TL;DR
- Third-party tracking pixels like Meta Pixel and GA4 have triggered HIPAA violations and lawsuits across U.S. healthcare organizations.
- Even “anonymous” web tracking can expose protected health information (PHI) when tied to user actions.
- Most traditional HIPAA compliance tools overlook client-side risks from JavaScript and browser-based data flows.
- Feroot’s HealthData Shield AI provides real-time visibility and control over third-party scripts to help CISOs secure PHI and prevent breaches.
- Audit-ready reports map client-side risks to HIPAA requirements — no manual evidence gathering required.
Why Are Third-Party Pixels a HIPAA Compliance Risk?
Third-party pixels are snippets of JavaScript embedded on healthcare websites to track user behavior — but they can unintentionally transmit PHI (Protected Health Information) to unauthorized recipients like Meta, Google, and others.
Common pixel-triggered compliance issues include:
- Transmitting PHI without authorization (e.g., appointment scheduling clicks, symptom selections)
- Failing to obtain proper consent for trackers
- Sharing patient identifiers (like IP address + page interaction) with third-party platforms
- Violating HIPAA’s Minimum Necessary and Use/Disclosure standards
Recent lawsuits and regulatory crackdowns (including FTC enforcement and OCR guidance) have made it clear: tracking technologies on healthcare websites can constitute a HIPAA breach.
What Kinds of Patient Data Are Being Exposed Through Web Trackers?
Tracking pixels collect far more than just “marketing analytics.” When embedded in sensitive healthcare contexts, they often transmit:
- Full URLs containing search or query parameters about conditions, medications, or procedures
- Button clicks that indicate health service interest (e.g., “Book Cancer Screening”)
- IP addresses, timestamps, user agents — which may be reasonably linkable to individuals
- Cookies and device IDs that persist across sessions
Example: A patient clicks “Schedule a Mental Health Visit” on a provider’s site with Meta Pixel installed. That click and page URL may be sent to Meta — along with the visitor’s IP address — without a HIPAA-compliant authorization or BAA in place.
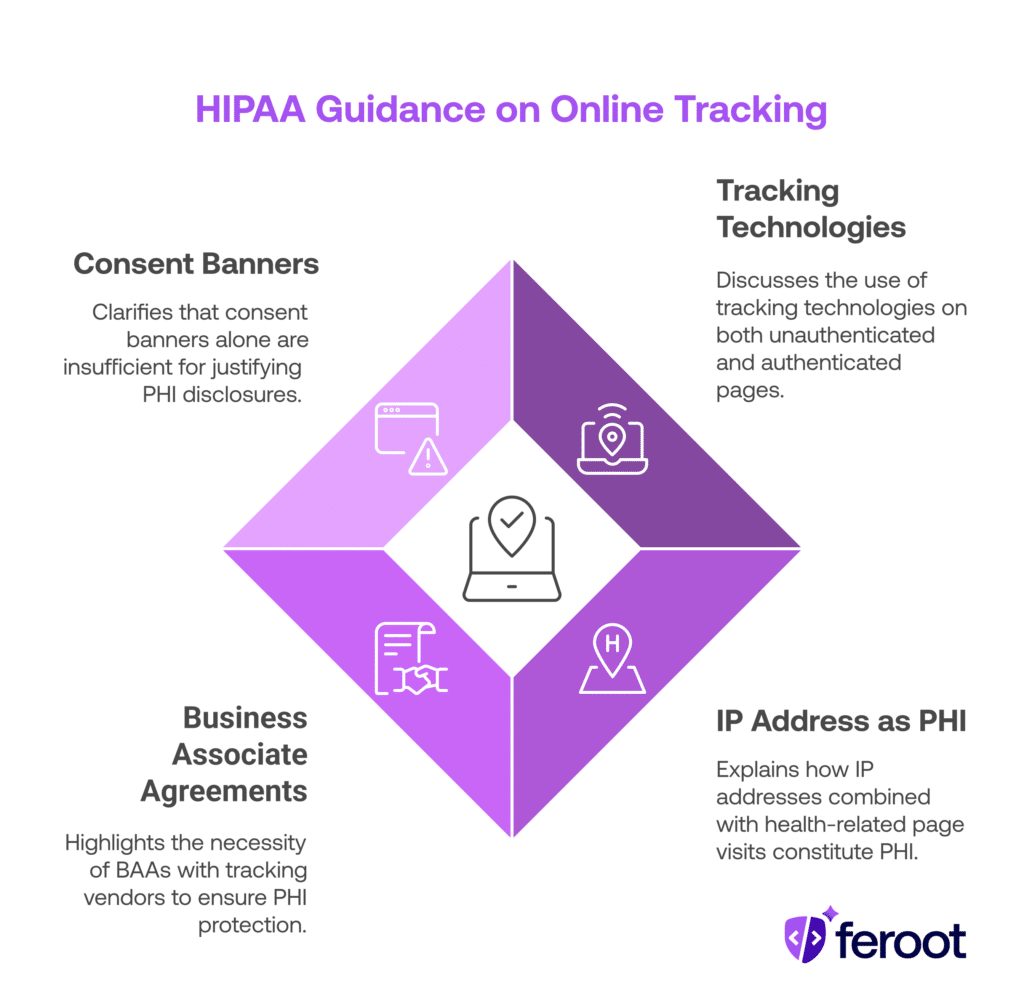
What Does the Latest HIPAA Guidance Say About Online Tracking?
