The hidden tracker problem
Every time someone clicks “accept cookies,” a new layer of risk begins. What appears to be a simple consent interaction can activate dozens of unseen third-party scripts that collect, share, or store user data beyond your control.
For marketers, cookies power analytics and personalization. For privacy and security professionals, they often create compliance gaps and data-security blind spots.
According to the Privado State of Website Privacy report, 75% of leading websites fail to meet GDPR or CPRA requirements. This is not always a case of negligence; it is often a result of limited visibility and fragmented ownership.
What you’ll learn in this article:
- How trackers infiltrate websites
- Detection methods that provide reliable visibility
- Governance models for ongoing control
- Automation strategies that scale compliance
- Why all of this directly affect business performance and trust
Most organizations assume they manage only a few analytics tags. In reality, dozens of additional scripts may be operating silently in the background. Because compliance depends on evidence, not assumption, visibility is the foundation of control.
How Feroot addresses this problem
Feroot’s AlphaPrivacy AI gives you continuous visibility into trackers and cookies across your sites and apps, then enforces the right controls for each location. It adapts to new privacy requirements in the U.S., Europe, the UK, Canada, Australia, and Brazil, so you can prevent unauthorized tracking, prove compliance, and keep pages fast.
Understanding modern web tracking
The evolution of tracking
Cookies were originally designed to improve usability by remembering sessions, carts, or preferences. Over time, tracking technology evolved into a large-scale behavioral data ecosystem.
| Tracking Evolution | Description |
| Device fingerprinting | Identifies users through attributes such as fonts, plugins, or screen resolution. |
| Blurred ownership | Embedded scripts and APIs let third parties function as first parties within your domain. |
| Server-side tracking | Sends user data directly to vendor servers, bypassing browser privacy controls. |
The current tracking ecosystem
Modern tracking cookies do more than record visits. Analytics tools such as Google Analytics collect granular details like scroll depth, mouse movement, and dwell time. Ad networks share unique identifiers across hundreds of data brokers, while social media pixels exchange behavioral data with their parent platforms.
Together, they form a hidden information exchange network that operates beyond most site owners’ direct oversight.
Consent and its cascading effects
When users approve cookies, they often consent to more than they realize. Even one trusted analytics provider can relay data to numerous partners under “legitimate interest.”
This chain reaction, known as a consent cascade, extends user data across multiple vendors, each with its own privacy standards. Without ongoing monitoring, businesses unknowingly delegate personal data control and increase compliance exposure.
A 2023 CNIL study confirmed that many sites transmit analytics and advertising data to third parties even after users reject cookies, demonstrating the complexity of true consent enforcement.
The Google reality you can’t ignore
Why Google dominates tracking
Google cookies reach far beyond analytics. Through Google Tag Manager, a single approved tag can deploy multiple dependent scripts that interact with services like DoubleClick, AdSense, and Firebase.
Internal audits show that one GTM container can create data connections to more than forty external domains, compounding risk and operational complexity.
Managing Google cookies responsibly
Removing Google technologies entirely is nearly impossible. Instead, organizations can focus on responsible governance:
| Practice | Purpose |
| Sandbox GTM | Prevents unapproved tags from being added automatically. |
| Limit data scope | Collect only essential metrics. Disable cross-domain tracking unless required. |
| Monitor new trackers | Use privacy scanners to identify unauthorized domains. |
The objective is not to reject Google tools but to control their scope and ensure accountability.
Detecting what’s really running behind the scenes
Why periodic scans fail
Quarterly privacy audits and surface-level scans often miss real-world conditions. Many trackers activate only after user interaction, specific geolocation, or marketing events.
Examples:
- A video playback script triggers additional analytics requests.
- A regional promotion activates geotargeted trackers.
- A minor GTM update introduces new code dependencies between scans.
As a result, a compliance team may see a clean audit report while hidden trackers remain active.
