TL;DR
- A zero-day in the Gravity Forms plugin is being exploited to inject malware into WordPress sites
- Attackers use PHP object injection to gain control and plant backdoors
- Thousands of websites may be compromised, with signs of client-side and server-side tampering
- CISOs must act quickly to audit plugin activity and update vulnerable installations
- Feroot helps security teams detect and monitor malicious client-side behaviors in real time
What Happened in the Gravity Forms Breach?
A critical vulnerability in the popular Gravity Forms WordPress plugin has led to widespread malware injections across thousands of sites. The flaw is being actively exploited by threat actors, some of whom are inserting backdoors and malicious JavaScript into WordPress sites to carry out data theft, SEO poisoning, and client-side attacks.
Initial reports link the issue to a PHP object injection vulnerability, which allows attackers to deserialize user-supplied data and execute arbitrary code on the server.
While the exact CVE has not yet been issued (as of mid-July 2025), security firms tracking the campaign say exploitation has been observed in the wild for at least several weeks.
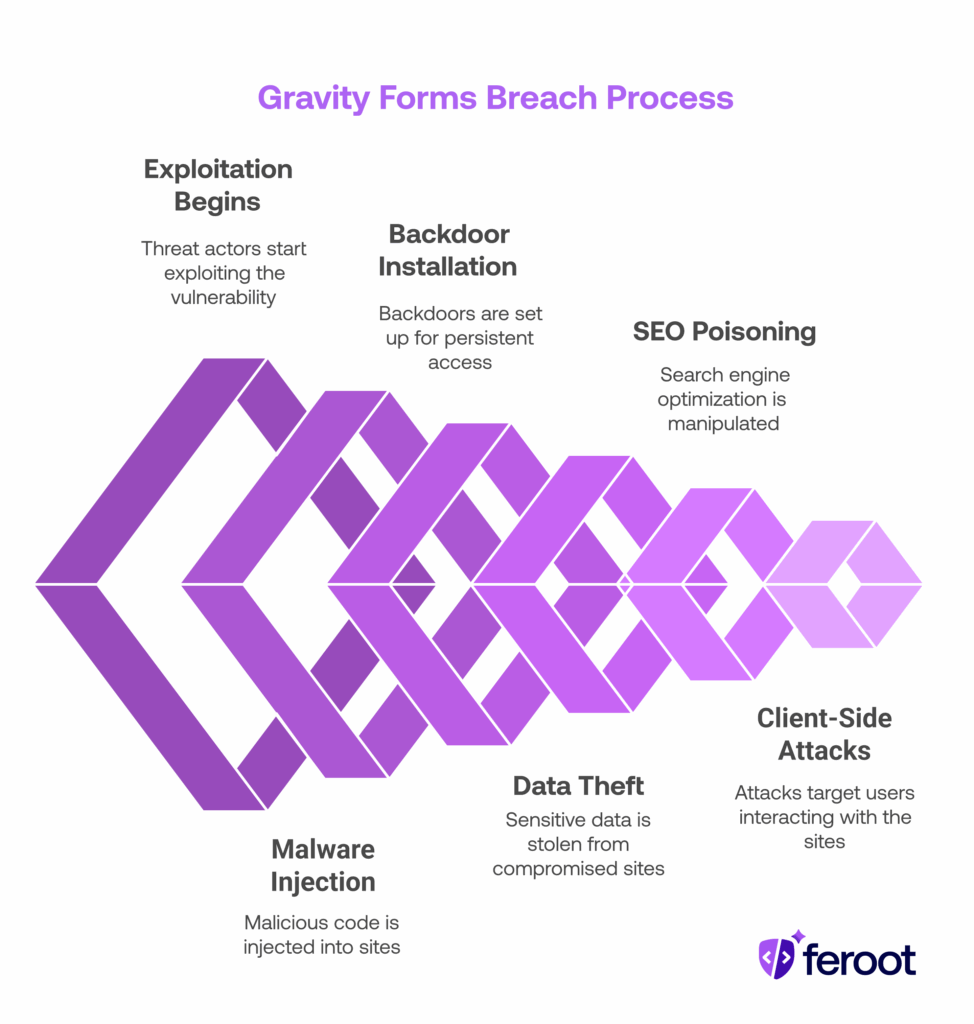
How Are Attackers Exploiting the Plugin Vulnerability?
The Gravity Forms plugin deserialization bug lets unauthenticated users exploit improperly validated form data. Here’s how the typical exploit chain works:
- Step 1: Malicious actors send specially crafted form submissions
- Step 2: The plugin deserializes the payload and executes malicious PHP
- Step 3: Attackers establish persistent access via backdoors or reverse shells
- Step 4: Client-side JavaScript is injected to monitor user input or redirect traffic
Early compromise indicators include:
- New unknown .php files in /wp-content/uploads
- JavaScript loading from unfamiliar third-party domains
- Unexpected redirects on form submission
- Browser-based credential theft (e.g., fake login popups)
What Is PHP Object Injection and Why Is It Dangerous?
