and OCR is signaling more aggressive enforcement of current standards in the meantime.
Will these rules apply to business associates too?
Yes. All HIPAA-covered entities and business associates would be expected to comply with the updated requirements.
What happens if we fail to meet the new requirements?
Expect increased OCR audits and fines for noncompliance—especially if a breach reveals that required controls (like MFA or encryption) were missing.
Can we use HITRUST or NIST to satisfy the new HIPAA requirements?
Yes, in part. Many CISOs will map their security stack against NIST or HITRUST CSF, but you must still meet the specific language of the HIPAA Security Rule.
Conclusion
The 2025 HIPAA Security Rule update is a clear signal: cyber complacency is no longer tolerated in healthcare. While the final version of the rule may evolve, the key mandates—MFA, encryption, risk assessments, and vendor oversight—are here to stay.
To stay ahead of both regulators and threat actors, CISOs must:
- Inventory and monitor PHI across all systems (including client-side apps)
- Replace legacy controls with enforced, auditable safeguards
- Strengthen relationships with vendors who support continuous compliance