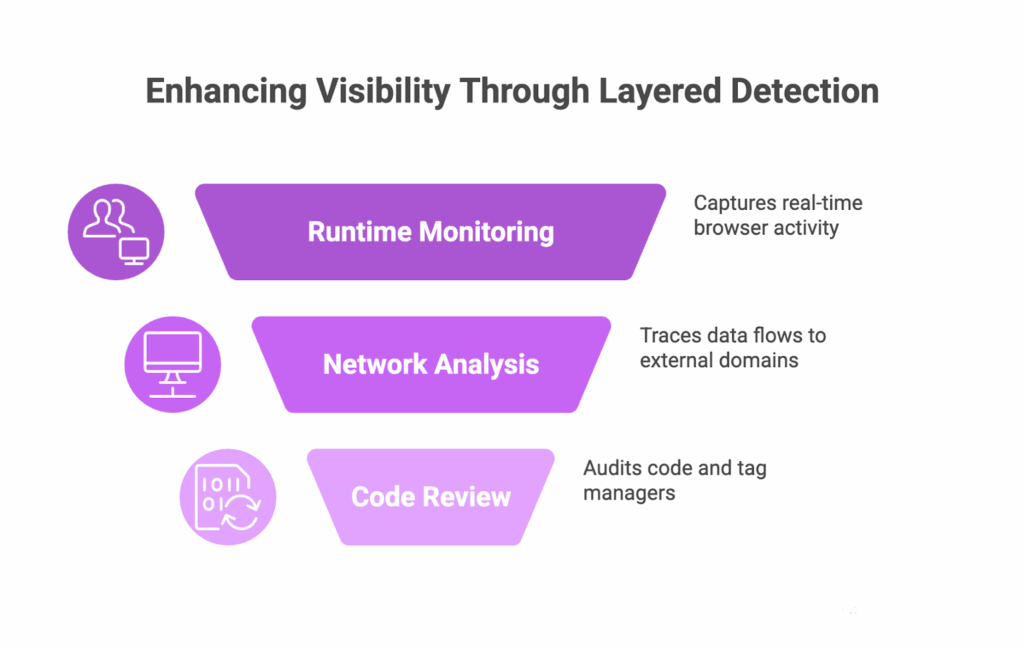
A layered detection strategy
A multi-layered detection approach provides more accurate visibility.
| Detection layer | Method | Value |
| Runtime monitoring | Observe browser activity in real sessions. Captures dynamic and conditional trackers. | Detects real-time behavior and new script injections. |
| Network analysis | Map all outgoing requests to external domains. | Identifies unauthorized data transfers. |
| Code and tag-manager review | Audit GTM containers, dependencies, and libraries. | Reveals embedded or hidden inclusions that bypass runtime tools. |
This layered strategy ensures you understand what is actually happening in your production environment.
From detection to prevention
Strengthening technical controls
Once visibility is established, prevention becomes the priority. Effective technical controls help enforce privacy automatically while maintaining essential site functionality.
| Control | Description | Reference |
| Content Security Policy (CSP) | Deploy in “report-only” mode to identify violations, then enforce allow-lists for approved domains. | OWASP CSP Cheat Sheet |
| Subresource Integrity (SRI) | Ensures that scripts have not been altered or replaced. | MDN Web Docs |
| Automated blocking | Uses tag-manager rules or privacy firewalls to stop unauthorized scripts in real time. | — |
Embedding governance in your workflow
Technical safeguards must align with business processes.
- Implement a script-approval workflow so every new tag is reviewed before deployment.
- Conduct monthly tracker reviews to confirm active scripts match approved inventories.
- Add privacy clauses and right-to-audit terms in vendor contracts.
- Provide regular training so marketing, development, and leadership understand their shared accountability.
When technology and governance are integrated, privacy protection becomes operational, not optional.
The business case for tracker control
Effective management of tracking cookies supports three core outcomes: performance, compliance, and trust.
| Factor | Benefit | Supporting source |
| Performance | Fewer third-party calls reduce page-load time and improve conversions. | WebsiteOptimization.com Study |
| Compliance | Under PCI DSS 6.4.3, unauthorized trackers may constitute a compliance violation. | PCI DSS Documentation |
| Trust | Transparent data handling strengthens customer confidence and brand reputation. | IAPP Privacy Perspectives |
In 2023, Meta was fined €390 million (~$414M USD) by Ireland’s Data Protection Commission for improper cookie practices. Hidden or mismanaged trackers can lead to significant financial and reputational consequences.