“Regulated entities are not permitted to use tracking technologies in a manner that would result in impermissible disclosures of PHI to tracking technology vendors.”
Key points from the HHS guidance:
- Tracking technologies on unauthenticated and authenticated pages may collect PHI
- IP address + health-related page visit = PHI, even without user login
- A Business Associate Agreement (BAA) must be in place with tracking vendors if PHI is disclosed
- Consent banners are not enough to justify improper PHI disclosures
Why Aren’t Traditional HIPAA Tools Catching These Violations?
Most HIPAA compliance programs focus on backend systems — EHRs, databases, access logs — but client-side risk is a blind spot.
Legacy tools typically miss:
JavaScript behavior in the browser
Third-party script injections via tag managers
Real-time PHI leakage through XHR requests or beacon calls
Shadow code from vendors or marketing teams
Security and compliance leaders are often surprised to learn their website is leaking PHI through:
- Chatbots
- Appointment widgets
- Video embeds
- Analytics scripts
And because these operate on the client-side (in the browser), they often aren’t captured by server-side logging or firewalls.
What’s the Cost of Ignoring Third-Party Pixel Risks Under HIPAA?
Failing to address client-side PHI exposures isn’t just a compliance issue — it’s a high-dollar liability with increasing legal and reputational costs.
The risks include:
- Class-action lawsuits: Major U.S. hospitals and telehealth providers have faced lawsuits for pixel-triggered breaches
- Regulatory fines: OCR and FTC are actively investigating disclosures of PHI through trackers
- Mandatory breach notifications: Exposing PHI can require costly patient notifications and PR responses
- Loss of trust: Patients expect healthcare providers to secure every interaction, including digital ones
Example cases:
- FTC enforcement against BetterHelp and GoodRx for unauthorized sharing of health data with ad platforms
- Multiple hospital systems (including Advocate Aurora, WakeMed, Novant Health) under class-action lawsuits for pixel-related PHI leaks
- Health app developers flagged by HHS for using tracking tools without appropriate safeguards
These aren’t theoretical risks — they’re already happening. And in most cases, executives didn’t even know pixels were active on sensitive web pages.
How Does Feroot’s HealthData Shield AI Help Healthcare Organizations Stay Compliant?
Feroot provides a purpose-built client-side security platform designed to detect, control, and audit browser-based risks — including third-party pixels and script behaviors that put HIPAA compliance at risk.