PHP Object Injection (POI) is a vulnerability that arises when untrusted user input is unserialized by a PHP application. If exploited, it can allow an attacker to:
- Execute arbitrary code
- Perform SQL injection
- Delete or alter files on the server
- Bypass authentication or authorization mechanisms
In the case of the Gravity Forms breach, attackers abused a POI flaw to inject malicious serialized data via form submissions. Because many WordPress sites run with elevated permissions, this allowed attackers to drop persistent malware and modify form behavior directly in the browser.
Key takeaway for CISOs: Any plugin that unserializes data without validation is a serious risk vector — even if it’s widely trusted or previously secure.
Why WordPress Plugins Are High-Risk Entry Points
With over 59,000 plugins available in the official WordPress repository — and many more from third-party vendors — plugins represent a massive and often unmonitored attack surface.
Common plugin security issues include:
- Poor input validation (e.g., POI, XSS, SQLi)
- Outdated dependencies or libraries
- Lack of regular updates or patching
- Insecure default configurations
- Overprivileged access to file systems and APIs
Even well-maintained plugins like Gravity Forms can become a threat when attackers discover novel ways to exploit them — or when site owners delay updates.
CISO Action Item: Create a plugin risk scoring system and require security reviews or auto-updates for any plugin handling forms, user input, or client-side scripts.
Which Risks Should CISOs Be Prioritizing Right Now?
This is more than just a WordPress issue — it’s a third-party plugin supply chain risk. Security teams should prioritize:
- Plugin inventory review: Identify all WordPress instances using Gravity Forms
- Version audits: Check whether you’re running affected versions (v2.x series)
- Log analysis: Review form submissions and web server logs for injection attempts
- Endpoint monitoring: Inspect client-side behavior via real user monitoring tools
Many of these breaches can remain undetected for weeks — especially when client-side scripts are designed to mimic normal functionality.
How Can Security Teams Detect Malware Injected via Plugins?
Traditional server monitoring will miss browser-level compromises. Here’s what CISOs should implement:
- Real-time script behavior analysis
- Subresource integrity (SRI) validation for third-party scripts
- Alerting for unexpected JavaScript changes on form pages
- Scanning of uploaded assets for PHP shells and obfuscated code
- Cross-checking plugin templates for unauthorized modifications
Look for signs of obfuscation, such as:
- Base64-encoded strings
- eval() or document.write() JavaScript functions
- Hidden iframe injections
- Network calls to unfamiliar domains
How Does Feroot Help CISOs Detect Client-Side Plugin Abuse?
Feroot gives security teams real-time visibility into client-side activity, helping detect and prevent breaches stemming from plugin vulnerabilities like the one in Gravity Forms.
Why client-side monitoring matters:
- Plugin-based attacks often bypass server-side defenses
- Injected scripts can steal session cookies, credentials, and PII
- Most GRC and vulnerability scanners don’t see what’s happening in the browser
What Feroot does:
- Continuously monitors all scripts executed in the browser
- Detects malicious JavaScript changes triggered by plugin exploits
- Flags violations of compliance frameworks like PCI DSS 6.4.3 and 11.6.1
- Maps activity back to plugins and third-party components
- Provides audit-ready logs for incident response and compliance reviews
FAQ
How do I know if my site was affected by the Gravity Forms breach?
Check for unexpected PHP or JavaScript files in your uploads or themes folders. Review server logs for deserialization attempts and user-agent anomalies.
Can a plugin vulnerability like this impact PCI DSS or HIPAA compliance?
Yes. Injected scripts can capture payment data or PHI, violating PCI DSS 4.0 and HIPAA security rule requirements.
Do I need to remove Gravity Forms entirely?
Not necessarily. Update to the patched version once released, and monitor for unauthorized script behavior on any page using forms.
What if my team doesn’t have visibility into client-side threats?
Use a platform like Feroot to detect script changes, behavioral anomalies, and real-time browser-side risk.
Does Feroot integrate with our existing WordPress or DevSecOps stack?
Yes. Feroot integrates with CI/CD pipelines, SIEMs, and other tools to provide complete compliance and security coverage.
Conclusion
The Gravity Forms plugin breach underscores the growing threat of plugin-based supply chain attacks — and how easily they can compromise thousands of websites.
CISOs must expand visibility to the client-side to fully understand and mitigate risks introduced by third-party components like WordPress plugins.
- Reduce dwell time
- Detect browser-side breaches fast
- Maintain compliance with PCI DSS, HIPAA, and more