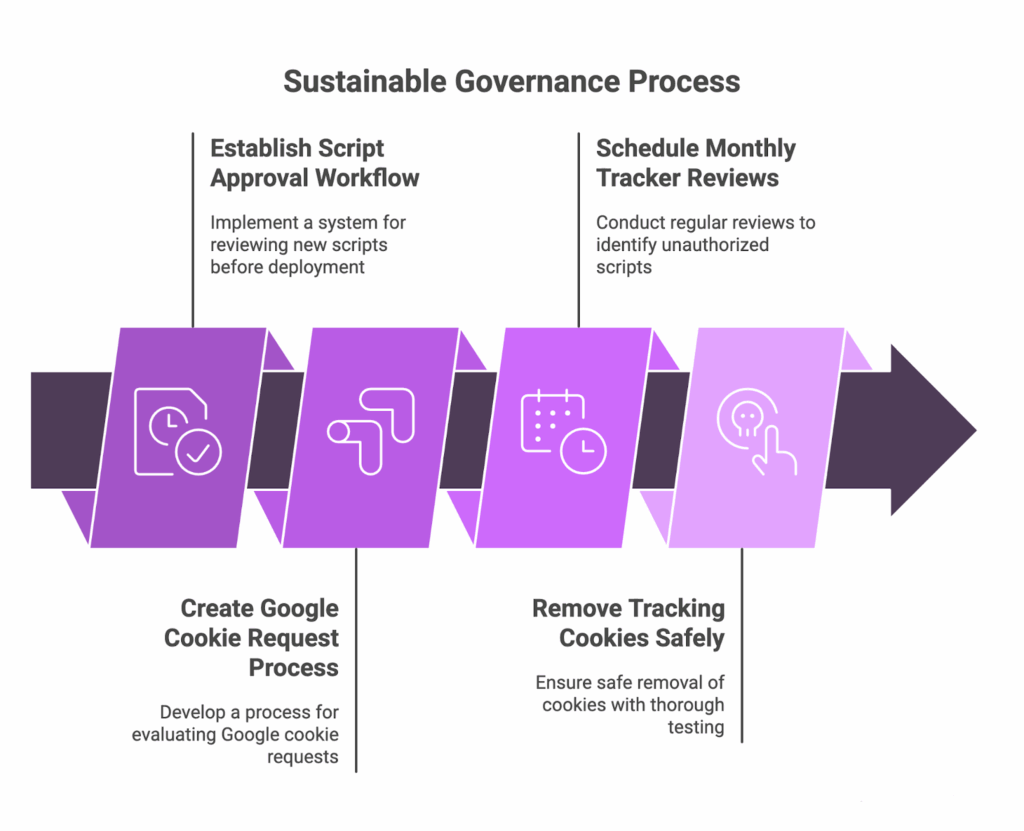
Building sustainable governance
Long-term privacy protection relies on structured governance, not quick fixes. A repeatable framework keeps privacy and security aligned as your business evolves.
| Governance Step | Action | Benefit |
| Script approval workflow | Require all marketing and development teams to submit new tags for review. | Prevents unauthorized scripts from entering production. |
| Dedicated Google-cookie process | Evaluate each use case for purpose, data scope, and risk before approval. | Controls Google’s multi-layered tracking network. |
| Monthly tracker reviews | Hold short, consistent sessions to identify unauthorized scripts. | Keeps tracker inventory current. |
| Safe removal of tracking cookies | Document dependencies, test thoroughly, and monitor post-deployment. | Avoids functionality disruptions. |
Structured governance transforms tracker control from a reactive cleanup exercise into an ongoing operational discipline.
Your 30-day implementation plan
A focused, step-by-step plan helps convert visibility into control.
| Week | Focus | Key actions |
| 1 | Discovery | Inventory all trackers, including Google cookies. |
| 2 | Classification | Risk-rate all tracking cookies, distinguishing essential from unauthorized. |
| 3 | Control | Block or sandbox unapproved trackers while maintaining site functionality. |
| 4 | Monitoring | Enable continuous tracking, alerting, and reporting of new trackers. |
Measure progress using metrics such as detection time, unauthorized-tracker rate, and false-positive ratio. Tracker control is a continuous discipline rather than a one-time task.
Conclusion: Moving from awareness to control
Effective cookie management is not about eliminating every tracker but about ensuring that none operate without authorization. Responsible management of Google cookies, continuous visibility, and structured governance are the foundation of modern website privacy.
When detection, prevention, and governance work together, tracker control becomes part of your client-side security posture rather than a crisis response.
Organizations that continuously monitor and verify their tracking landscape maintain faster websites, stronger compliance, and greater customer trust.