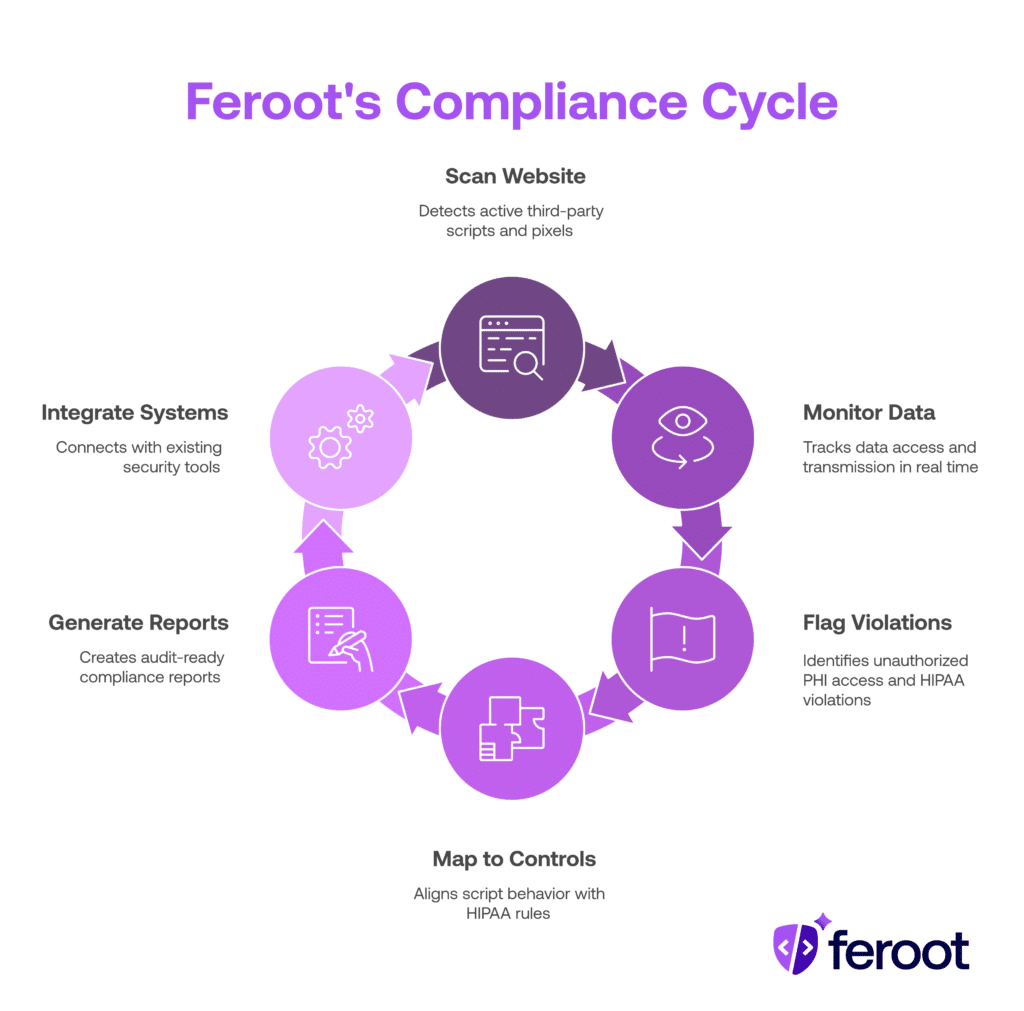
What Feroot does:
- Scans your website and web apps to detect all active third-party scripts and pixels
- Monitors what data those scripts access or transmit in real time
- Flags unauthorized access to PHI and potential HIPAA violations
- Maps pixel and script behavior to HIPAA Privacy and Security Rule controls
- Generates audit-ready reports for compliance and legal teams
- Integrates with existing security stacks (SIEMs, GRC platforms, ticketing systems)
What Results Have Security Teams Seen with Client-Side Protection?
Feroot has helped healthcare and healthtech teams:
- Eliminate unauthorized PHI exposures from Meta Pixel, GA4, and other trackers
- Reduce HIPAA risk assessment timelines from weeks to days
- Pass compliance reviews with auditable evidence of client-side controls
- Avoid costly breach notifications and class-action litigation
FAQ
Can I still use analytics tools under HIPAA?
Yes — but only if you sign a BAA with the provider and configure tools to avoid PHI exposure. Tools like GA4 and Meta Pixel often don’t support HIPAA-compliant use cases.
What’s considered PHI in web activity?
Any combination of data that identifies an individual and relates to their health — including page visits, button clicks, and device metadata — can be PHI.
Do consent banners solve the problem?
No. HIPAA requires authorization, not just consent, for PHI disclosures. Plus, consent alone doesn’t eliminate the need for a BAA.
Is Feroot HIPAA-compliant?
Feroot supports HIPAA compliance by providing visibility and controls that help covered entities prevent impermissible disclosures through web technologies.
What’s the fastest way to check if my site is leaking PHI?
Run a client-side scan with Feroot to detect all active scripts, data flows, and compliance violations.
Conclusion
Third-party pixels are creating HIPAA violations in places few teams expect — the browser. CISOs and compliance leaders can no longer afford to overlook this risk.
Feroot helps healthcare organizations:
- Prevent data leakage at the client side
- Maintain HIPAA compliance across complex tech stacks
- Reduce time and cost of audits and risk assessments
- Protect patient trust in every web interaction